¶ Introduction
In the ever-evolving landscape of network and web security, Web Proxy is a powerful and versatile solution that plays a pivotal role in enhancing performance, security, and control over internet access. This solution brief provides an overview of Web Proxy, its capabilities, and the benefits it offers for organizations. We also provide guidelines on enabling Web proxy in Exium's Cyber Gateway for Modern Workplace Security.
NOTE: We do NOT recommend to use the Web proxy with SSL decryption broadly due to the concerns with SSL decryption. Read our article on Why adopt an AI approach over SSL Decryption? In Exium's on-prem Cyber Gateway, we offer Web proxy with SSL decryption capability to address very specific use cases such as visibility into search engine queries.
¶ Challenges
Internet Access Management: Organizations need to manage and control internet access to ensure security, compliance, and efficient resource utilization.
Content Filtering: Filtering and blocking unwanted or malicious content is crucial for maintaining network integrity.
Traffic Optimization: Efficiently handling internet traffic, reducing bandwidth usage, and improving response times are continuous challenges.
Security and Anonymity: Protecting against cyber threats, preserving user privacy, and ensuring secure web browsing are vital considerations.
¶ Solution: Web Proxy
|
Feature |
Description |
|---|---|
| Web Caching | Web Proxy caches frequently requested web content, reducing bandwidth usage and accelerating web page load times. |
| Content Filtering | Implement content filtering policies to block access to malicious or inappropriate websites, ensuring network security and compliance. |
| Access Control | Enforce access policies based on IP addresses, user authentication, or group memberships to control who can access what content. |
| Security | Enhance security by inspecting web traffic for malware, viruses, and intrusion attempts. |
| SSL / HTTPS Inspection | Inspect and filter HTTPS traffic through a feature called SSL Bumping, allowing for deep inspection of encrypted traffic |
| User Authentication | Enforce user authentication to control access to internet resources, track user activity, and maintain accountability. |
¶ Benefits of Web Proxy
Improved Performance: Web Proxy accelerates web content delivery by caching frequently requested data, improving response times.
Enhanced Security: Content filtering, SSL inspection, and security measures protect against malicious content, phishing, and other threats.
Access Control: Web Proxy offers granular control over internet access, ensuring compliance with corporate policies and regulatory requirements.
Cost Savings: Reduced bandwidth usage through caching and optimized web traffic leads to cost savings.
Web Proxy is a versatile and robust solution for managing internet access, enhancing security, and optimizing web traffic. By combining content caching, access control, content filtering, and security features, organizations can ensure a safer, more efficient, and cost-effective internet experience for users while meeting security and compliance requirements. Web Proxy is an invaluable tool for modern network management and security.
¶ Configuring Web Proxy for Cyber Gateway on Exium Platform
To configure HTTP proxy server for a new Cyber Gateway deployment, follow the steps below.
- Navigate to the MSP admin console -> Client Workspace
- Click on Sites → CyberGateways in the left menu bar → Add Gateway if deploying a new CG
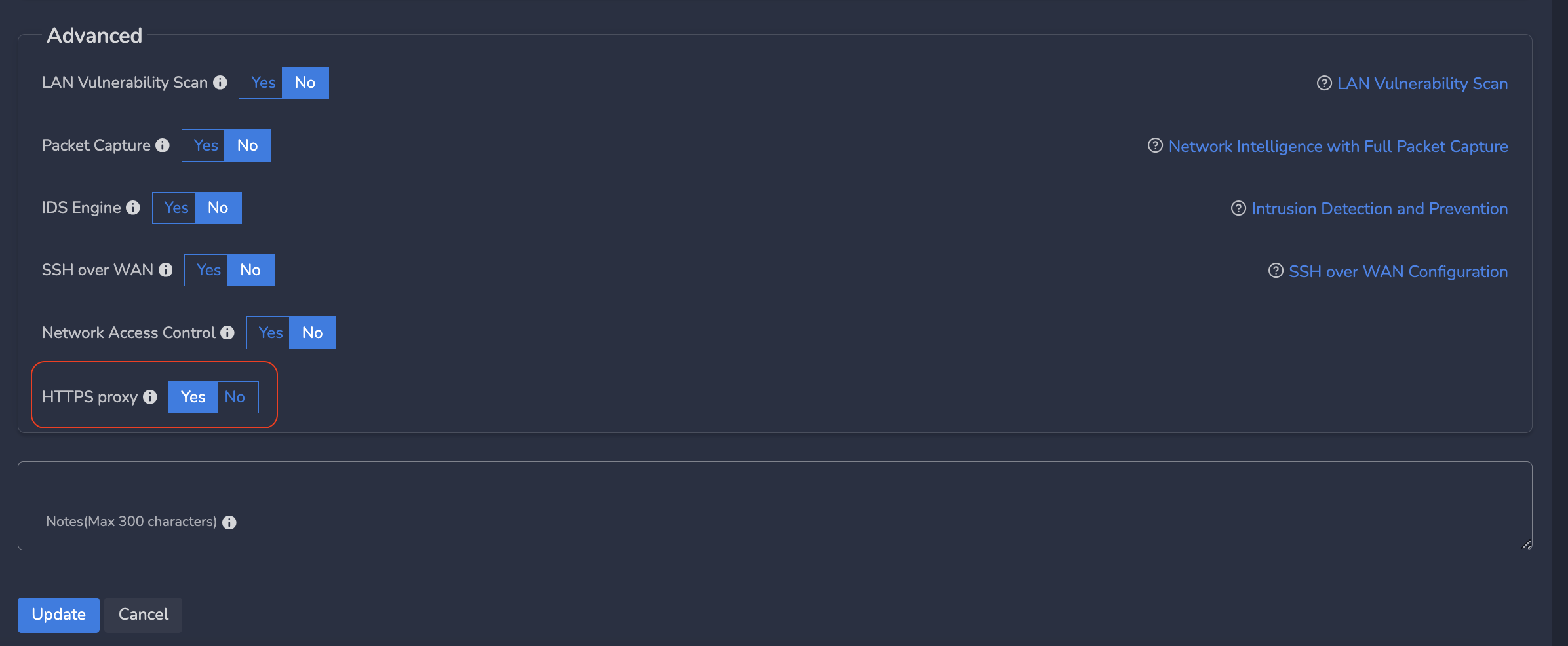
- Go to “Advanced” section and toggle the “HTTPS Proxy” switch to “Yes” (see screen shot below)
- Once done , click “Save/Update”
- Please follow the instructions for Multiple interface CGW deployment for other configuration options.
¶ Testing Web Proxy
Get the LAN IP address of CGW machine.
- Navigate to the MSP admin console -> Client Workspace
- Click on Sites → CyberGateways in the left menu bar
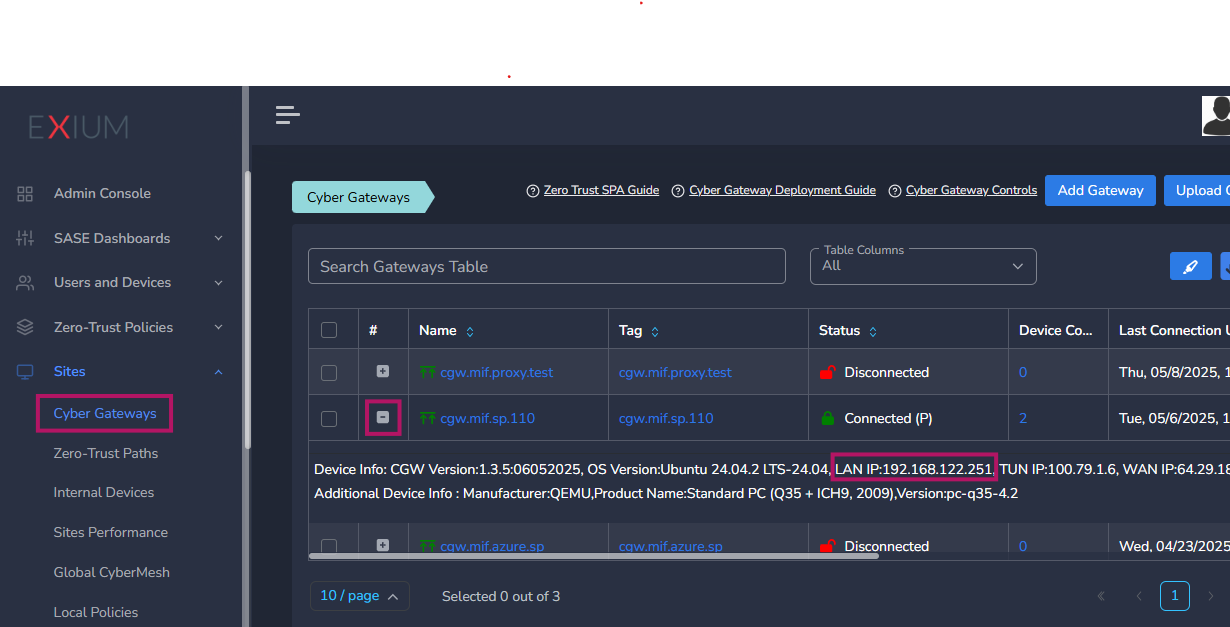
- Identify your CGW and click on the plus ‘+’ sign to get LAN IP details
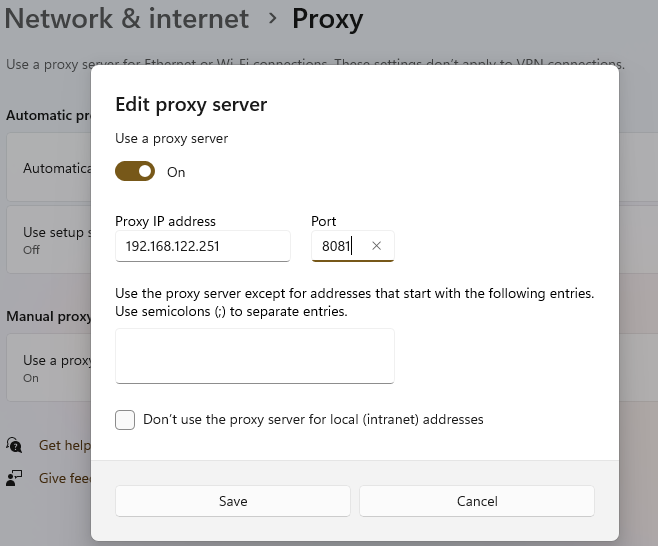
Configure proxy IP as: LAN IP of CGW and port: 8081
Example, if CGW LAN IP is 192.168.122.251 then configure like below example and save.
¶ Install Exium Root Certificate on the Devices
SSL decryption involves the interception and inspection of encrypted network traffic. To achieve this, it's essential to install a root certificate on devices. The root certificate acts as a trusted authority, allowing the SSL decryption device (Cyber Gateway) to re-encrypt and inspect the traffic before forwarding it to the destination server. Without the root certificate, devices may perceive the SSL decryption process as a potential security threat, resulting in warnings or blocked connections. Installing the root certificate on devices ensures that the SSL decryption process is transparent and maintains security while enabling organizations to effectively protect against threats and monitor network traffic.
¶ Deploying Root CA Certificate via RMM /Intune
You can use the following procedure to push down Exium's Trusted Root CA Certificate.
- Download Exium trusted Root CA Certificate .cer file on your computer.
- We recommend installing root certificate using a remote management tools such an RMM or Intune. For example, see instructions for Installing Exium Trusted Root CA Certificate using Microsoft Intune.
- On windows machine, you can use Distribute Certificates to Client Computers by Using Group Policy.
¶ Deploying Root CA Certificate Manually
In your browser, add the Exium certificate by downloading Exium trusted Root CA Certificate .cer file on your computer. We provide instructions by starting the process via the Google Chrome browser. The process is similar for other browsers.
- Open a Google Chrome browser.
- Navigate to Customize and control Google Chrome > Settings.
- Click Security from the Privacy and security pane.
- Click Manage certificates, and then Import.
- Click Next in the Certificate Import Wizard window.
- Click Browse and select the Exium trusted Root CA Certificate .cer file that you downloaded, and then click Next.
- Select the Place all certificates in the following store option to store the CA securely.
- Click Browse, and then select Trust Root Certification Authorities as certificate store.
- Click OK, and then Finish.
You have imported the CA into the Google Chrome browser.
Note you should put the certificate in the Trusted Root Certificate Category and select Accept (Yes) on the pop-up, as shown on the screenshot below.