¶ Create a Multi Interface Cyber Gateway
Multi network interface version of Exium’s Cyber Gateway supports Firewall replacement (or overlay) and Zero-Trust Secure Private Access (SPA) use cases.
To create a Multi Interface Cyber Gateway (CGW-MIF), follow the steps below.
- Navigate to the MSP admin console -> Client Workspace
- Click on Gateways in the left menu bar → Add Gateway
- Name - You may change the name of the CGW
- Select Gateway Type as Multi Interface. Fill in the details and add Gateway.
- High Availability (HA) - Please select ‘Yes’ if CGW to be deployed in High Availability mode. 2 Ubuntu VMs or any other 2 quantity of recommended hardware needed for HA setup, Please refer HA user manual for more detailed instructions.
- Admin Notifications Email - Provide email ID which will receive alerts/notifications related to CGW
- LAN Configuration
- If NAT is not required on LAN network then select No for option NAT on LAN, else skip it
- LAN Subnet - Enter LAN subnet (for eg. 10.10.10.0/24). This will be added as Trustpath automatically to Gateway, so no need to add this as Trustpath again. VERY IMPORTANT: This is the subnet that will be behind the gateway (i.e. plugged into the LAN port of the gateway) that you want remote users to be able to access. This is NOT the subnet that the WAN port of the gateway is on. Machines on this subnet will be able to access internet via CGW, if they are configured with default gateway as CGW LAN IP.
- LAN IP - Specify IP address of the Gateway which will be used by the devices behind CGW in LAN subnet specified in above parameter. Configured LAN Gateway IP will be installed on the CGW machine, so make sure it is not conflicting in network or not installed on any other device statically. If HA (High Availability) is enabled, then do not use .251 and .252 IP addresses as LAN Gateway IP. These IP addresses will be installed on Primary and Secondary nodes respectively.
- Next HOP GW for LAN - Provide gateway for LAN traffic. It is required when LAN traffic has to send all traffic to an IP which handles communication with actual core LAN network.
- DHCP Configuration
- Select Yes, if DHCP IP assignment should happen from CGW on LAN network. Please refer DHCP user manual for more detailed instructions.
- If selected Yes, DHCP server will be started for LAN
- Specify Start Range and End Range
- Select Yes, if DHCP IP assignment should happen from CGW on LAN network. Please refer DHCP user manual for more detailed instructions.
- In case of Multiple LAN subnets, click on + symbol and add additional subnets, else SKIP it.
- Enable / Disable DHCP functionality individually on each LAN subnet and set their start and end range
- Enable / Disable DHCP for All LANs
- VLAN Configuration
- Select Yes if CGW needs to support VLAN network segments. Please refer VLAN user manual for more detailed instructions.
- If Yes is selected, please specify VLAN IDs and VLAN subnets.
- Specify VLAN Gateway IP
- Inter VLAN Communication - Select Yes, if inter VLAN communication should be allowed
- Enable/Disable DHCP IP allocation for all VLANs by selecting Yes/No for DHCP for All VLANs option
- You may also enable/disable DHCP IP allocation for individual VLAN by selecting Yes/No for DHCP option
- By default, VLAN DHCP function will use start range .2 to end range .250
- Select Yes if CGW needs to support VLAN network segments. Please refer VLAN user manual for more detailed instructions.
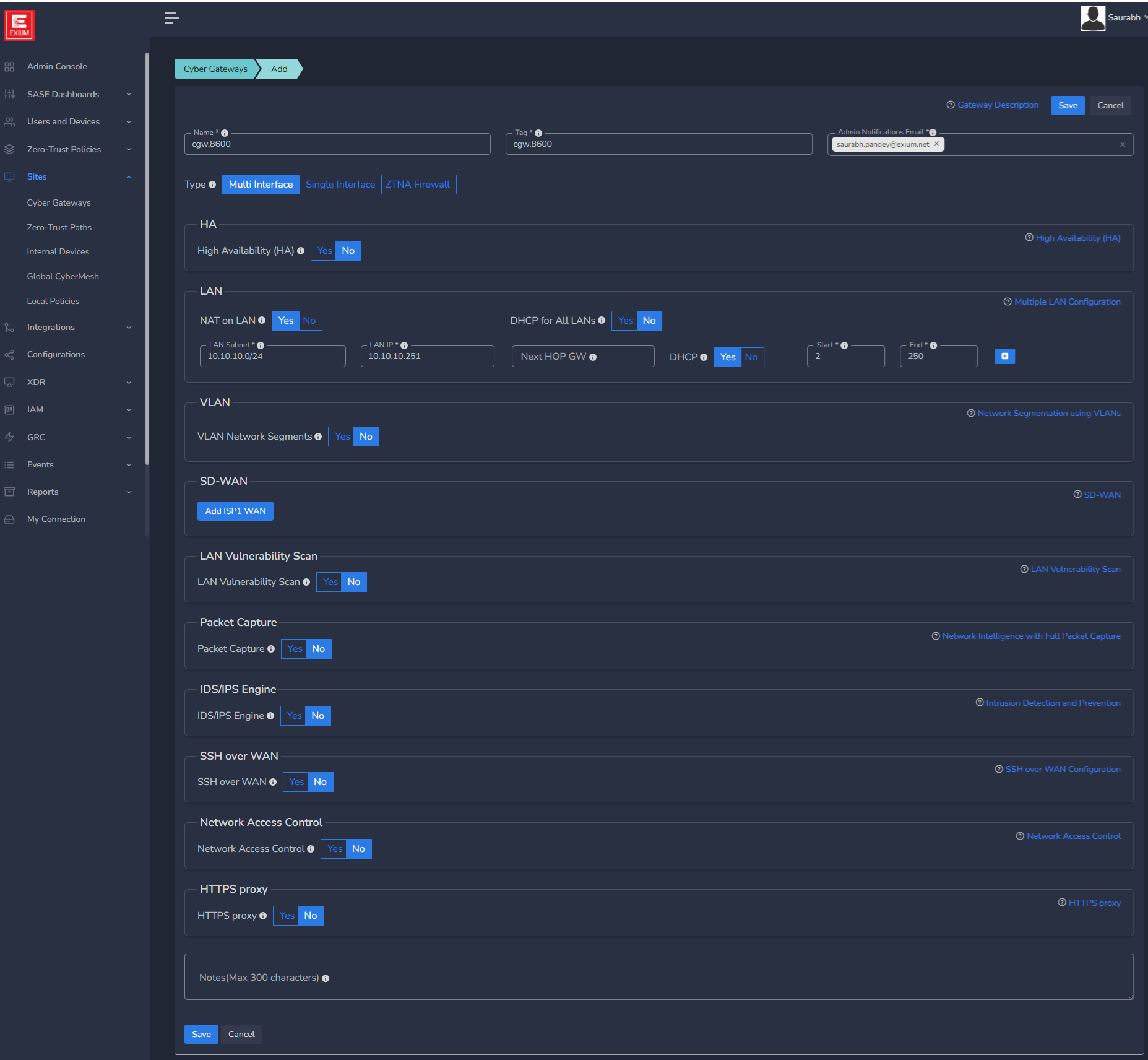
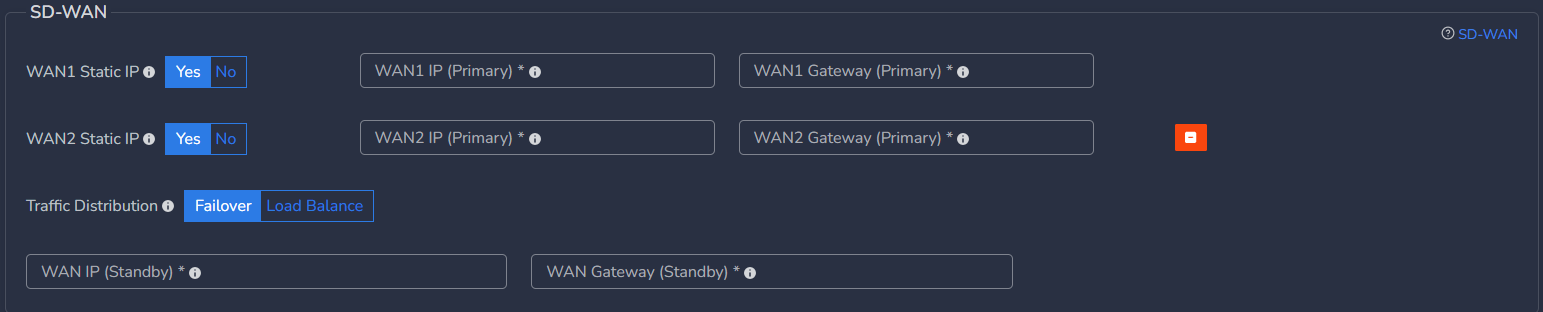
- SD-WAN Configuration
Mostly for CGW deployment on public clouds, you may not need static IPs on WAN interfaces but for specific requirements, it can be added.
- Static IP address along with their default gateway can be configured.
- Mostly it is required when existing Firewalls are replaced with CGW and ISP provided public IP and gateway need to configured on CGW node directly on WAN interface. Please refer SD-WAN user manual for more detailed instructions.
- Click on Add ISP1 WAN
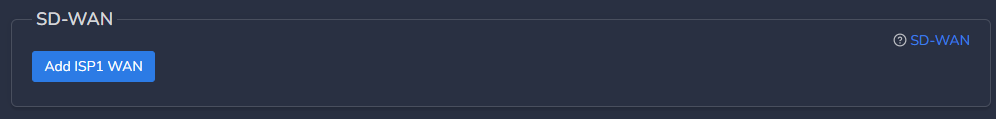
- If WAN1 Static IP is set to Yes, configure below parameters, else skip it.
- WAN1 IP (Primary) - Specify IP with subnet for Primary CGW node
- WAN1 Gateway (Primary) - Specify gateway IP without subnet for Primary CGW node
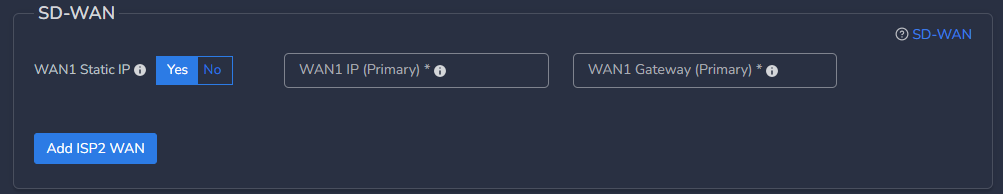
- In case you want to deploy CGW with 2 WAN (WAN1 on ISP1 and WAN2 on ISP2) interfaces then click on Add ISP2 WAN, else skip it
- If selected Yes, you can select Traffic Distribution as Failover or Load Balance
- In case of Failover, only one WAN interface / ISP connection will be active
- In case of Load Balance, both WAN interfaces / ISP connections will be active and in load balance mode
- If Multi WAN is selected with WAN Static IP option, then WAN2 IP (Primary) must be configured with WAN2 gateway (Primary)
- Please refer SD-WAN user manual for more detailed instructions.
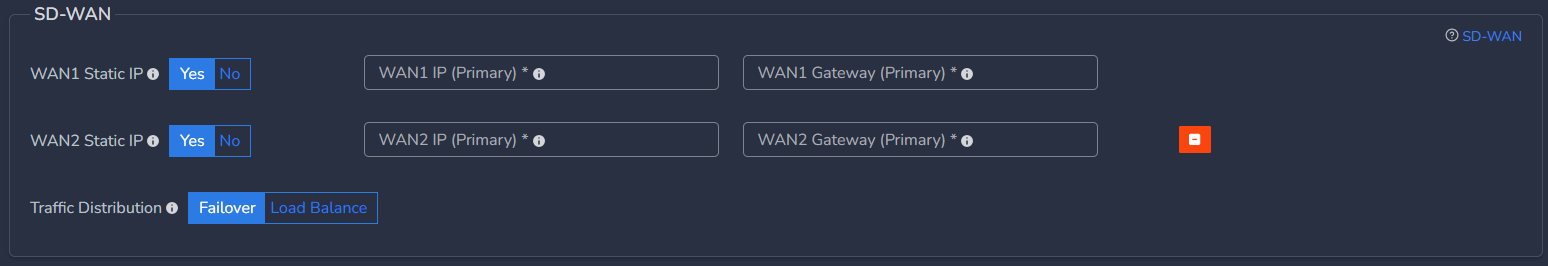
You can configure static IP on WAN1 which is on ISP1 and select No option for WAN2 which is on ISP2 in case ISP2 works on DHCP. In this case, WAN1 will have static IP and WAN2 will get IP allocated from ISP2.
- In case High Availability is enabled, static WAN IP and gateway are required for both nodes
- WAN IP (Standby) - Specify IP with subnet for Secondary CGW node
- WAN Gateway (Standby) - Specify gateway IP without subnet for Secondary CGW node
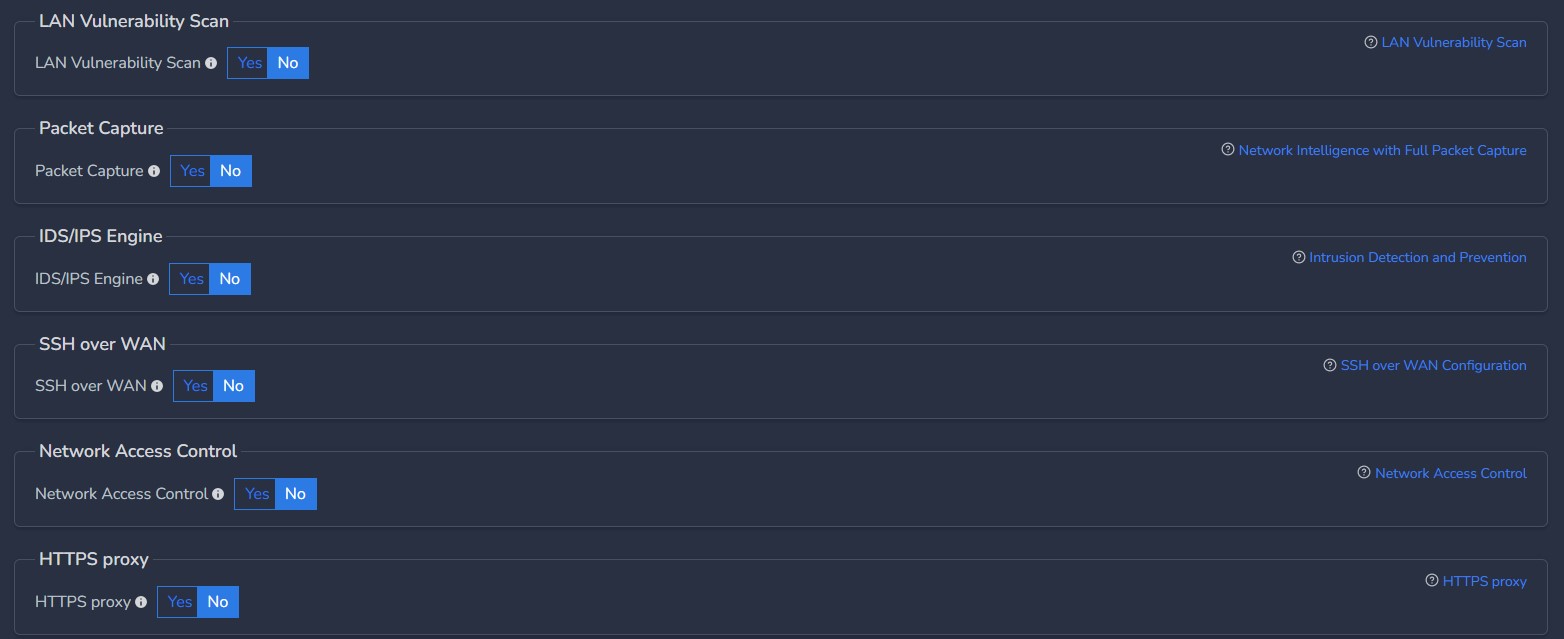
- As per requirements, customer can enable/disable advanced configuration mentioned below.
- Please refer user guides for advanced features for more detailed explanation
¶ Deploy the Cyber Gateway
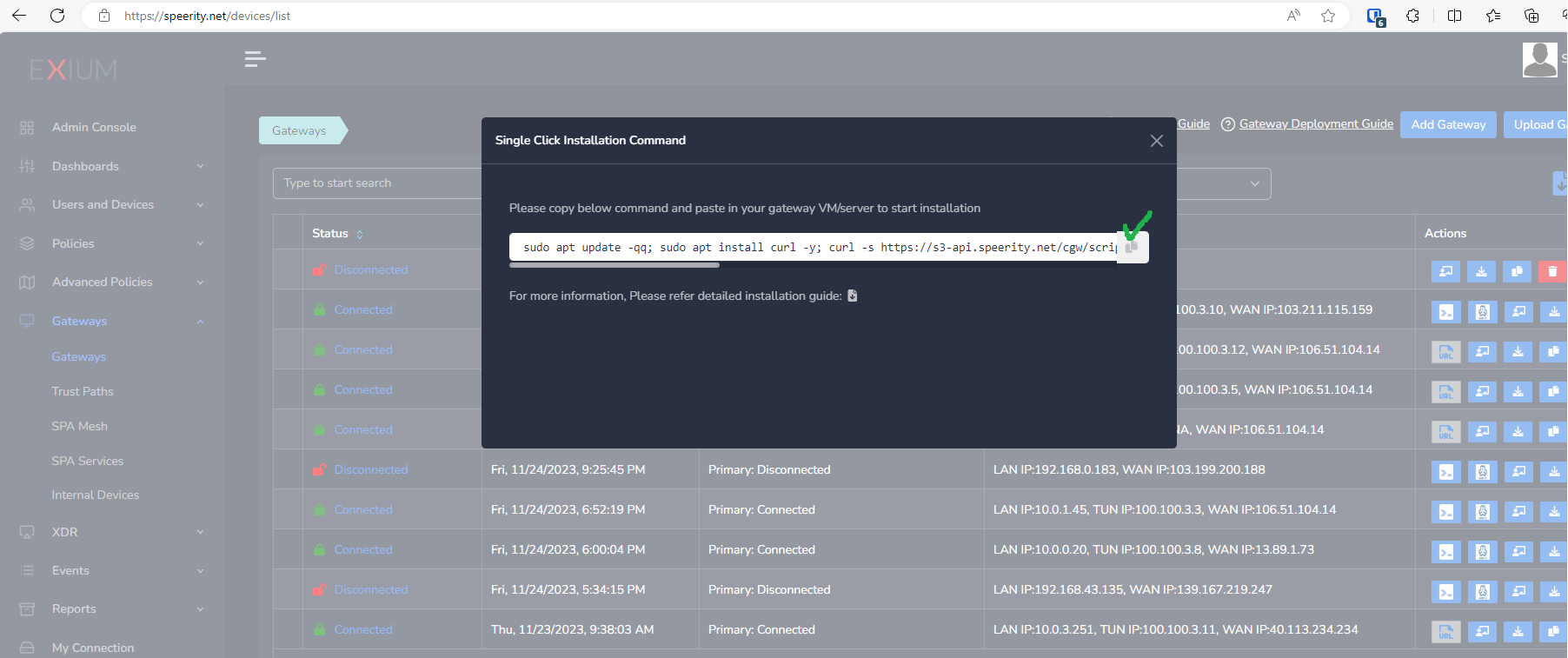
- Copy the Script for the cyber gateway you just created as shown in the screenshot below
- Paste the Script in the VM SSH console
- Press Enter
In case, you are unable to login to machine using SSH to copy and run CGW install command, then we recommend you to run pre-install script mentioned below. You have to type it on console, because copy paste won't work on some direct machine consoles.
bash <(curl -s https://s3-api.speerity.net/cgw/scripts/cgwctl.sh)Please share Workspace and CGW names with us on support@exium.net. We will push installation remotely.
The Cyber gateway deployment will start. At this time, you can leave the deployment running unattended. You will receive an email on the admin email that you specified earlier when the deployment is complete. You can also check the status of the cyber gateway in the Exium admin console. When cyber gateway is deployed successfully and connected, you will see a Green Connected Status as in the screenshot below.
Login to VM or machine
- Type
sudo -sto switch to root - Paste the command copied from admin console in VM or machine
- This will install all necessary packages for CGW. While installation is in progress, you will be asked to select LAN, WAN Interfaces as shown below
- If it is a multi LAN or multi WAN setup, additional inputs will be prompted, please select them to complete the input configuration.
- Post installation, VM will reboot automatically. This is required to make sure all installations come in effect.
- After reboot, please wait ~10 mis for CGW to restart and connect. You can check CGW connection status on admin console
¶ CyberGateway Console or local UI
Please refer to Effortless Cyber Gateway Management for steps to access CyberGateway local web UI or console. Please refer to Credentials section in same document for getting credentials to access DNS Security, Webmin, Cloudshell and docker containers management console.
¶ CybreGateway CLI commands:
Please type cgw help from Linux shell to see all CGW CLI commands

¶ VM and Hardware Recommendations:
Please check out the Modern Security brief for the recommended VM and the hardware for the cyber gateway.
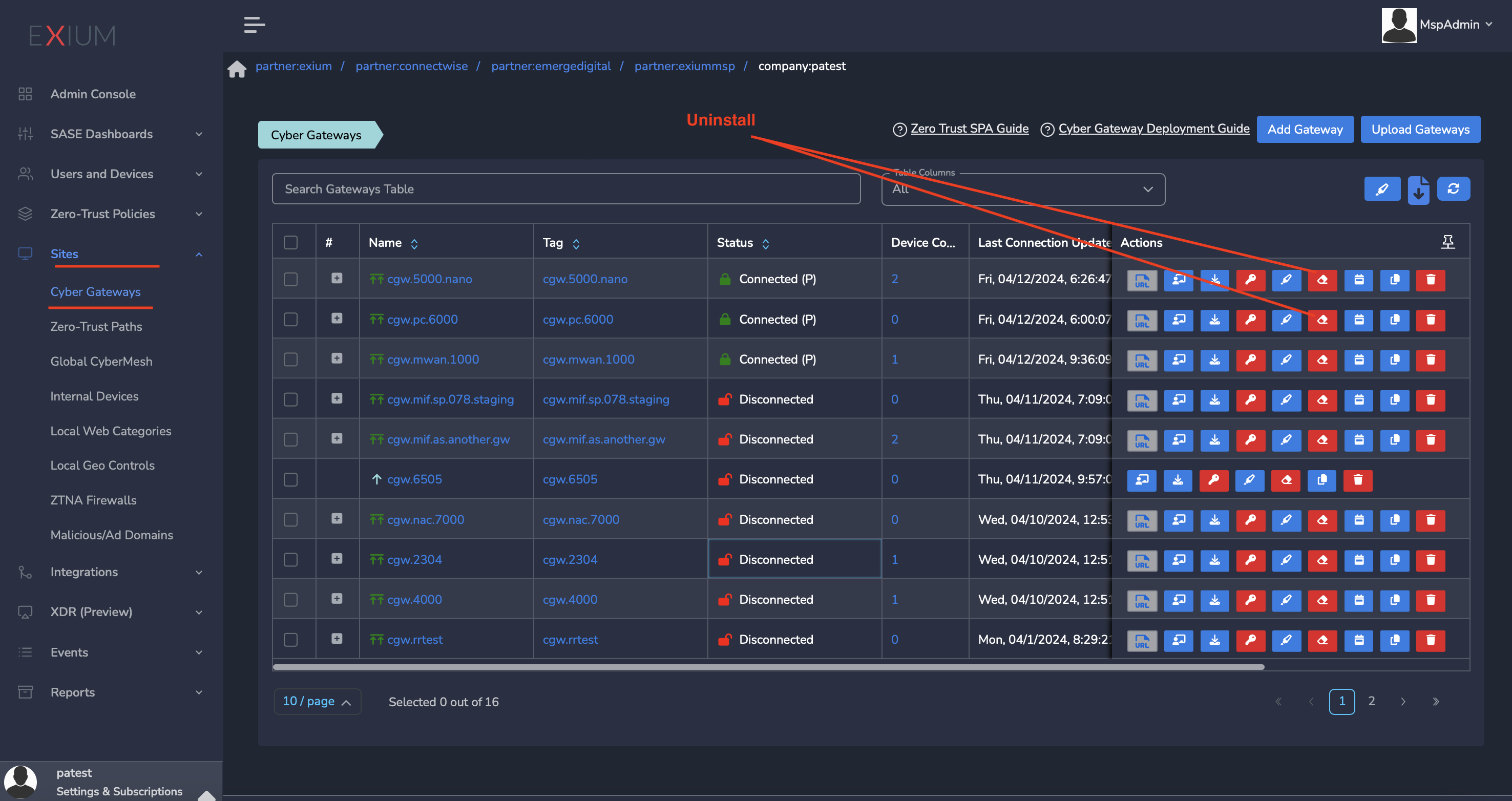
¶ Uninstall CyberGateway
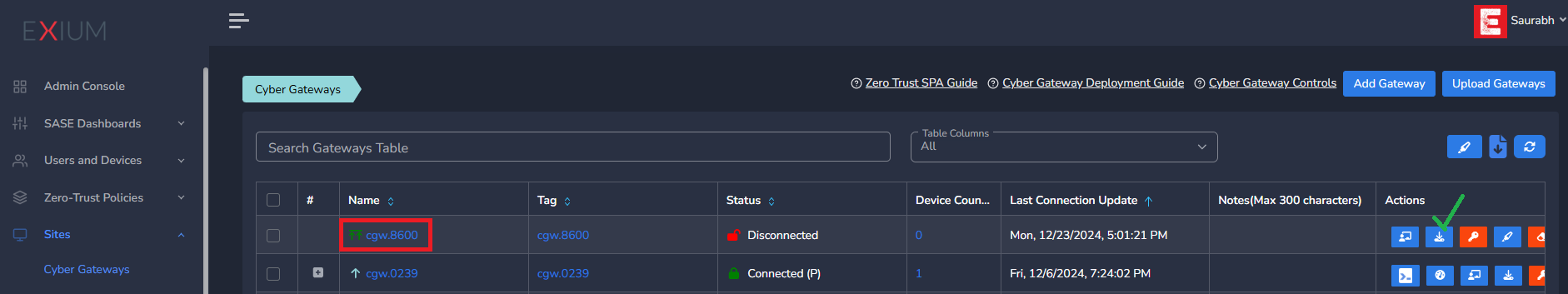
- Navigate to the MSP admin console -> Client Workspace
- Click on Sites → Cyber Gateways in the left menu bar
- Select the CyberGateway you want to uninstall and click on the icon show in screenshot
- It will take around 5 ~10 mins complete uninstallation
¶ Effortless Cyber Gateway Management
Please refer to Effortless Cyber Gateway Management for Exium's centralized control panel for managing Exium SASE Cyber Gateways from a single, intuitive interface.
¶ Conclusion
Experience the power of streamlined Cyber Gateway for seamless connectivity and management with Exium's centralized control panel—where efficiency meets innovation in the fight against cyber threats.
To learn more about implementing SASE and XDR for your organization and explore tailored solutions that meet your unique requirements, contact Exium at partners@exium.net for a consultation or demonstration. If you are ready to get started, check out our testing and onboarding process.