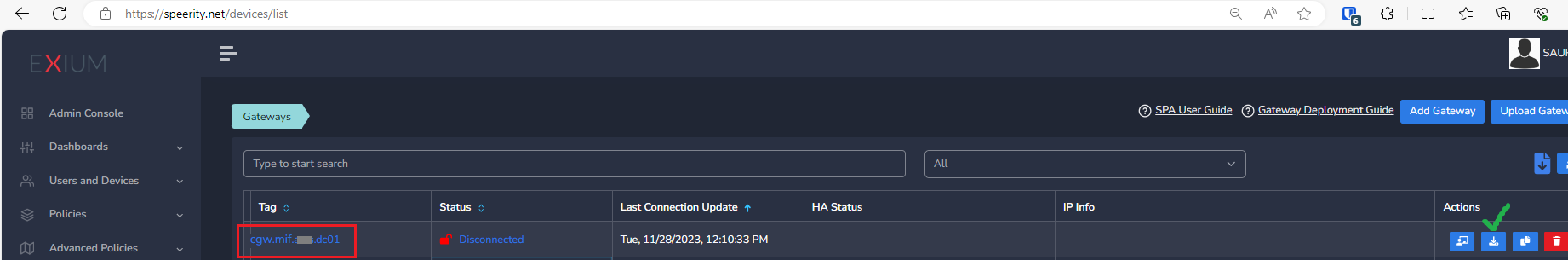
¶ CGW-MIF VM Deployment on Azure
This document describes CGW deployment on 2 interface setup where WAN and LAN interfaces need to be on different subnets. 2 interface CGW deployment handles the cases where LAN subnet or private resources do not have direct public/internet access.
Please refer CGW deployment guide to understand single/dual interface solutions.
¶ Pre-requisites
- Privileged login and subscription on Azure portal to create VMs, networks, subnets and route tables.
- Choose the size or flavor of the VM as per your bandwidth requirement.
| Azure VM Type |
OS |
CPU |
RAM |
HDD |
Bandwidth on Azure |
|---|---|---|---|---|---|
| DS1_v2 |
or Ubuntu 24.04 |
1 vCPU |
3.5 GB |
Standard with size > 30GB |
Up to ~700Mbps |
- Check Azure documentation here, to understand size/flavor of the VM and how much bandwidth it can support
- For higher bandwidth, Accelerated Networking must be enabled on VM's vNICs post deployment
- Network Interfaces: 2 (WAN and LAN)
- WAN on subnet1 – Connectivity to Internet (Default gateway pointing to WAN subnet gateway)
- LAN on subnet2 – Connectivity to private resources
- Refer document Firewall ports to get the list of ports for whitelisting, in case Firewall is present on Azure before CGW VM
¶ Create Network
You can skip virtual network or subnet creation, if you would like to use existing network or subnets.
- WAN subnet creation example shown below:
- Navigate to Home -> Virtual networks
- To create new, click on “create”
- Select Subscription and Resource group
- Provide Virtual network name
- Select Region, where CGW VM is being deployed
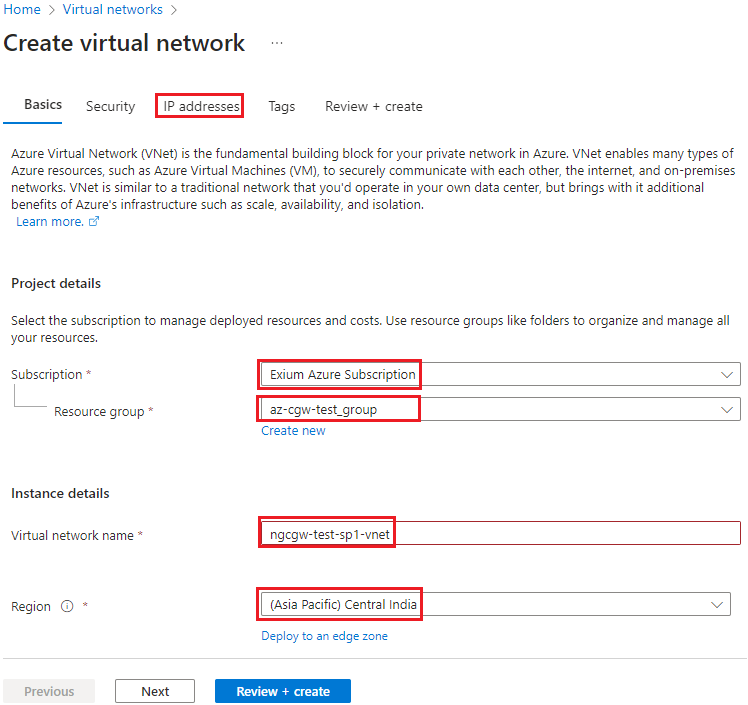
- Click on IP addresses
- Default values will be displayed, which user can modify if required.
- It will also create default subnet with IP range
- For eg. - In below sample, it shows 10.19.0.0/16 is superset of subnet which is available to create smaller subnets
- Subnet with name “default” has range 10.19.0.0/24 (WAN subnet)
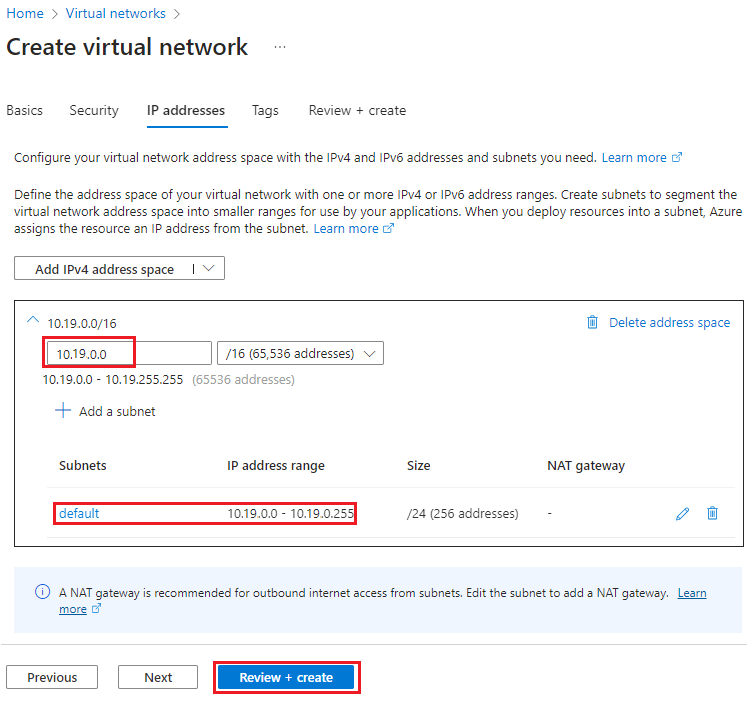
- Click on Review and create
- Verify all the details and click on Create
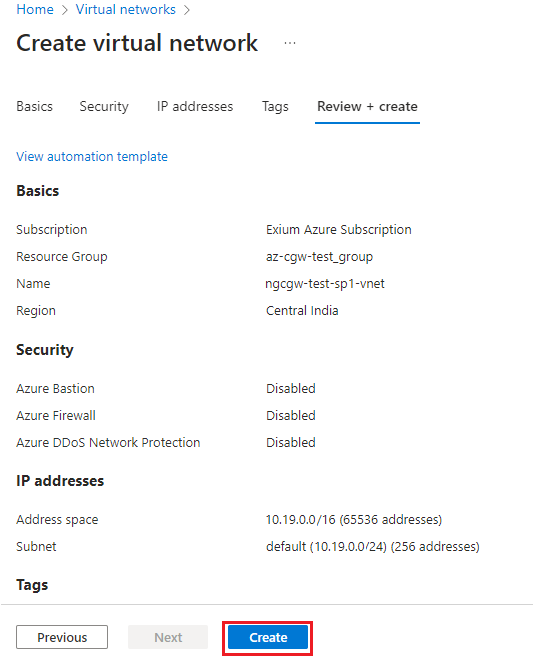
- Virtual network will be created successfully
¶ Create Subnets
- LAN subnet creation example show below:
- Navigate to Home -> Virtual networks

- Select the vnet created on previous step or user can select the existing vnet which is identified for CGW deployment.

- Select Subnets
- Default subnet will be present with an IP address range (In previous section, new separate WAN subnet was created with range 10.19.0.0/24)
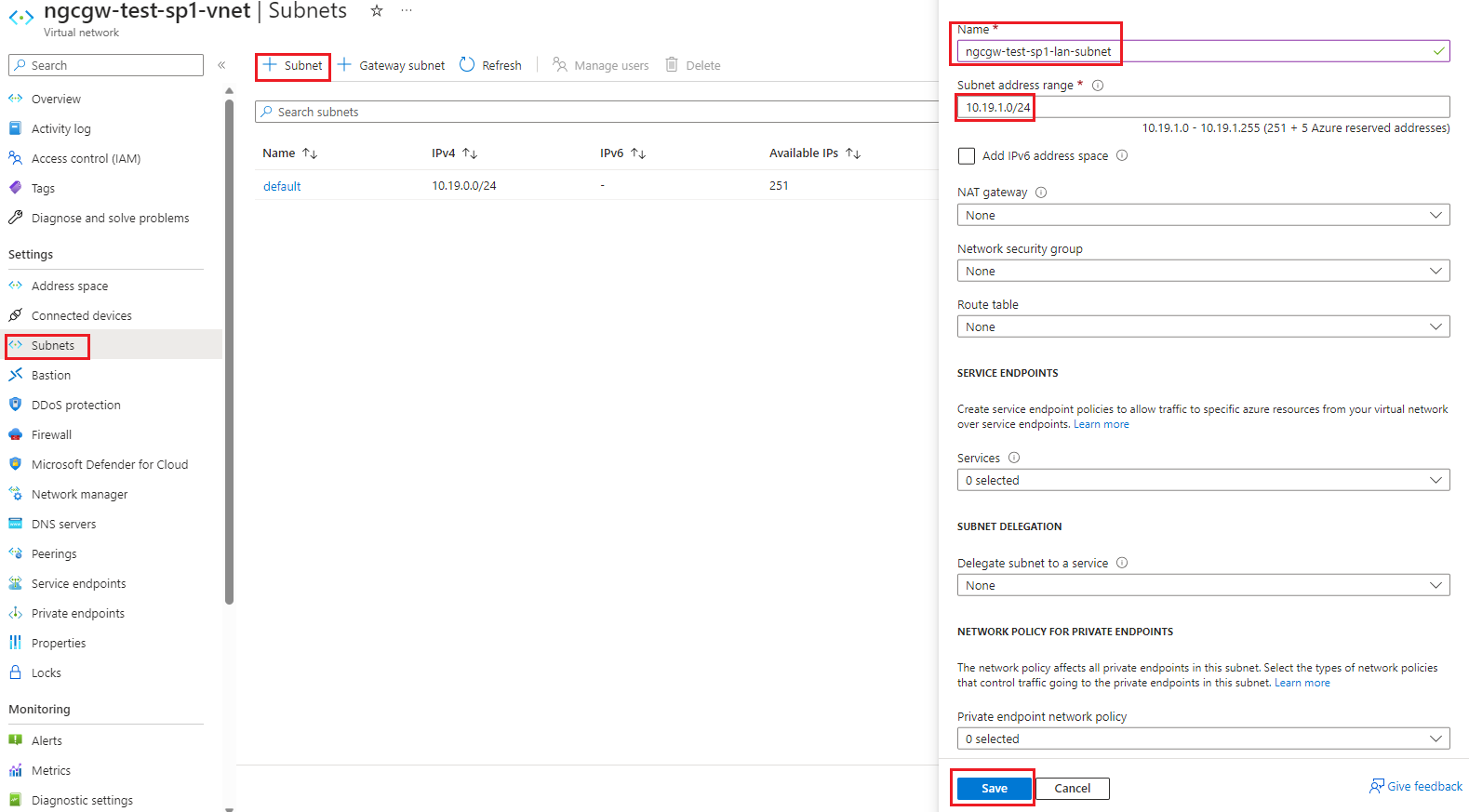
- Click on plus symbol to create another subnet for LAN
- Provide the name and check the range by default filled by Azure. In our case it is 10.19.1.0/24 which must be different from WAN subnet
- Click on save.
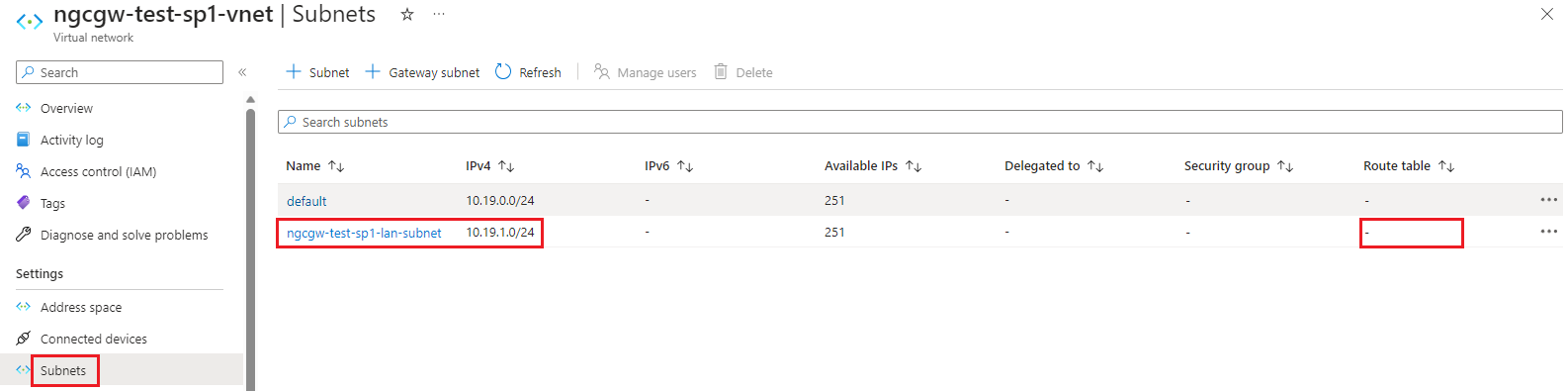
- New subnet will be displayed as below. It will not show any routing table associated with the subnet.
¶ VM Creation
- Use privileged credentials and login to Azure portal.
- Check subscription and identify resource group and region to deploy CGW.
- Users can use existing vnet (Virtual Networks) but we recommend to create new vnet to avoid modifying existing network configurations. (Refer to Create Network section of this page)
- Create 2 subnets, one for WAN and another for LAN network. For eg. WAN subnet 10.19.0.0/24 (default) and LAN subnet 10.19.1.0/24 (Refer to Create Subnet section of this page)
- Create a VM on Azure
- Navigate to home page and select Virtual machines
- Click on Create and select Azure virtual machine
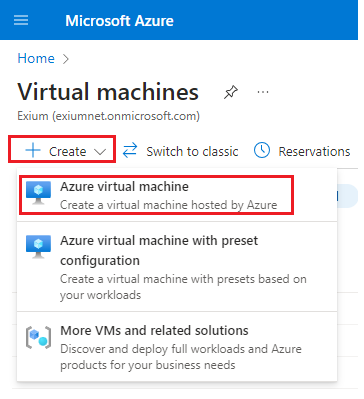
- Provide details such as Subscription, Resource group, Virtual machine name, Region, Image (Recommended- ubuntu Server 24.04 LTS – x64 Gen2), VM Architecture (x64), Size (As per throughput requirement, but user can use 1 vCPU and 3.5 GB RAM configuration).
- Select Authentication type as SSH public key. Username and key name can be modified or skipped with default values.
- Click on Review + create
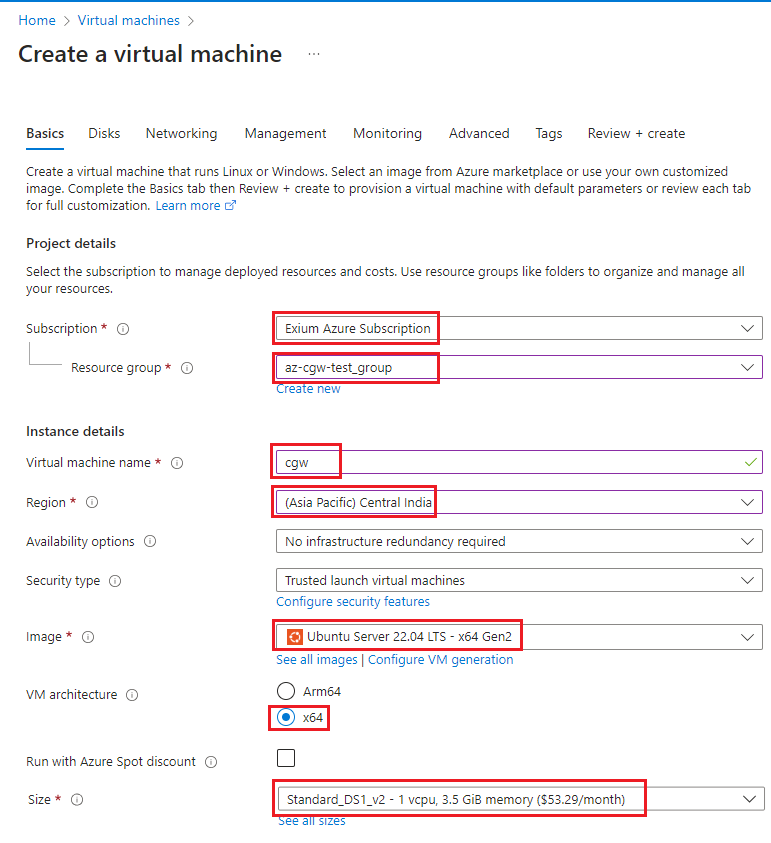

- Select Networking section to validate subnet used for networking
- Selected subnet will be configured on primary interface on VM, to provide WAN/Internet connectivity (In current example 10.19.0.0/24)
- For higher bandwidth, enable Accelerated Networking
- Azure does not allow Accelerated Networking on the VMs with lower size/flavors
- Click on Review + create

- Validate inputs and configuration for CGW VM and click on Create
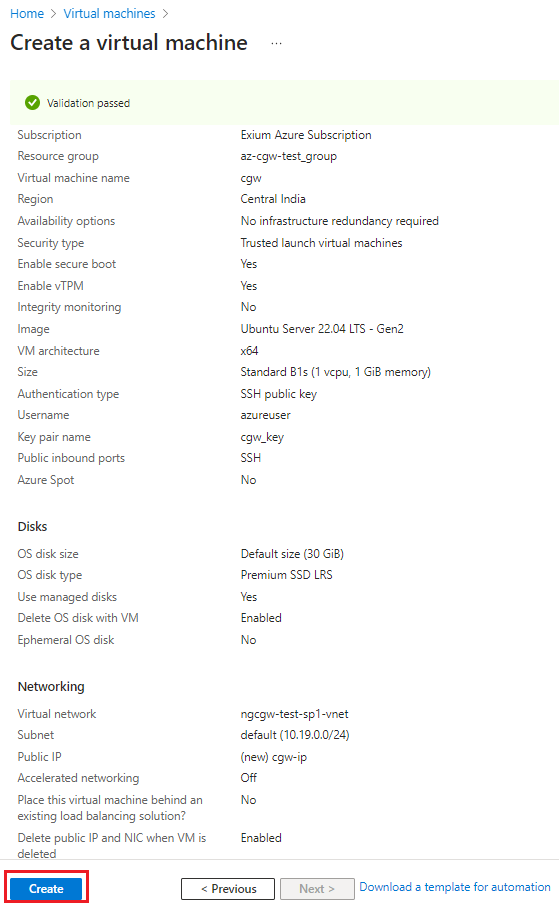
- Download ssh keys to access CGW later from ssh clients
- VM deployment will start and it will show progress on terminal
- After VM deployment completes, click on Go to resource
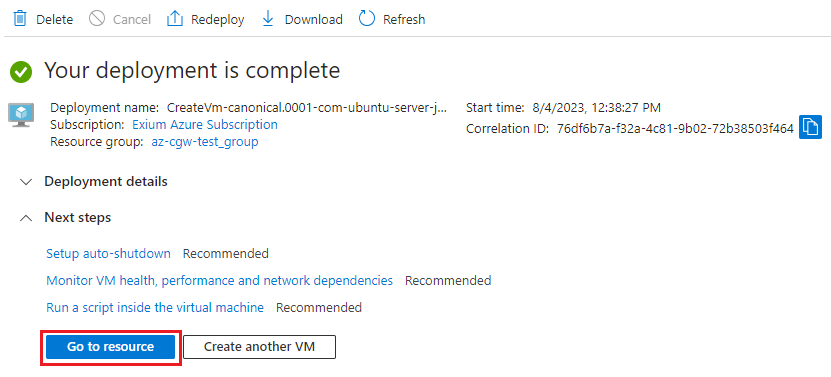
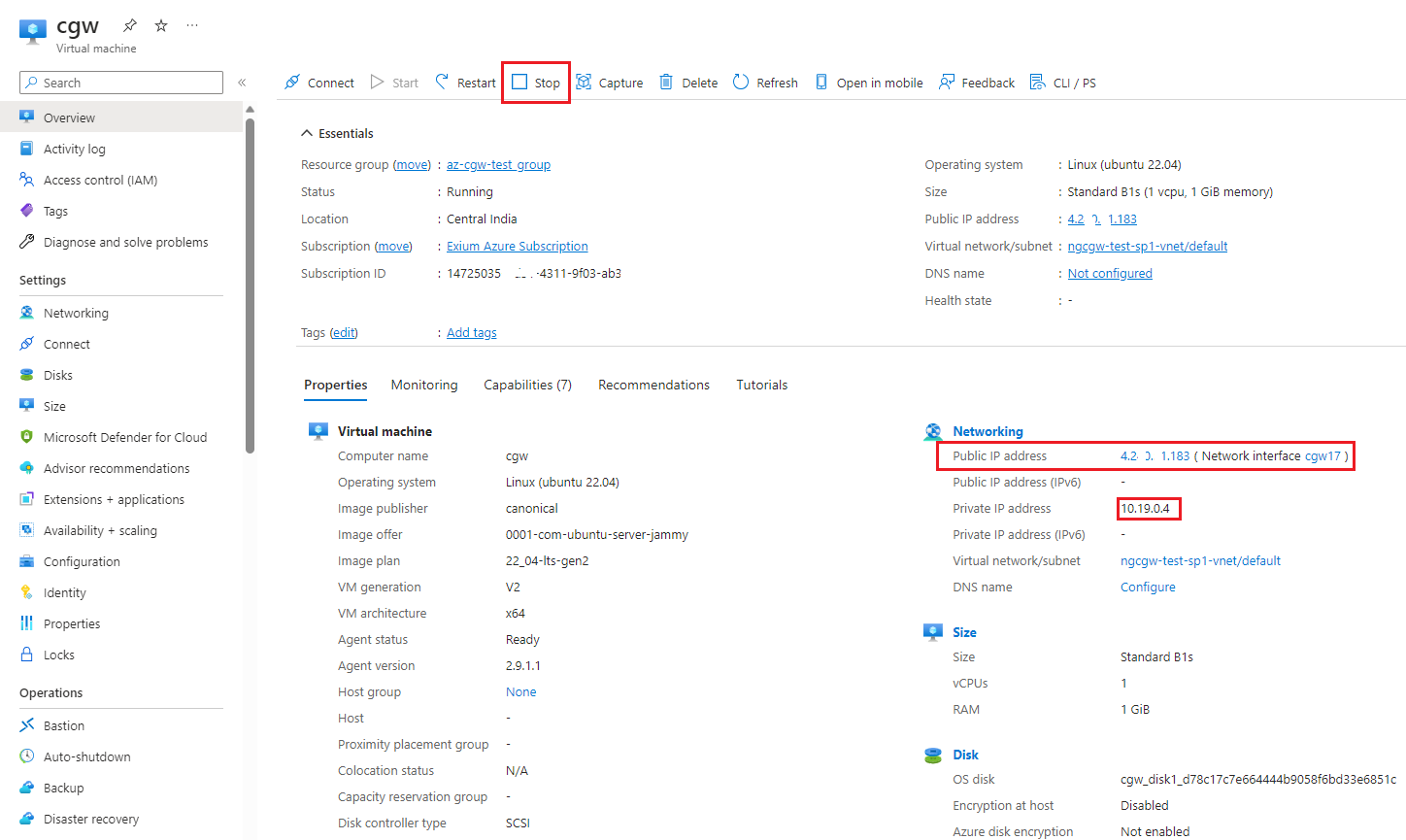
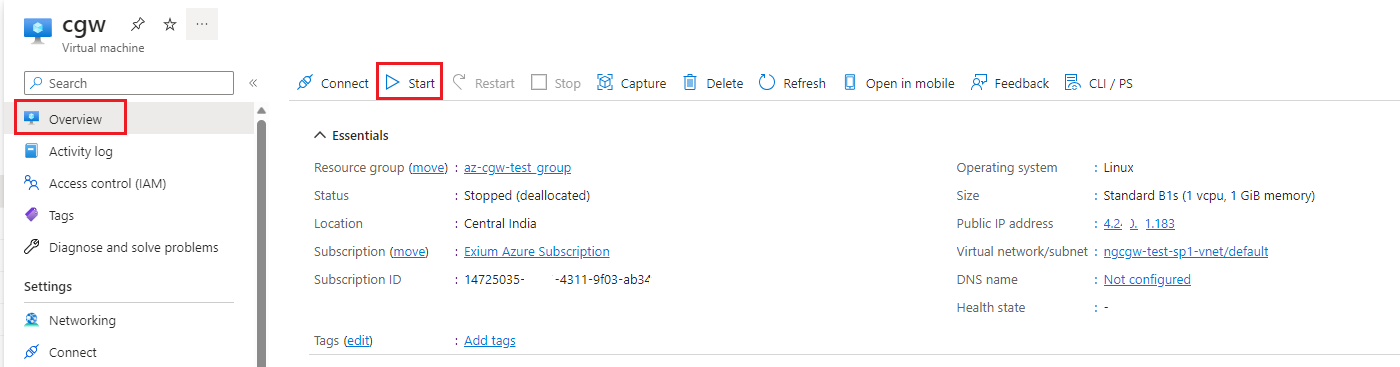
- Shutdown VM by clicking on Stop button
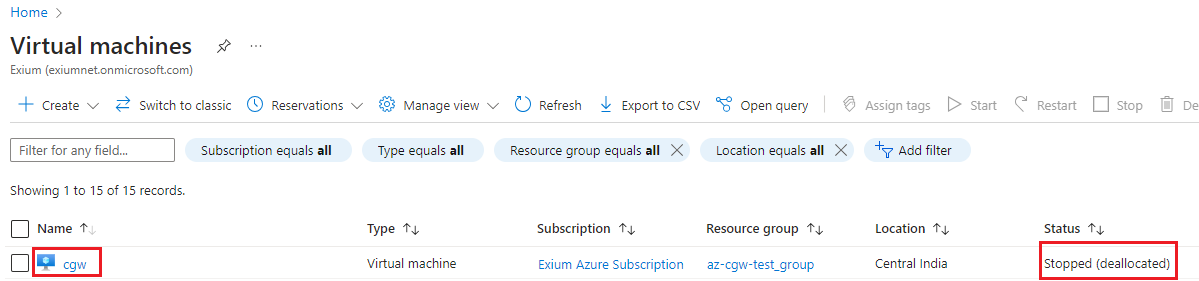
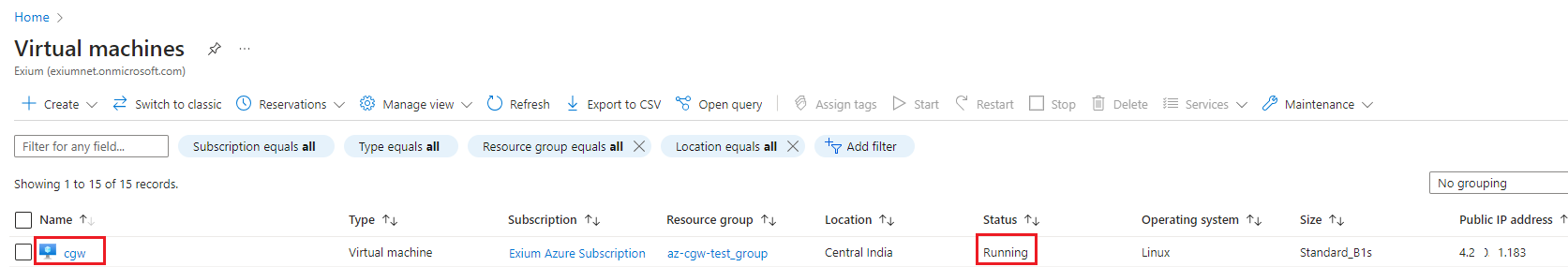
- Navigate to Home -> Virtual machines and check for CGW VM state. It must show stopped state
- Select CGW VM, and on Overview page, select Networking
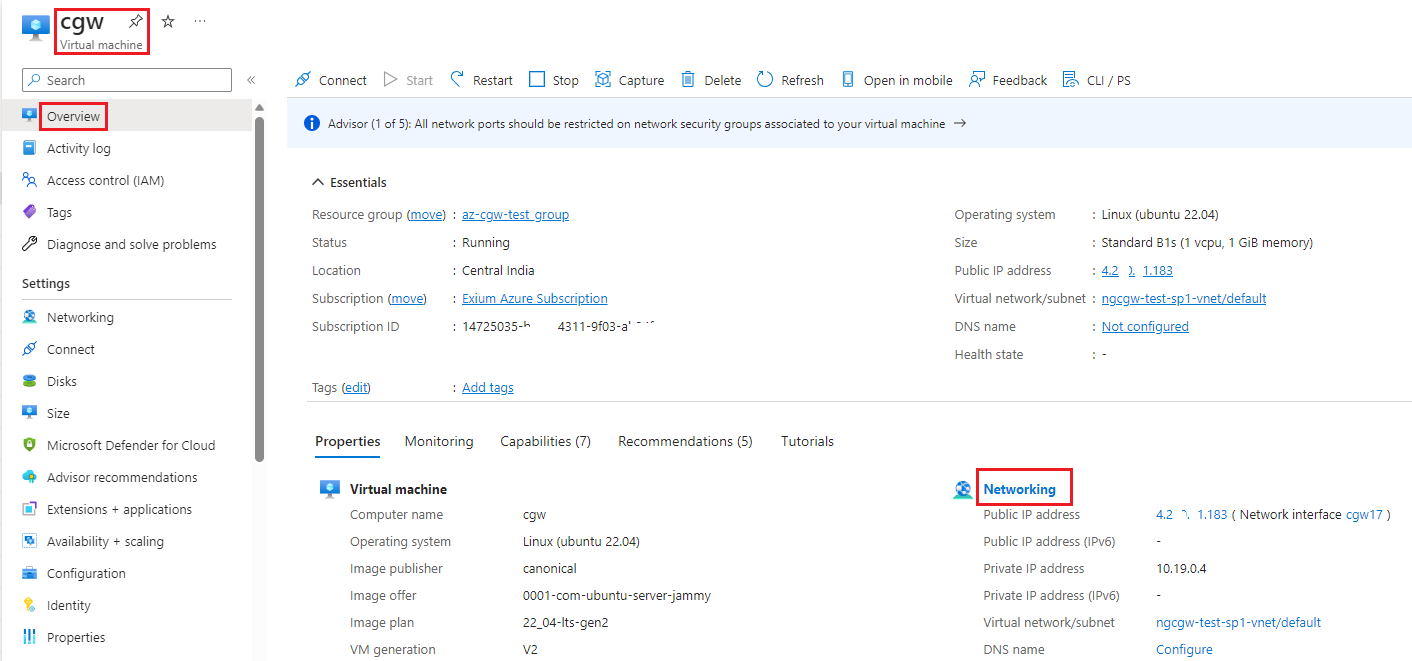
- Click on Attach network interface
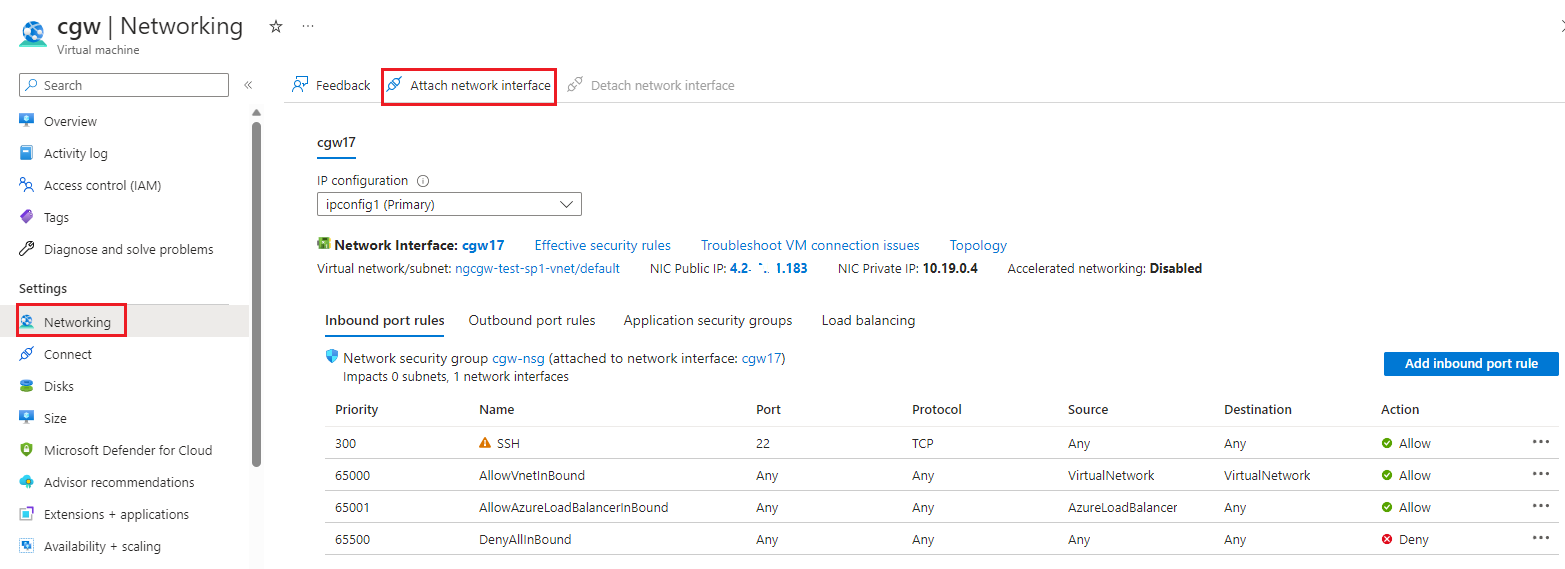
- Click on Create and attach network interface
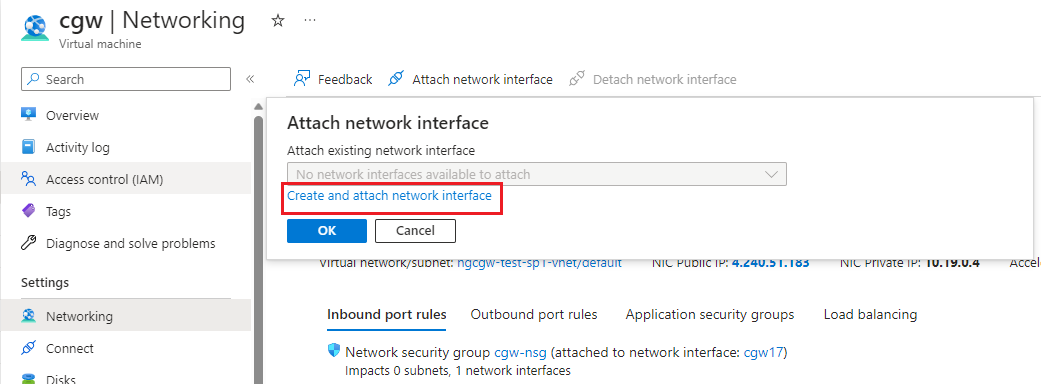
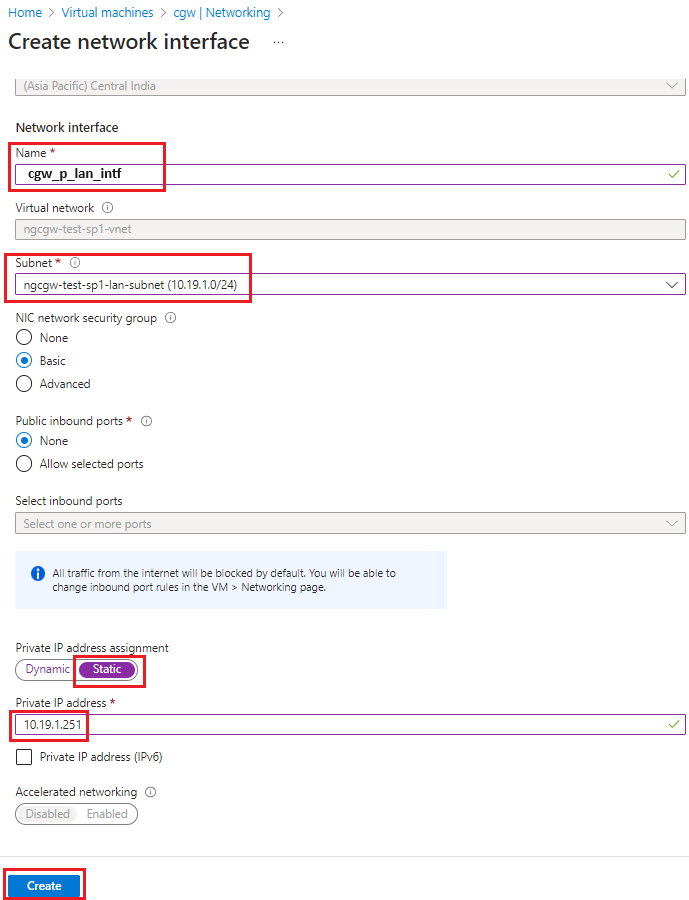
- Provide inputs:
- Check Subscription, resource group, location/region are same where CGW VM was created
- Provide name - cgw_p_lan_intf
When HA is enabled for CGW, network interface names must be cgw_p_lan_intf and cgw_s_lan_intf for Primary and Secondary node respectively.
- Check for virtual network, make sure it matches with CGW VM’s vnet
- Select subnet (Other then default, which was created for LAN interface) for eg. 10.19.1.0/24
- Select Static option for Private IP address assignment
- Provide static IP address as “10.19.1.251” if LAN subnet selected or configured is 10.19.1.0/24 (Application by default reserves and uses ‘.251’ IP address of the LAN subnet)
When HA is enabled for CGW, IP address must be subnets .251 and .252 for Primary and Secondary node respectively.
- Leave rest everything as it is.
- Create the network interface, by clicking on Create button
- Once LAN interface is created and attached, it will display on Networking section with the static IP address configured
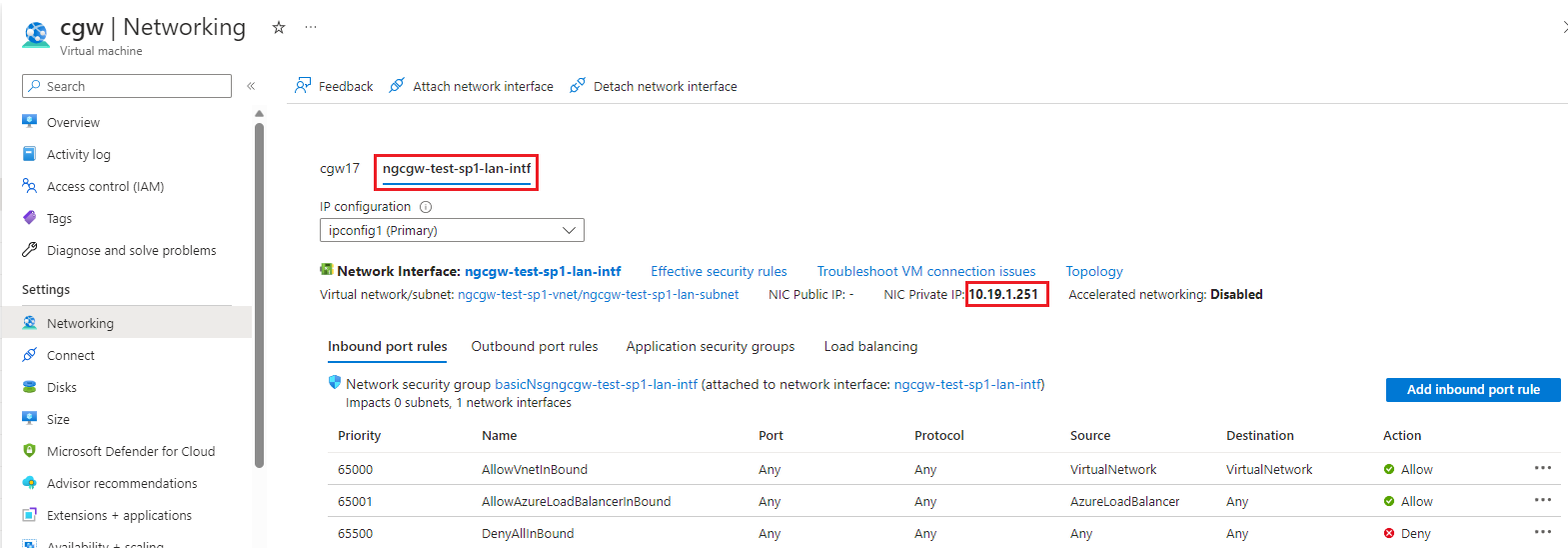
- Navigate to Home -> Virtual machines, select CGW machine and Start VM by clicking on start button
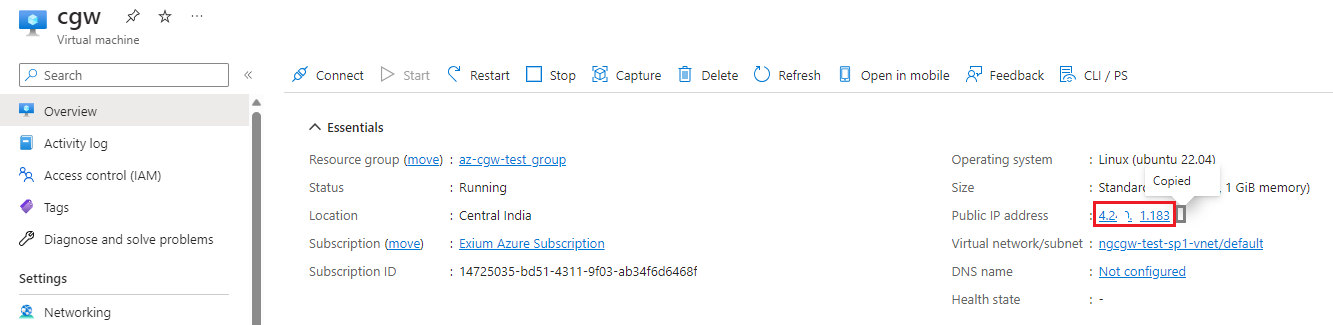
- Verify CGW VM is up and running before execution of further processes
¶ Verify IP Assignments
- Login to CGW VM using public IP and ssh key keys
- Command to do ssh from ssh client :
- On your laptop, navigate to the path where CGW VM key is downloaded (cgw_key.pem)
- Change file permission to 400 (chmod 400 cgw_key.pem)
- ssh -i cgw_key.pem azureuser@<cgw-vm-public-ip-address>
- Public IP of the CGW VM can be fetched from Azure portal (Home -> Virtual machines -> CGW VM -> Overview page)
- Command to do ssh from ssh client :
- Check IP addresses are matching with the subnets configured during deployment
- In current example - eth0 is WAN on primary interface with subnet 10.19.0.0/24 and eth1 is LAN on second interface with subnet 10.19.1.0/24
azureuser@cgw:~$ ip a
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN group default qlen 1000
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
inet6 ::1/128 scope host
valid_lft forever preferred_lft forever
2: eth0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc mq state UP group default qlen 1000
link/ether 00:0d:3a:a7:0f:b8 brd ff:ff:ff:ff:ff:ff
inet 10.19.0.4/24 metric 100 brd 10.0.0.255 scope global eth0
valid_lft forever preferred_lft forever
inet6 fe80::20d:3aff:fea7:fb8/64 scope link
valid_lft forever preferred_lft forever
3: eth1: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc mq state UP group default qlen 1000
link/ether 00:0d:3a:92:a8:4c brd ff:ff:ff:ff:ff:ff
inet 10.19.1.251/24 metric 200 brd 10.0.1.255 scope global eth1
valid_lft forever preferred_lft forever
inet6 fe80::20d:3aff:fe92:a84c/64 scope link
valid_lft forever preferred_lft forever¶ Default Route Check
Verify that default route is configured on WAN interface and not LAN interface.
Use below command to verify default route on machine. (Output must show WAN interface name and WAN subnet gateway as default gateway)
For example, in current output sample WAN interface shows eth0 and default gateway is 10.19.0.1. Interface has IP 10.19.0.4
azureuser@cgw:~$ ip route | grep default
default via 10.19.0.1 dev eth0 proto dhcp src 10.19.0.4 metric 100¶ WAN Connectivity Check
- After ssh access or login, check WAN/Internet on CGW VM – Use ping command with WAN interface name and check 8.8.8.8 and google.com to verify Internet access
- Few times, due to firewall in path, ping may not work. Allow ping to 8.8.8.8, 1.1.1.1 and google.com for CGW WAN IP on firewall.
- If no firewall in path, it is possible that Network Security Group (NSG) is not allowing ping to work. Configure inbound and outbound rules for the CGW VM. Add rule or modify existing rule and include ICMP protocol in allow list for any IP range.
For example, in current sample, eth0 is used as WAN interface name
azureuser@cgw:~$ ping -I eth0 8.8.8.8
PING 8.8.8.8 (8.8.8.8) 56(84) bytes of data.
64 bytes from 8.8.8.8: icmp_seq=1 ttl=115 time=13.0 ms
azureuser@cgw:~$ ping -I eth0 google.com
PING google.com (142.250.125.100) 56(84) bytes of data.
64 bytes from jh-in-f100.1e100.net (142.250.125.100): icmp_seq=1 ttl=101 time=25.7 ms¶ LAN Connectivity Check
Use ping command with LAN interface name and check private VM/resource IP connectivity.
For example, in current sample, eth1 is used as LAN interface name
azureuser@cgw:~$ ping -I eth1 <IP_Address>¶ Create a Cyber Gateway
To create a Multi Interface Cyber Gateway (CGW-MIF), follow the steps below.
- Navigate to the MSP admin console -> Client Workspace
- Click on Gateways in the left menu bar → Add Gateway
- Name - You may change the name of the CGW
- Select Gateway Type as Multi Interface. Fill in the details and add Gateway.
- High Availability (HA) - Please select ‘Yes’ if CGW to be deployed in High Availability mode. 2 Ubuntu VMs or any other 2 quantity of recommended hardware needed for HA setup, Please refer HA user manual for more detailed instructions.
- Admin Notifications Email - Provide email ID which will receive alerts/notifications related to CGW
- LAN Configuration
- If NAT is not required on LAN network then select No for option NAT on LAN, else skip it
- LAN Subnet - Enter LAN subnet (for eg. 10.19.1.0/24). This will be added as Trustpath automatically to Gateway, so no need to add this as Trustpath again. VERY IMPORTANT: This is the subnet that will be behind the gateway (i.e. plugged into the LAN port of the gateway) that you want remote users to be able to access. This is NOT the subnet that the WAN port of the gateway is on. Machines on this subnet will be able to access internet via CGW, if they are configured with default gateway as CGW LAN IP.
- LAN IP - Specify IP address of the Gateway which will be used by the devices behind CGW in LAN subnet specified in above parameter. Configured LAN Gateway IP will be installed on the CGW machine, so make sure it is not conflicting in network or not installed on any other device statically. If HA (High Availability) is enabled, then do not use .251 and .252 IP addresses as LAN Gateway IP. These IP addresses will be installed on Primary and Secondary nodes respectively.
- Next HOP GW for LAN - Provide gateway for LAN traffic. It is required when LAN traffic has to send all traffic to an IP which handles communication with actual core LAN network.
- DHCP Configuration
- Select Yes, if DHCP IP assignment should happen from CGW on LAN network. Please refer DHCP user manual for more detailed instructions.
- If selected Yes, DHCP server will be started for LAN
- Specify Start Range and End Range
- Select Yes, if DHCP IP assignment should happen from CGW on LAN network. Please refer DHCP user manual for more detailed instructions.
- In case of Multiple LAN subnets, click on + symbol and add additional subnets, else SKIP it.
- Enable / Disable DHCP functionality individually on each LAN subnet and set their start and end range
- Enable / Disable DHCP for All LANs
- VLAN Configuration
- Select Yes if CGW needs to support VLAN network segments. Please refer VLAN user manual for more detailed instructions.
- If Yes is selected, please specify VLAN IDs and VLAN subnets.
- Specify VLAN Gateway IP
- Inter VLAN Communication - Select Yes, if inter VLAN communication should be allowed
- Enable/Disable DHCP IP allocation for all VLANs by selecting Yes/No for DHCP for All VLANs option
- You may also enable/disable DHCP IP allocation for individual VLAN by selecting Yes/No for DHCP option
- By default, VLAN DHCP function will use start range .2 to end range .250
- Select Yes if CGW needs to support VLAN network segments. Please refer VLAN user manual for more detailed instructions.
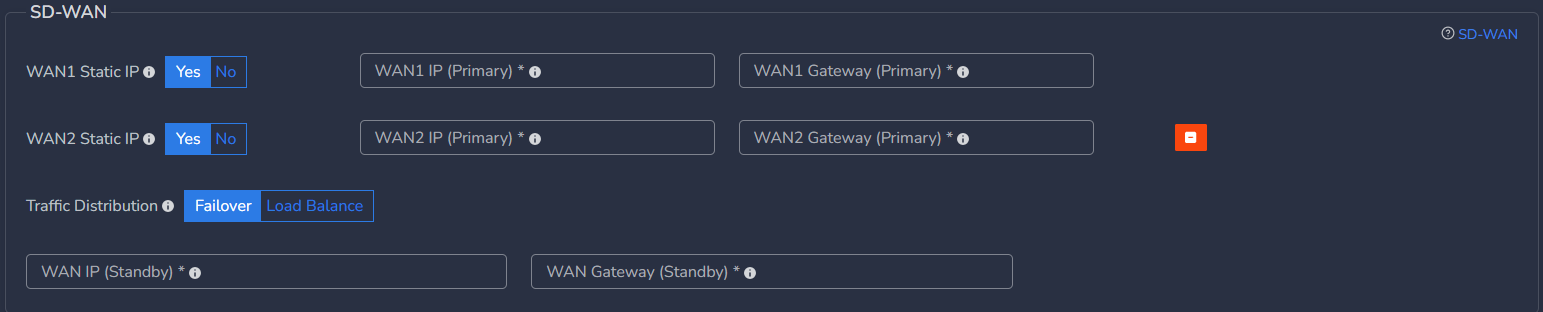
- SD-WAN Configuration
Mostly for CGW deployment on public clouds, you may not need static IPs on WAN interfaces but for specific requirements, it can be added.
- Static IP address along with their default gateway can be configured.
- Mostly it is required when existing Firewalls are replaced with CGW and ISP provided public IP and gateway need to configured on CGW node directly on WAN interface. Please refer SD-WAN user manual for more detailed instructions.
- Click on Add ISP1 WAN
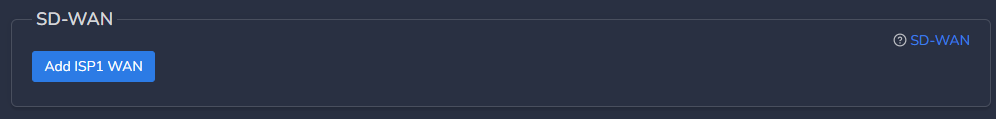
- If WAN1 Static IP is set to Yes, configure below parameters, else skip it.
- WAN1 IP (Primary) - Specify IP with subnet for Primary CGW node
- WAN1 Gateway (Primary) - Specify gateway IP without subnet for Primary CGW node
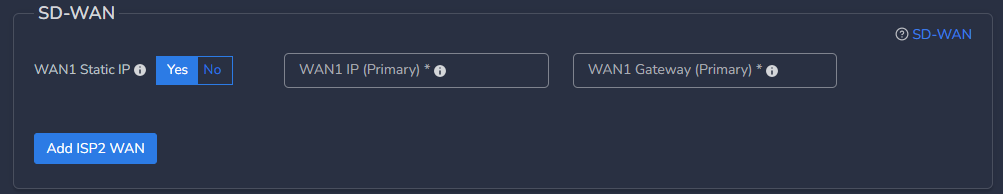
- In case you want to deploy CGW with 2 WAN (WAN1 on ISP1 and WAN2 on ISP2) interfaces then click on Add ISP2 WAN, else skip it
- If selected Yes, you can select Traffic Distribution as Failover or Load Balance
- In case of Failover, only one WAN interface / ISP connection will be active
- In case of Load Balance, both WAN interfaces / ISP connections will be active and in load balance mode
- If Multi WAN is selected with WAN Static IP option, then WAN2 IP (Primary) must be configured with WAN2 gateway (Primary)
- Please refer SD-WAN user manual for more detailed instructions.
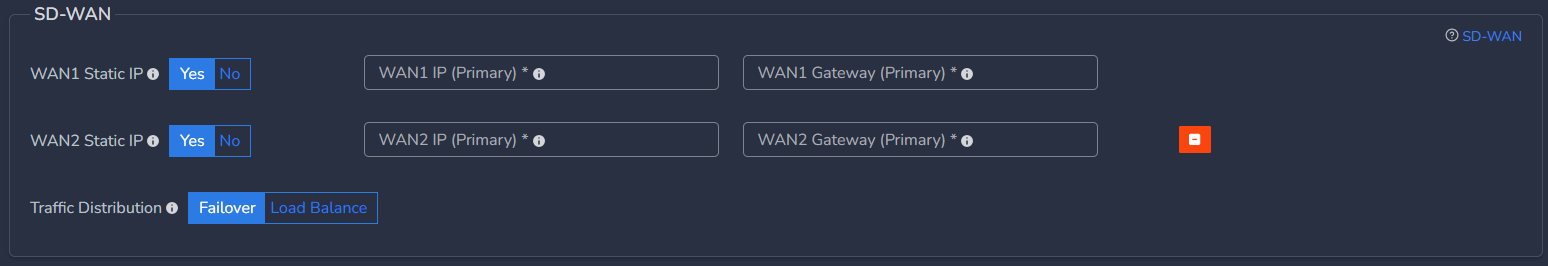
You can configure static IP on WAN1 which is on ISP1 and select No option for WAN2 which is on ISP2 in case ISP2 works on DHCP. In this case, WAN1 will have static IP and WAN2 will get IP allocated from ISP2.
- In case High Availability is enabled, static WAN IP and gateway are required for both nodes
- WAN IP (Standby) - Specify IP with subnet for Secondary CGW node
- WAN Gateway (Standby) - Specify gateway IP without subnet for Secondary CGW node
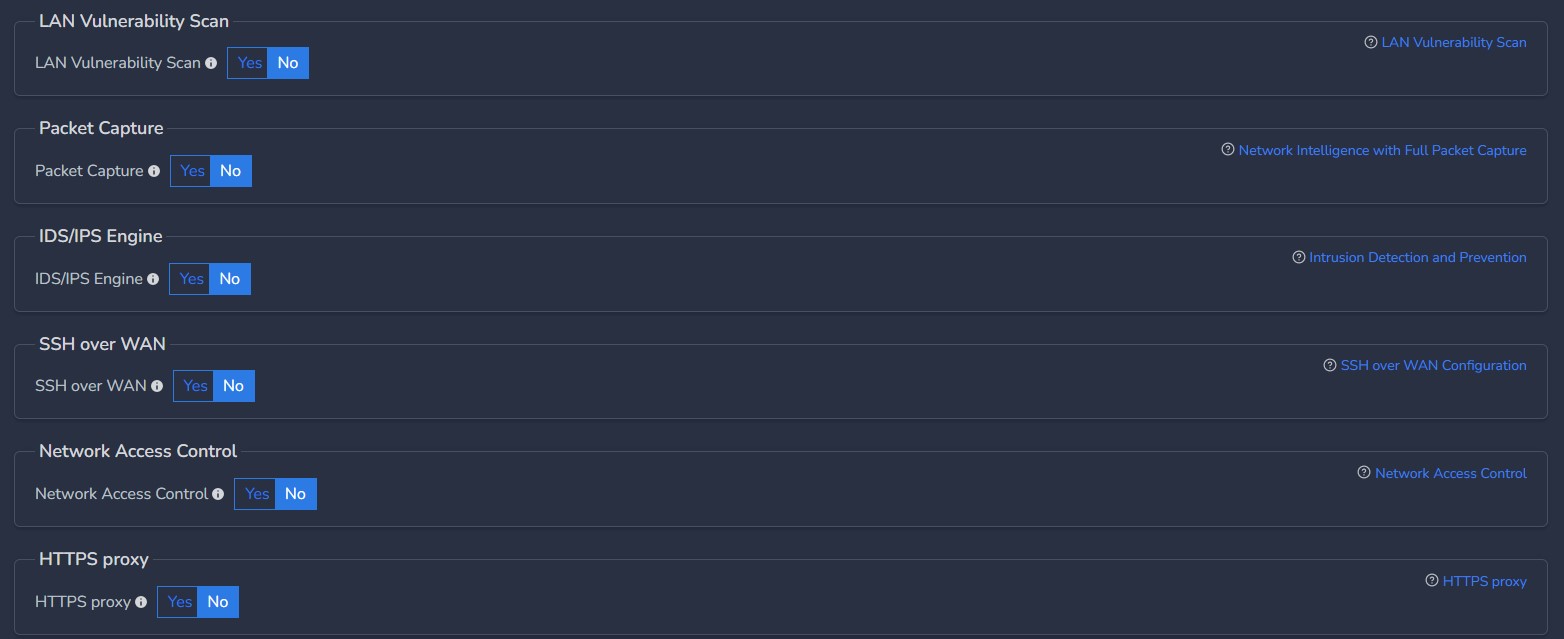
- As per requirements, customer can enable/disable advanced configuration mentioned below.
- Please refer user guides for advanced features for more detailed explanation
¶ Deploy the Cyber Gateway
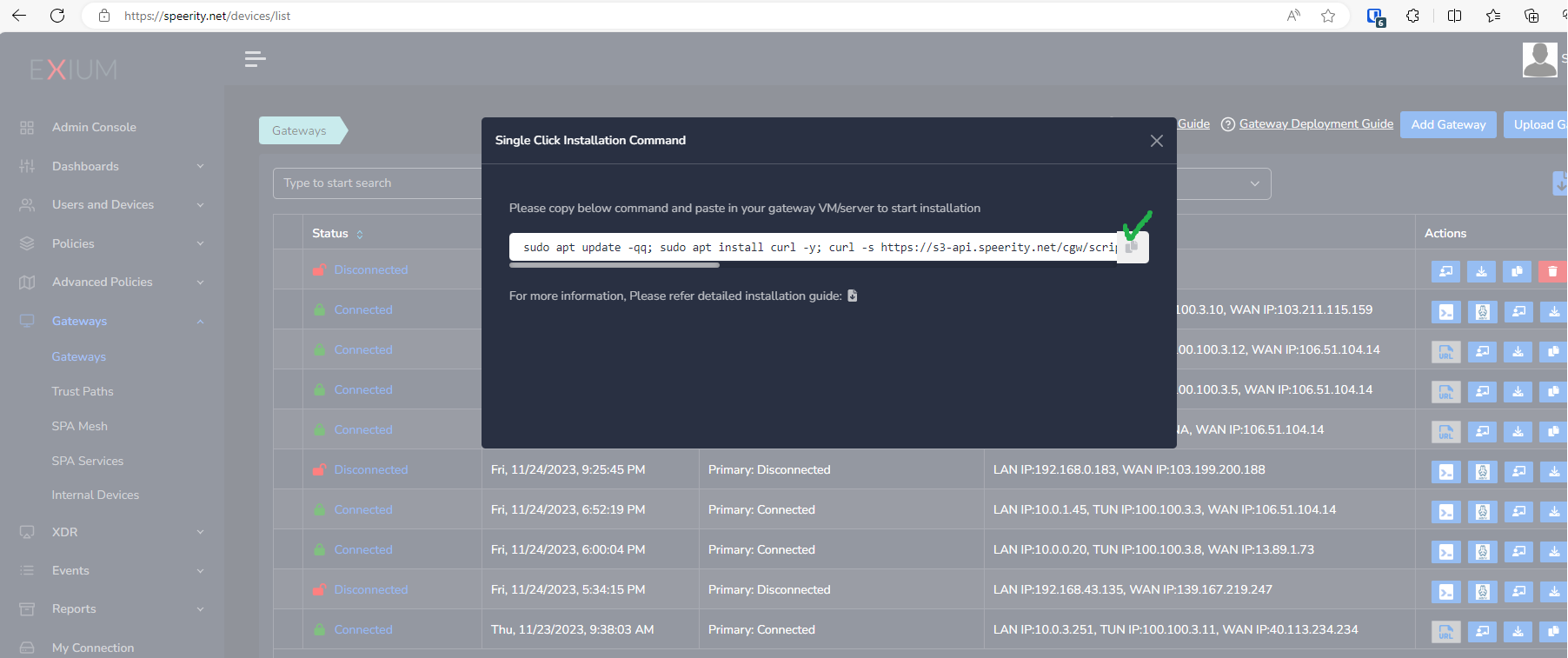
- Copy the Script for the cyber gateway you just created as shown in the screenshot below
- Paste the Script in the VM SSH console
- Press Enter
In case, you are unable to login to machine using SSH to copy and run CGW install command, then we recommend you to run pre-install script mentioned below. You have to type it on console, because copy paste won't work on some direct machine consoles.
bash <(curl -s https://s3-api.speerity.net/cgw/scripts/cgwctl.sh)Copy
Please share Workspace and CGW names with us on support@exium.net. We will push installation remotely.
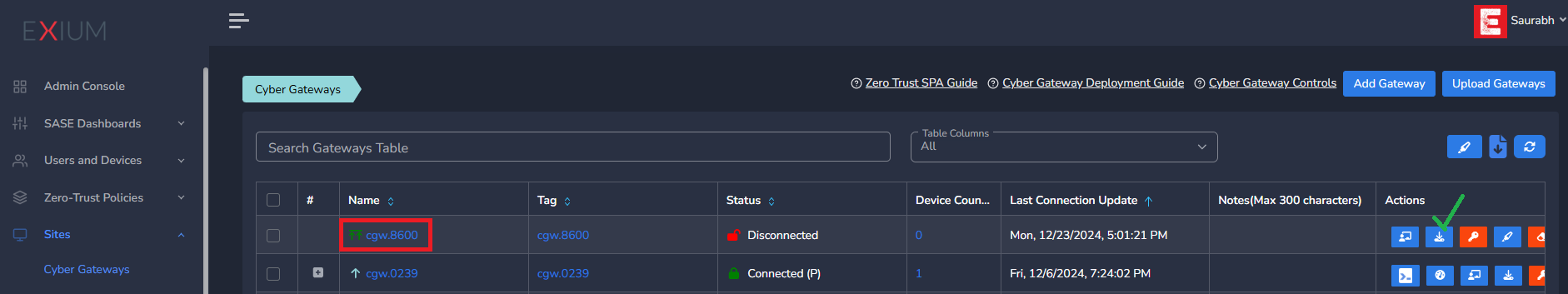
The Cyber gateway deployment will start. At this time, you can leave the deployment running unattended. You will receive an email on the admin email that you specified earlier when the deployment is complete. You can also check the status of the cyber gateway in the Exium admin console. When cyber gateway is deployed successfully and connected, you will see a Green Connected Status as in the screenshot below.
- Copy Install Command:
Once the cyber gateway is deployed successfully and connected, you can start testing the Zero Trust Secure Private Access policies.
¶ Need High Availability?
Skip this section if HA is not required.
High availability on Azure requires additional configuration. For inside-out access, CGW will need floating IP configured on it's LAN interface. Floating IP will act like a LAN gateway for the machines behind CGW on Azure. It is always attached to active peer and enables external connectivity. On failover, the process of detaching the IP address and reattaching it to the now active peer can take a few minutes.
To enable CGW HA on Azure, you need an Azure Active Directory application and Service Principal that includes the permissions listed below:
"Microsoft.Authorization/*/read", "Microsoft.Compute/virtualMachines/read", "Microsoft.Network/networkInterfaces/*", "Microsoft.Network/networkSecurityGroups/*", "Microsoft.Network/virtualNetworks/join/action", "Microsoft.Network/virtualNetworks/subnets/join/action"
User must be Global Administrator to create service principle.
Perform below steps on any of your existing Ubuntu machine. If you don't have any, you can use one of CGW VM and logout from Azure account after configuration completes:
- Install Azure CLI
bash <(curl -sSL https://s3-api.speerity.net/cgw/scripts/install-az-cli.sh)
- Login to your Azure account (Needs Global Administrator privileges)
az login --use-device-codeFollow the instructions on screen to login. Open URL on your laptop's browser and provide the code.
After successful login, identify the Subscription ID and Resource Group name, which will be used for CGW deployment on Azure:
To get subscription ID, execute below command:
az account list --query '[].{SubscriptionName:name, SubscriptionId:id}'To get list of resource group names configured on your Azure environment, execute below command:
az group list --query '[].name' --output tsvUse below script/command to generate the HA-configuration file for CGW.
Replace subscription-id and resource-group-name fields in below command with actual ID/name fetched in above steps:
bash <(curl -sSL https://s3-api.speerity.net/cgw/scripts/create_service_principal.sh) --sub_id <subscription-id> --rg_name <resource-group-name>HA-config file az-cgw-mif-ha-param.ini will be created in current directory. Copy az-cgw-mif-ha-param.ini file on your laptop to use it on CGWs post CGW installation. This file must be copied on both CGW machines once they are deployed.
Repeat VM Creation step for CGW secondary node also and create another VM.
Once secondary node is created, copy the install command from admin console.
Copy Install Command for secondary node again:

- Replace P with S, in install command, which will look like:
sudo apt update -qq; sudo apt install curl -y; bash <(curl -sSL https://s3-api.speerity.net/cgw/scripts/cgw_mif_install.sh) <AUTH_TOKEN>,S
Copy HA-config file az-cgw-mif-ha-param.ini on both CGWs in path /etc/ngcgw/ha/ directory after installation is completed on both CGW nodes. Service will not come up on CGW until HA config file is copied on CGW nodes.
¶ Secure Private Access (SPA): Outside-In Access
¶ Pre-requisites
- Make sure user is added or present on the workspace/admin console
- Make sure user is part of admin group (if no other group is created for testing)
- Make sure trust path is associated with the admin user group
¶ Client connection and SPA testing
- Download and configure Wireguard on user’s laptop
- Connect the service and verify basic internet and browsing work.
- Ping any of the IPs from the trust path subnets 10.98.2.0/24
- If any web application is running behind CGW, then access on browser using private IP to test and confirm.
¶ Secure Internet Access (SIA): Inside-Out Access
CGW can be configured as default gateway for the resources/VMs on Azure to act as a default gateway for internet access. Note down CGW LAN IP address which was created in earlier steps.
Refer to the below steps:
- Navigate to Home -> Virtual networks
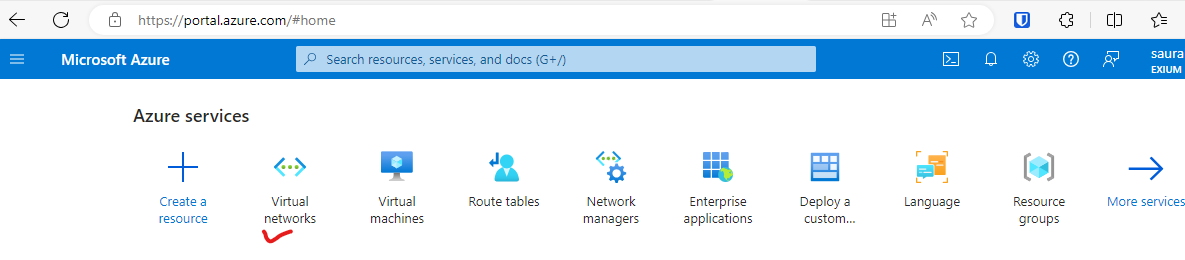
- Select the vnet created for CGW
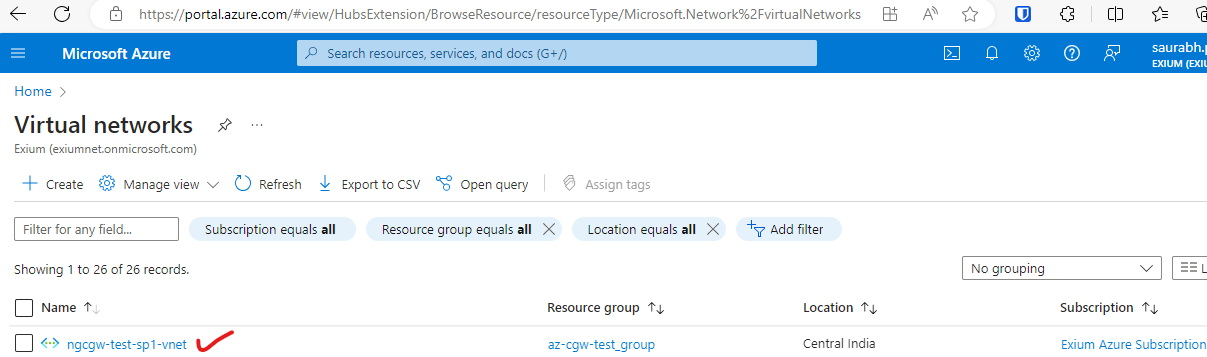
- Select Subnet
- Click on the LAN subnet, in current example it is 10.19.1.0/24 (If not created, click on plus symbol to add subnet)
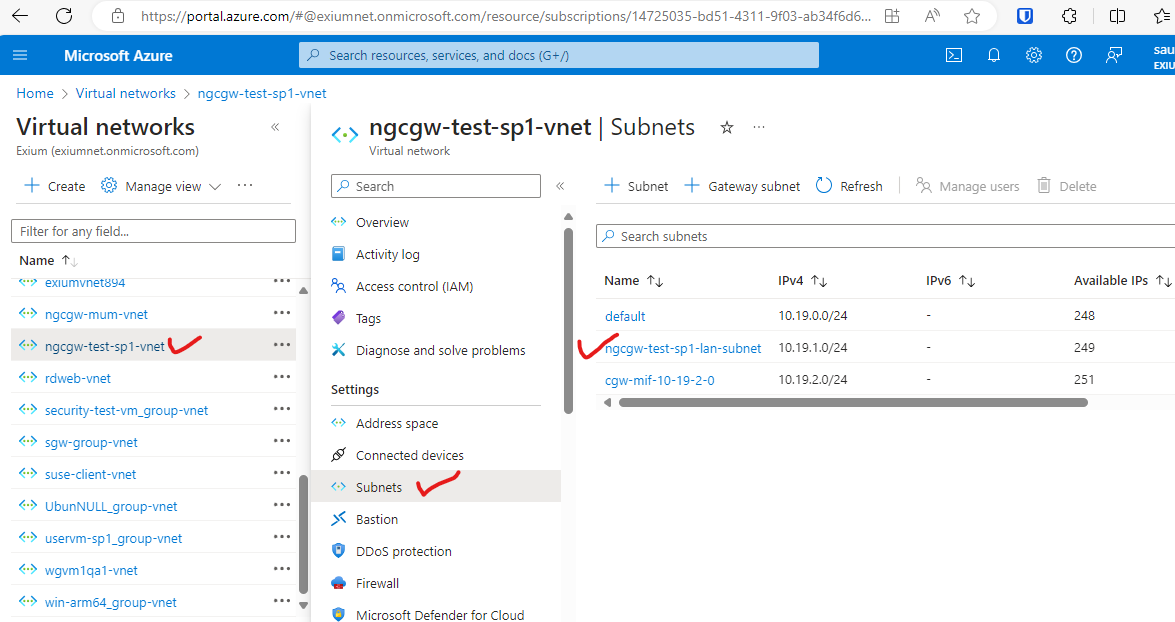
- Navigate to “Route tables” page
- Click on plus symbol to create new route table
- Provide details for route table creation
- Select Subscription,
- Select the resource group used for CGW VM creation
- Select region where CGW VM is created
- Provide name of the VM.
- Click on “Review and create” and create it.
- Click on “Go to resource”
- Click on “Routes” in left panel.
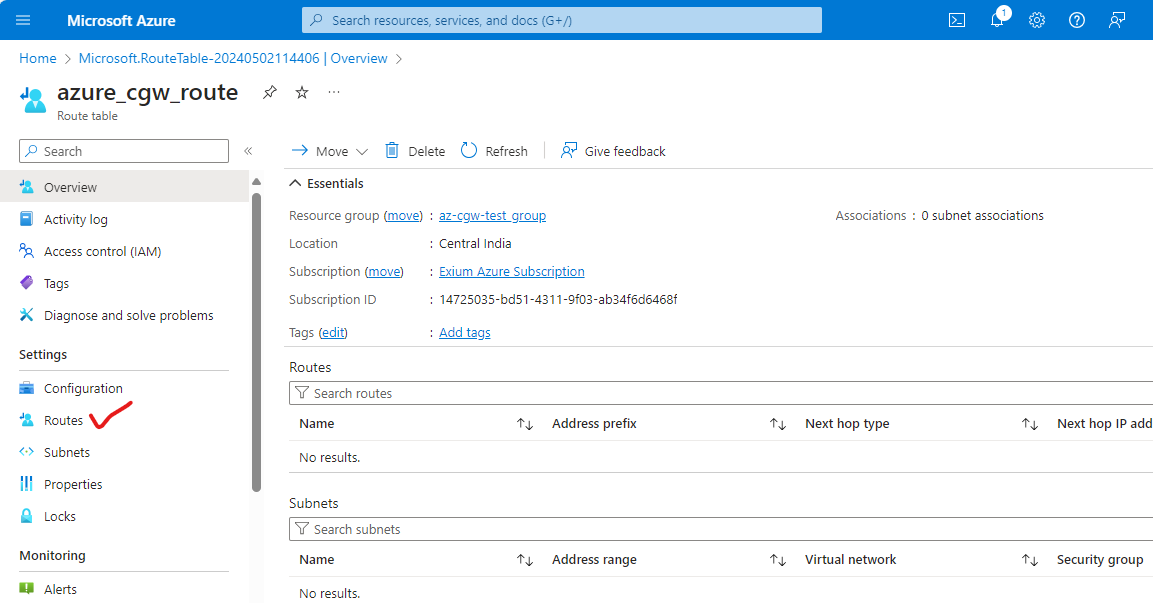
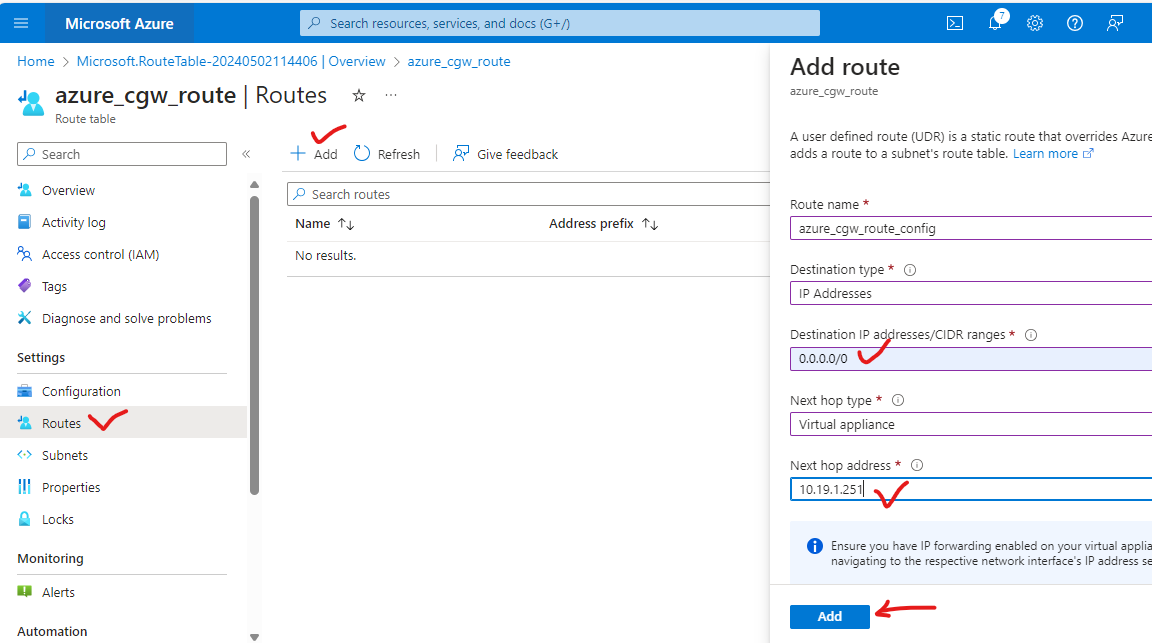
- Click on Add to add a new route in table.
- Fill all the fields:
- Provide name
- Select IP addresses in Destination type
- Enter 0.0.0.0/0 for default traffic in Destination IP addresses
- Select virtual appliance in Next hop type
- Enter the LAN interface static IP address which was created and attached to CGW VM during VM creation/deployment. (For eg. 10.19.1.251). Click on Add.
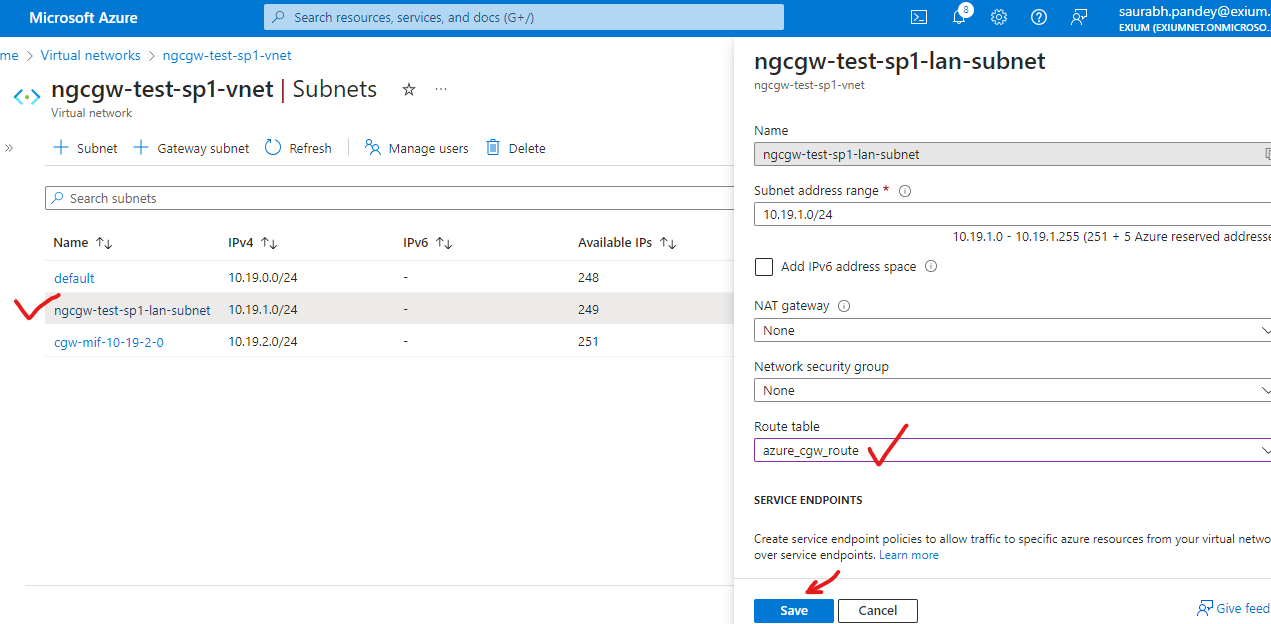
- Navigate to Home -> Virtual networks
- Select the vnet created for CGW

- Select Subnets and click on LAN subnet

- Click on CGW LAN subnet, select the route table created in earlier step and save.
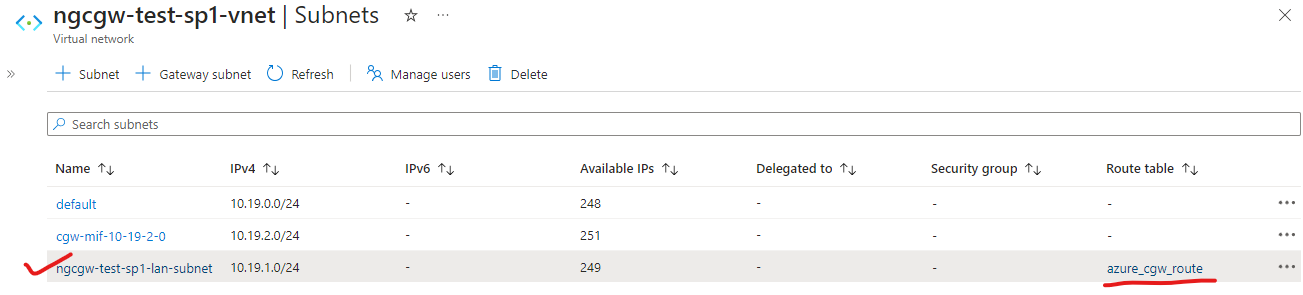
Note: Azure private VMs configured within LAN subnet will now be able to securely access internet via CGW as default gateway.
¶ Checklist for higher throughput
Azure supports different flavors/sizes of VMs as per bandwidth requirements. To achieve throughput or bandwidth in Gbps, you must select VM size with higher resources.
For example, Standard D4ds v4 size can provide bandwidth up to 10Gbps. Azure also restricts egress traffic and VMs which are accessing internet via CGW, must be configured with higher size to achieve best results. Accelerated networking must be enabled on the CGW and as well as on the user machines.
¶ How to enable Accelerated Networking?
- Login to Azure portal
- Navigate to Virtual Machines
- Identify VM and click on it's name
- Navigate to Networking
- Select the Interface (vNIC) - (In case of CGW, select LAN interface which was attached to VM during VM deployment)
- Click on Edit Accelerated Networking
- Enable and click on Save