¶ Introduction
Network security is paramount in today’s digital landscape. With the growing need to protect sensitive data, ensure compliance, and prevent unauthorized access, having a reliable and flexible access control mechanism is essential.
Exium's SASE NAC solution leverages a client-driven Captive Portal Detection (CPD) approach—supported by most modern operating systems and browsers—as well as a gateway-driven Captive Portal Identification (CPI) method in line with RFC 8908 and RFC 8910. Together, these standards enable accurate and seamless detection of captive network environments.
This Network Access Control (NAC) solution enforces authentications for all devices attempting to access the network. Upon connecting, users are redirected to a captive portal where they must authenticate using valid credentials and an OTP (One-Time Password) sent to their registered email or mobile number. Only after successful authentication is Internet access granted.
This document outlines the benefits and features of our NAC solution using CPD and CPI, and provides step-by-step guidelines on how to enable it on your gateways.
¶ The Challenge
Organizations face the constant challenge of preventing unauthorized access to their networks. With the increasing diversity of devices and user mobility, ensuring that only authorized personnel and trusted devices gain access is a complex task. A breach can have serious consequences, including data loss, compliance violations, and reputational damage.
¶ The Solution: Network Access Control (NAC)
Solution addresses these challenges by offering dynamic, policy-driven access control for wired and wireless networks. Key benefits include:
|
No |
Key NAC Features |
|---|---|
| 1 | Enhanced Network Security: It enforces authentication and authorization policies, allowing only authenticated devices and users onto the network. This reduces the risk of unauthorized access and potential breaches. |
| 2 | Guest Network Isolation: Easily segregate guest users, preventing them from accessing sensitive internal resources while still providing internet access. |
| 3 | Compliance and Audit Trail: Maintain compliance with industry regulations and internal policies by tracking and auditing network access. |
| 4 | Flexible Policies: Tailor access policies based on user roles, device types, or specific network segments, allowing for granular control. |
| 5 | Network Visibility: Gain insights into connected devices, their status, and activities on the network, enabling rapid threat detection and response. |
¶ How NAC works in Exium's SASE Platform
Here's how it works:
User Authentication: Captive Portal Detection (CPD) is supported by most modern operating systems and browsers. When a device connects to the network, the OS or browser automatically initiates an HTTP request (typically over port 80) to probe for Internet access. If a captive portal is detected, the device is redirected to the authentication portal.
Captive Portal Identification (CPI), as defined in RFC 8908 and RFC 8910, allows the gateway to proactively inform the client about the presence of a captive portal, improving detection reliability and user experience.
Start authentication process: The user or device attempting to connect initiates the authentication process by sending its credentials to the Cyber Gateway. Upon submitting a valid username, an OTP (One-Time Password) is sent to the user's registered email or mobile number. After successful OTP verification, the user is granted Internet access.
Cyber Gateway: The Cyber Gateway receives the credentials and acts as the intermediary between the user or device and the authentication server. It is responsible for relaying authentication requests and responses between the user or device and the authentication server.
Authentication Server: The authentication server which runs in Exium's CyberMesh cloud is responsible for verifying the user or device's credentials.
Authentication Exchange: The authentication server validates the user or device credentials. If the credentials are correct, the authentication server sends an authentication success message to the Cyber Gateway. If the credentials are incorrect, an authentication failure message is sent.
Access Control: Based on the authentication result, the Cyber Gateway makes a decision regarding network access. If the authentication is successful, the Cyber Gateway permits network access for the user or device. If the authentication fails, network access is denied.
Logging and Monitoring: The NAC system includes logging and monitoring features that record authentication and access events. This information is valuable for security analysis, compliance reporting, and auditing.
Exium's NAC solution is a powerful tool for network security because it ensures that only authenticated and authorized users and devices can access the network.
For the NAC solution to work, the DHCP server must be enabled on the Cyber Gateway. This ensures that client devices receive proper IP configuration and are directed to the NAC system for authentication.
¶ Configure/Enable NAC
First make sure, you have Modern Workplace security enabled in your workspace.
To configure NAC, follow the steps below.
- Navigate to the MSP admin console -> Client Workspace
- Click on Sites → Cyber Gateways in the left menu bar → Add Gateway
- Currently you cannot enable NAC for existing Cyber Gateways. It will disrupt Internet services for all users connected to Network.
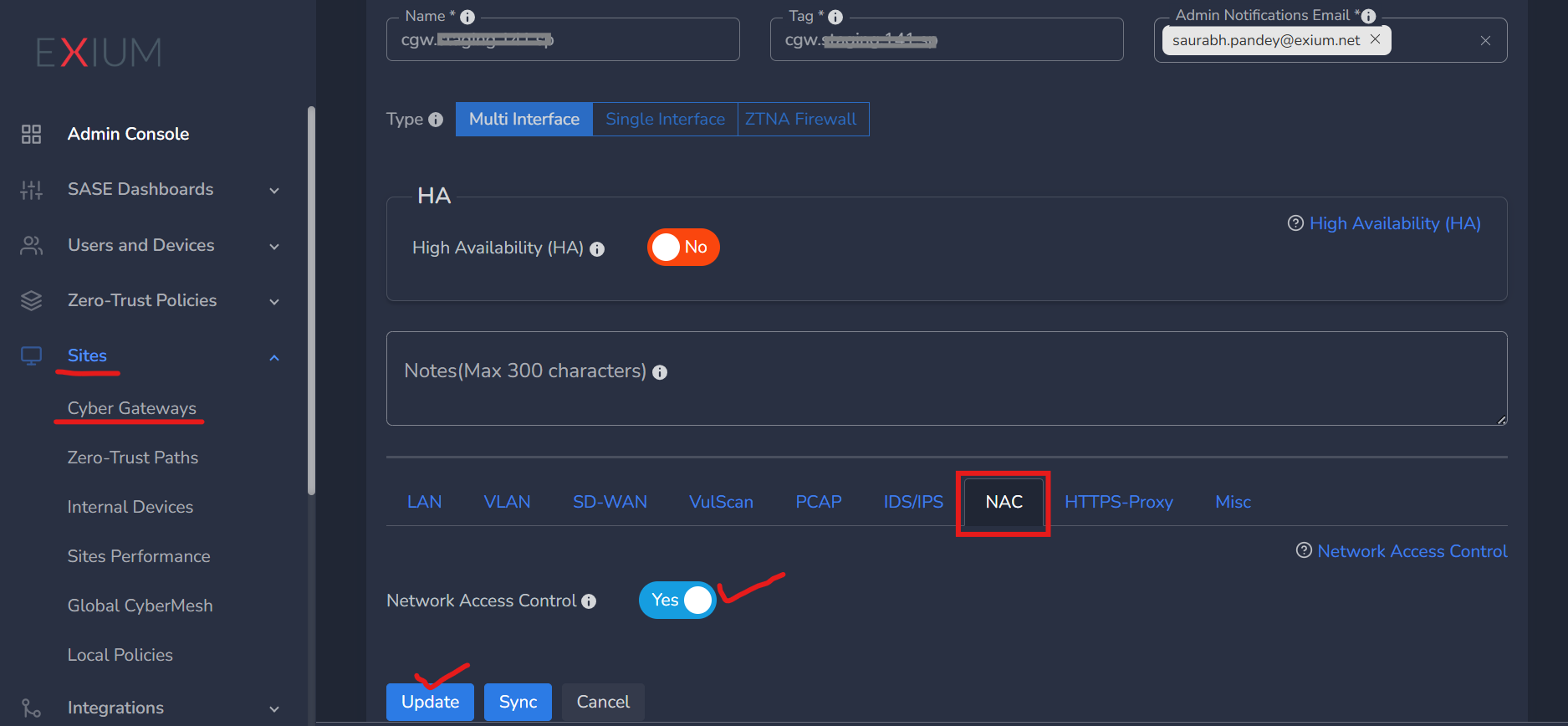
- Under configuration section, click on NAC tab, and toggle Network Access Control button to Yes
- Continue configuring other parameters if required and once done, click “Save/Update”
- Please follow the instructions for Multiple interface CGW deployment for other configuration parameters and deployment options
¶ Testing NAC?
Once NAC is enabled, all devices behind the gateway will be required to complete an authentication process before being granted Internet access.
¶ How It Works
On user devices behind CGW, follow below steps:
IP Assignment via DHCP
The Cyber Gateway must have DHCP enabled. When a device connects, it receives an IP address from the Cyber Gateway.
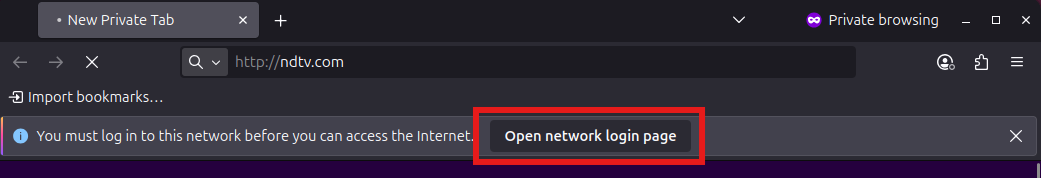
Captive Portal Redirection
After IP assignment, any attempt to access an HTTP website will automatically redirect the user to the Captive Portal login page.
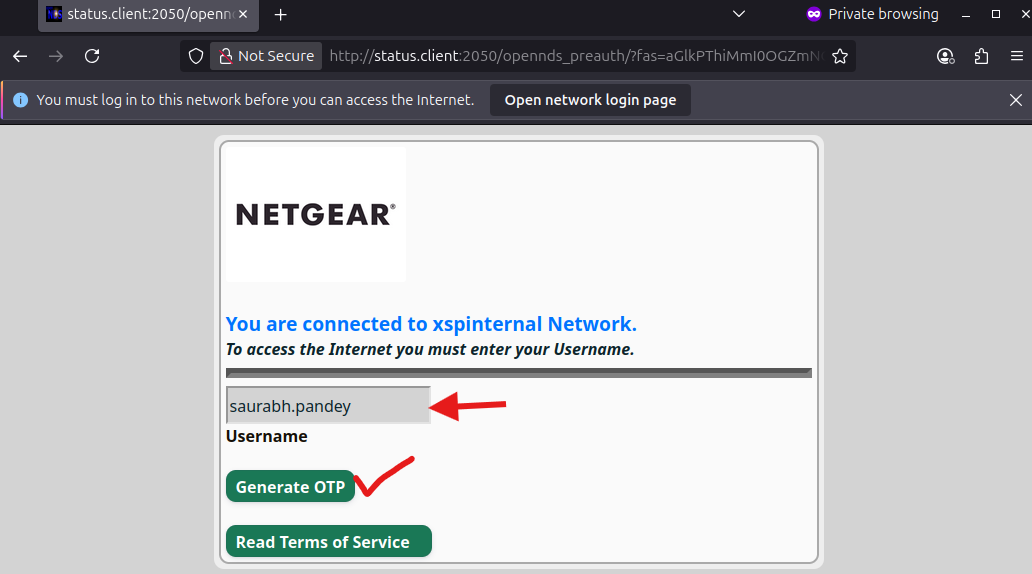
Username Entry
The user must enter a valid Username (for e.g., mike.johnson) that is registered in the Exium's SASE Admin Console.
Click on Generate OTP
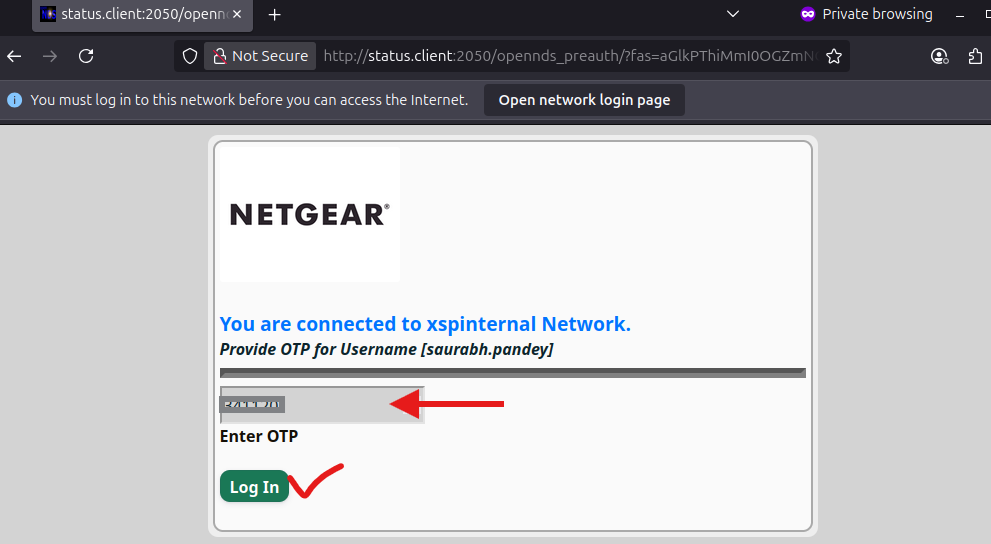
OTP-Based Authentication
If the username is valid, an OTP (One-Time Password) is sent to the user's registered email or mobile number.
The user must enter the correct OTP to complete authentication. Click on Log In
Access Control
Upon successful OTP verification, Internet access is granted.
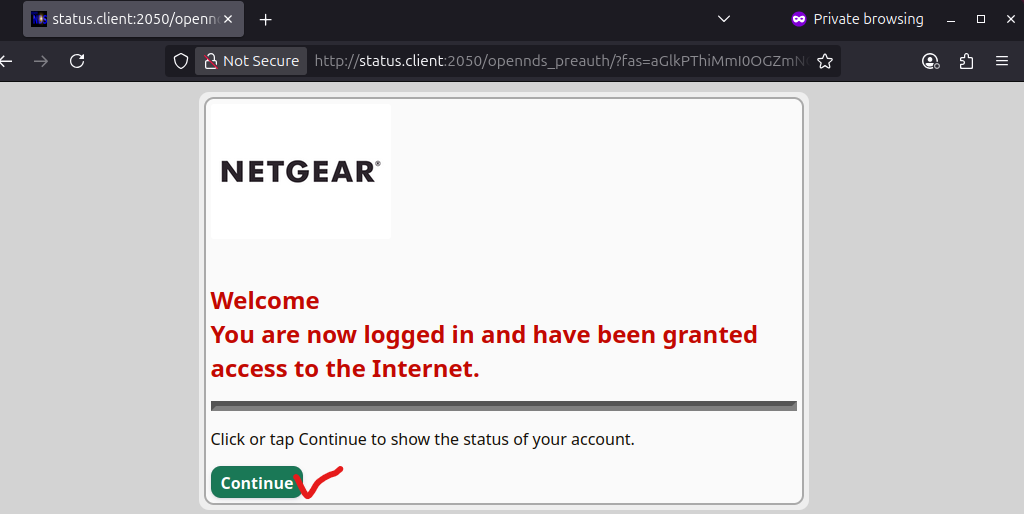
Users are allowed a maximum of three attempts to enter the correct OTP. If all attempts fail, the user will be redirected back to the login page.
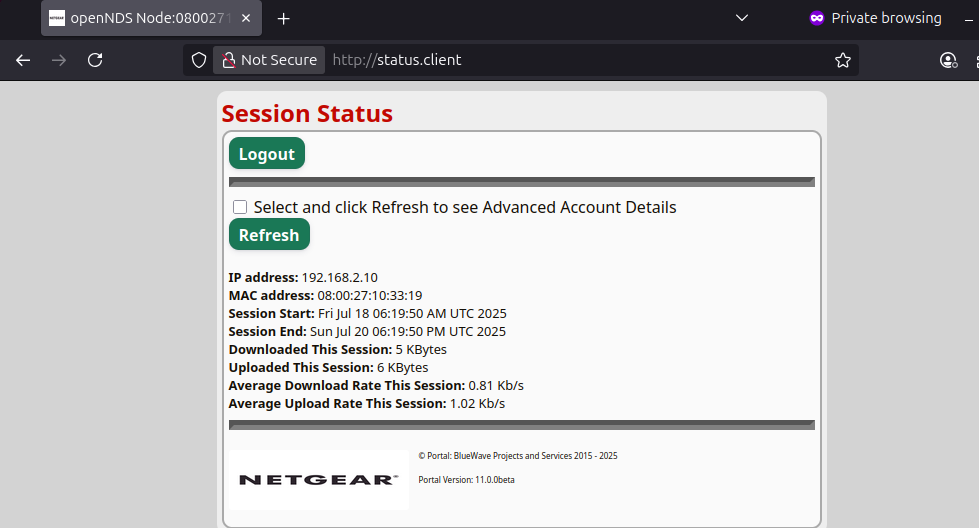
After clicking on Continue button, user device session status will be displayed.
¶ Summary
Network Access Control is a fundamental component of modern network security. By controlling and monitoring access based on user and device authentication, organizations can dramatically improve their security posture. It ensures that only authorized users and trusted devices connect to the network, mitigating the risks associated with unauthorized access and data breaches.
To learn more about implementing Network Access Control in your organization and explore tailored solutions that fit your unique requirements, contact Exium at hello@exium.net for a consultation or demonstration.