¶ Introduction
In the ever-evolving landscape of network security and management, organizations are increasingly turning to Virtual Local Area Networks (VLANs) to implement network segmentation and device isolation. This document explores the benefits and strategies for utilizing VLANs to enhance security, improve performance, and simplify network administration as well as provide guidelines on configuring network segmentation in Exium's SASE platform.
¶ The Challenge
Networks are susceptible to security threats, performance bottlenecks, and management complexity when they lack segmentation. Traditional flat networks may expose sensitive data and critical systems to unnecessary risks, leading to potential security breaches and operational inefficiencies.
¶ The Solution: Network Segmentation with VLANs
Virtual Local Area Networks (VLANs) offer an effective solution to address these challenges. VLANs enable organizations to logically segment a physical network into multiple isolated virtual networks, each with its own addressing, security policies, and broadcast domains.
¶ Key Benefits of Network Segmentation
Key benefits include:
Enhanced Security: VLANs isolate network traffic, limiting the scope of security threats. This isolation prevents lateral movement by attackers and safeguards sensitive data.
Improved Performance: Segmenting the network isolates broadcast domains, reducing broadcast traffic and enhancing overall network performance. Bandwidth is allocated more effectively.
Simplified Network Management: VLANs facilitate network administration by enabling the assignment of devices to specific logical networks. This streamlines the management of devices, users, and services.
Compliance and Data Privacy: VLANs help organizations meet compliance requirements by separating sensitive data from other network traffic, ensuring data privacy and regulatory adherence.
Scalability: As organizations grow, VLANs can accommodate new devices and users while maintaining isolation and security.
¶ Key Features
Key Features of VLAN-Based Segmentation and Device Isolation inlcude:
- Security Policies: Define access controls, firewall rules, and traffic filtering at the VLAN level.
- Dynamic VLAN Assignment: Automate VLAN assignment based on user roles, device type, or other attributes.
- Quality of Service (QoS): Prioritize and manage network traffic within VLANs to optimize performance for critical applications.
- Inter-VLAN Routing: Control and monitor traffic flow between VLANs with configurable routing.
- Guest Network Isolation: Create separate VLANs for guest access to prevent unauthorized access to sensitive resources.
- Network Monitoring and Reporting: Gain visibility into traffic patterns and security incidents with VLAN-specific monitoring.
Implementing network segmentation and device isolation with VLANs is a strategic move for organizations seeking to enhance security, performance, and network management. This approach allows organizations to fortify their network against security threats, optimize resource allocation, and streamline administrative tasks. By using VLANs effectively, organizations can achieve a more resilient and efficient network infrastructure.
Exium's Cyber gateway offers Zero-Trust network segmentation capabilities that you can easily configure and manage via Exium's centralized admin console.
¶ Configuring VLANs in Exium's SASE Platform
To configure VLANs and implement Zero-Trust network segmentation and device isolation, follow these steps:
¶ Access Client Workspace:
- Navigate to the MSP admin console and select Companies. Click on the name of the company you wish to view (or go directly to the Customer/ Client Workspace Sign In).
¶ Configure Cyber Gateways:
- In the left menu bar, click on Sites and then Cyber Gateways. Choose Add Gateway if you are deploying a new Cyber Gateway.
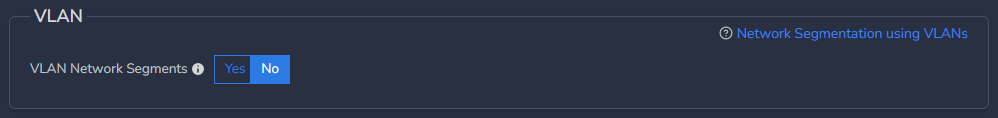
¶ Enable VLAN Network Segments:
- Toggle the VLAN Network Segments switch to Yes to activate this feature.
After enabling, you can start putting inputs for VLAN ID, Subnet, Gateway IP.
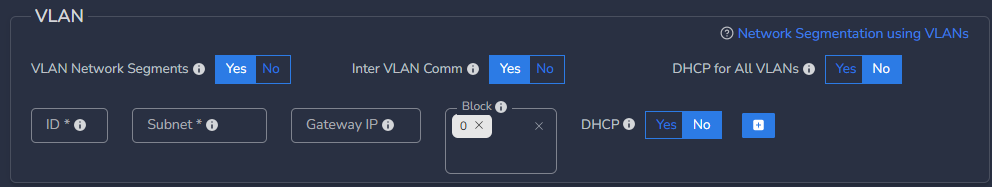
¶ Input VLAN ID:
- Enter the VLAN ID. A default subnet will be created automatically for each ID, although you have the option to modify it if needed.
¶ Add Additional VLANs:
- Add more VLANs by clicking the “+” sign on the right side of the top row.
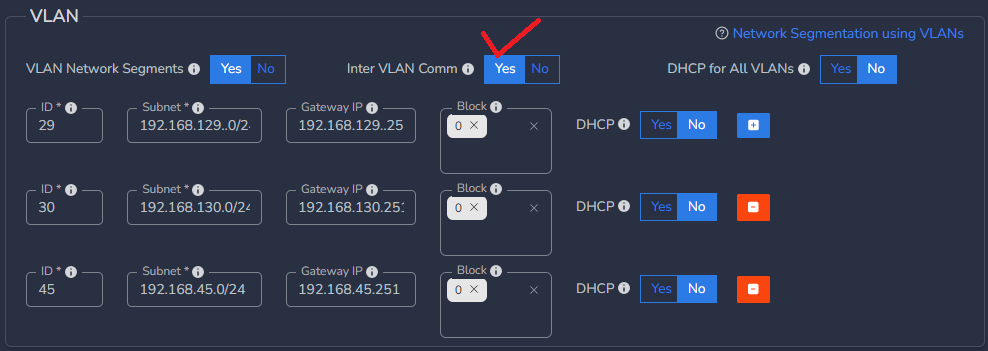
¶ Set Inter VLAN Communication:
- Decide whether to enable or disable communication between VLANs by selecting Yes or No.
- Toggle the Inter VLAN Comm button Yes to allow communication among VLANs or select No to block communication.
¶ Configure DHCP Settings:
- Enable or disable DHCP for all VLANs, or choose specific VLANs by setting the DHCP option to Yes. Specify DHCP pool ranges by defining the Start and End IPs.
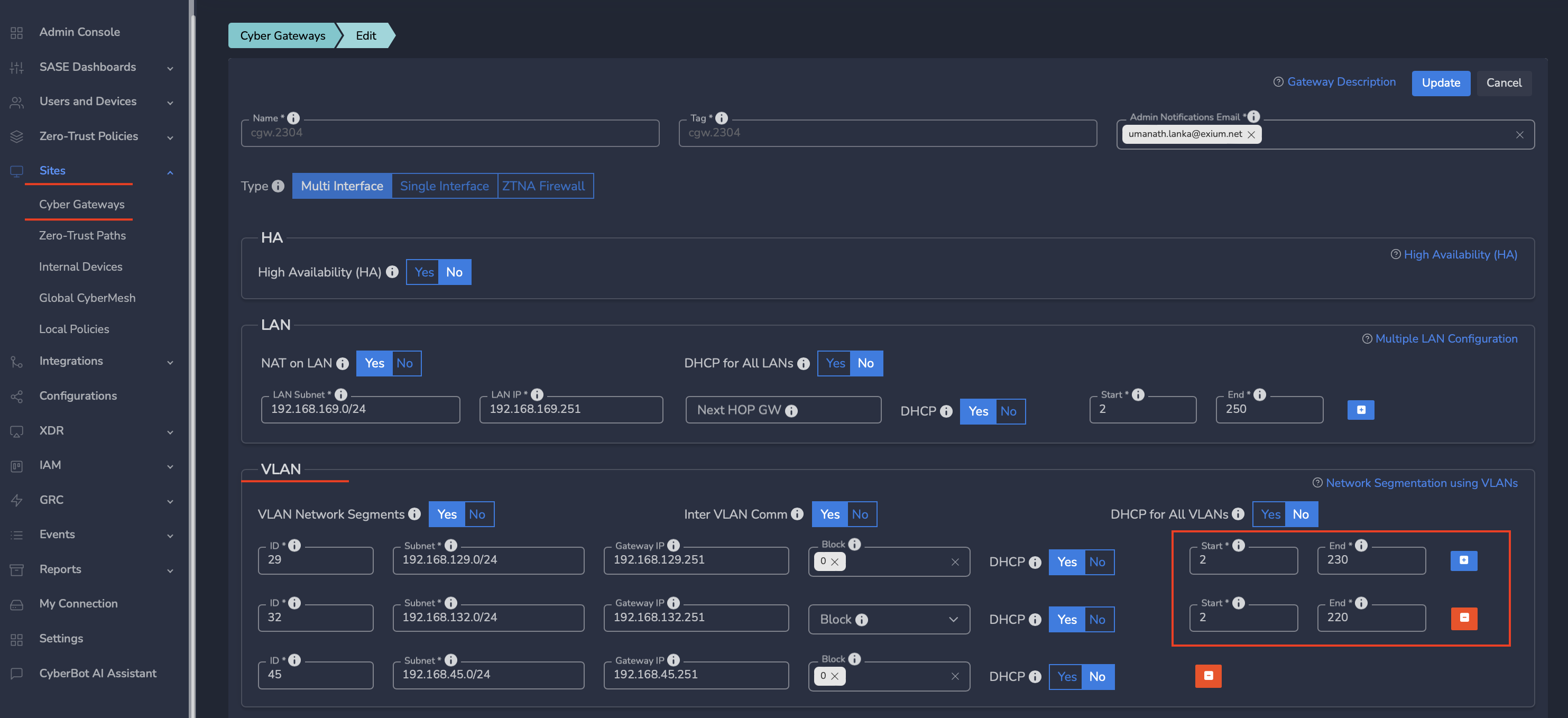
¶ Block Access Between VLANs:
- If you wish to block access between or among VLANs, configure the Block Access setting.
- Disable Inter VLAN communication if there should be no communication between VLANs.
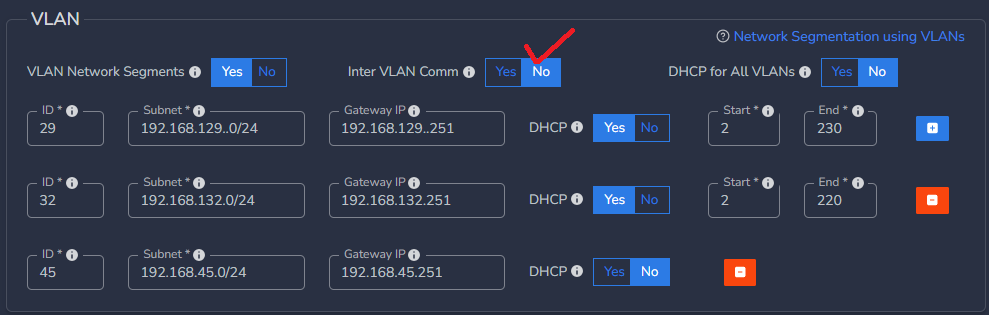
- If you wish to grant access between or among VLANs, switch Inter VLAN Comm to Yes.
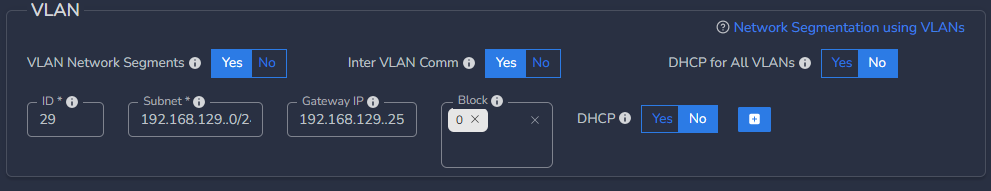
- Click on the Block box and select the VLAN ID(s) from list.
- If you want to block communication to LAN, select 0
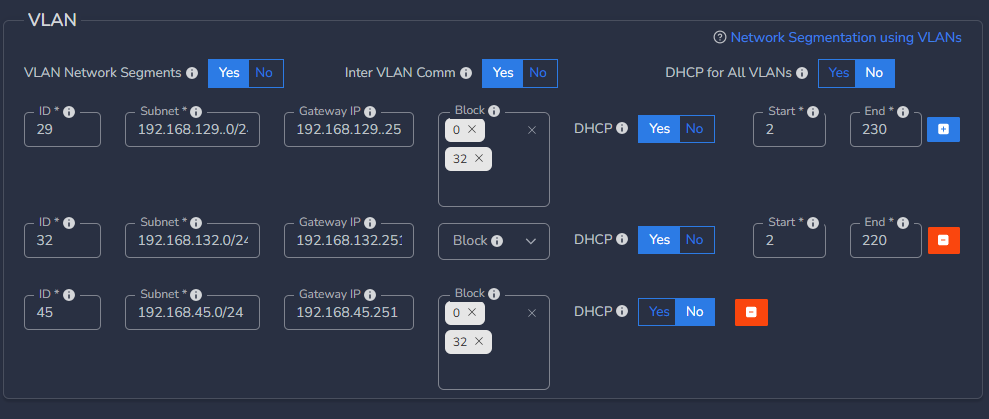
For example, above configuration will enforce below rules:
- No communication from VLAN ID 29 to LAN subnet and VLAN 32 subnet
- VLAN ID 32 can communicate to both VLANs 29 and 45 and also LAN subnet
- No communication from VLAN ID 45 to LAN subnet and VLAN 32 subnet
Currently, policies and firewall rules do not operate at the VLAN level in this version.
- If inter-VLAN communication is disabled, traffic between VLANs is fully blocked and cannot be allowed through firewall rules.
- If inter-VLAN communication is enabled, traffic between VLANs is fully allowed.
Granular, per-VLAN policy control is on our product roadmap, and it will be available by 1Q, 2026.
¶ Save Configuration:
- After entering all VLAN IDs and configurations, click Save to apply the settings.
By following these steps, you can effectively configure VLANs in Exium's SASE platform for secure network management and device isolation. Continue to Multiple interface CGW deployment.
¶ Testing VLANs in the Cyber Gateway
We recommend testing with a switch that supports IEEE 802.1Q VLAN tags. However, some initial testing can also be done using, for example, a windows machine with direct Ethernet cable plugged between the machine and the LAN interface of the cyber gateway as shown in the figure below.
To learn how to configure VLANs for Hyper-V on a Windows machine, click here for details.
Multiple VMs on a single machine or multiple machines can be used for VLAN testing via a Switch supporting IEEE 802.1Q VLAN tags as shown in the Figure below.