¶ Overview
The overlap between private subnets used in a company’s private network and those commonly found in home WiFi networks can create significant challenges for remote access, particularly for employees who need to use devices on both networks concurrently. Exium offers insights and recommendations for mitigating these issues to ensure seamless connectivity and secure access.
¶ The Issue of Subnet Overlap
When a company’s private network shares subnets with home networks, users may encounter routing conflicts that hinder access to resources. For example, if a company uses a subnet such as 192.168.0.0/24, which is also frequently used in domestic settings, remote users face limitations in accessing both local devices (e.g., printers) in their home network and resources on the company’s private network simultaneously.
¶ Optimal Subnet Configuration
To avoid such conflicts and ensure effective use of Exium’s Zero Trust Network Access (ZTNA) technologies, organizations should adopt distinct private subnets. Here’s an example of a conflict-free setup:
Company Private Subnets:
- 192.168.110.0/24
- 10.20.150.0/24
Common Home Subnet:
- 192.168.0.0/24
This configuration allows users to access both local devices on their home network and resources on the company’s private network without routing conflicts.
¶ Recommendations for Avoiding Overlap
To prevent overlap between company private networks and typical home networks, the following subnet ranges should be avoided for corporate use:
- 192.168.0.0/24
- 192.168.1.0/24
- 10.0.0.0/24
- 10.0.1.0/24
These subnets are commonly used by most WiFi routers and can lead to connectivity issues when employees work remotely.
¶ Mitigation Strategies for Existing Overlaps
In cases where it is not feasible to restructure existing subnets to avoid overlap, Exium provides two options: force local subnet through the tunnel and support for the overlap subnet.
¶ Force local subnet through the tunnel
By leveraging secure tunneling provided by Zero Trust Network Access (ZTNA), the company’s private network (Zero TrustPaths defined in Exium's central admin console) traffic can be forced through the secure tunnel, allowing remote users to access company resources. While this ensures security, users may be unable to access local devices on their home networks.
¶ Overlapping Subnet Support
Exium offers a solution for situations where users prefer not to alter their home network subnet that overlaps with a remote or office network. This solution allows an admin to designate a unique network subnet not used within the office environment and configure it as a trust path in the admin console. During the creation of a trust path, the admin can select a Forwarding Subnet that overlaps with the user's home network.
For example, if both the user's home and office networks use the subnet 192.168.0.0/24, the following configuration lets them access office resources without altering their home network subnet.
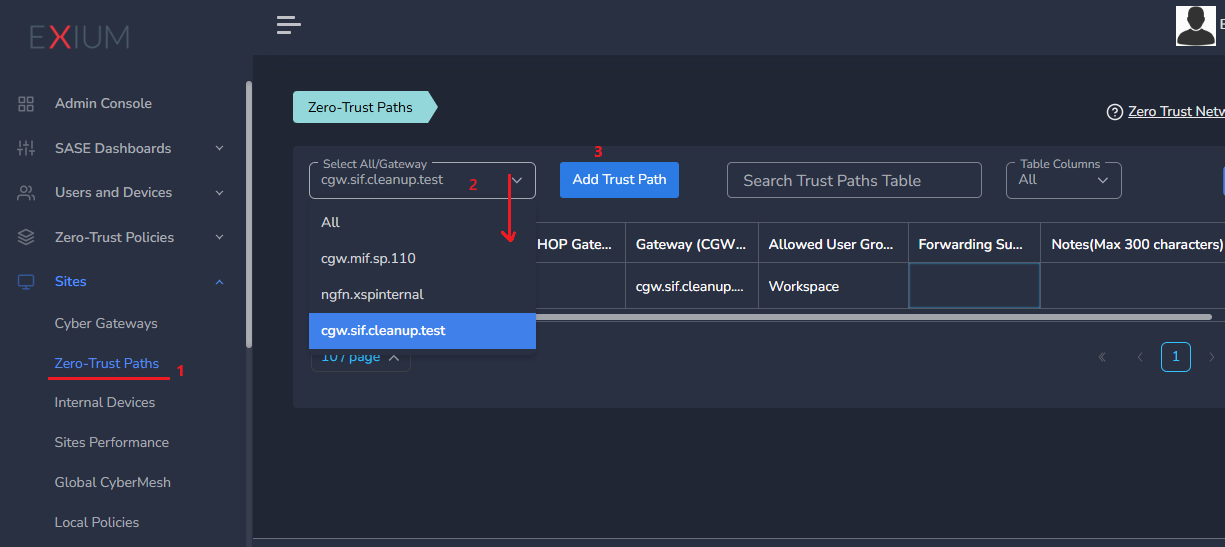
¶ Step 1: Log into the Admin Console and Create a Trust Path
- Navigate to the MSP admin console and go to Companies.
- Click on Gateways in the left menu bar and then select Trust Paths.
- Choose a gateway from the dropdown and click on Add Trust Path.
¶ Step 2: Enter the unique Unused subnet
- Enter a unique network subnet in Network Destination that is unused within the office network.
- In Forwarding Subnet, select the actual subnet or office/remote trust path that requires mapping or forwarding.
- Save the configuration.
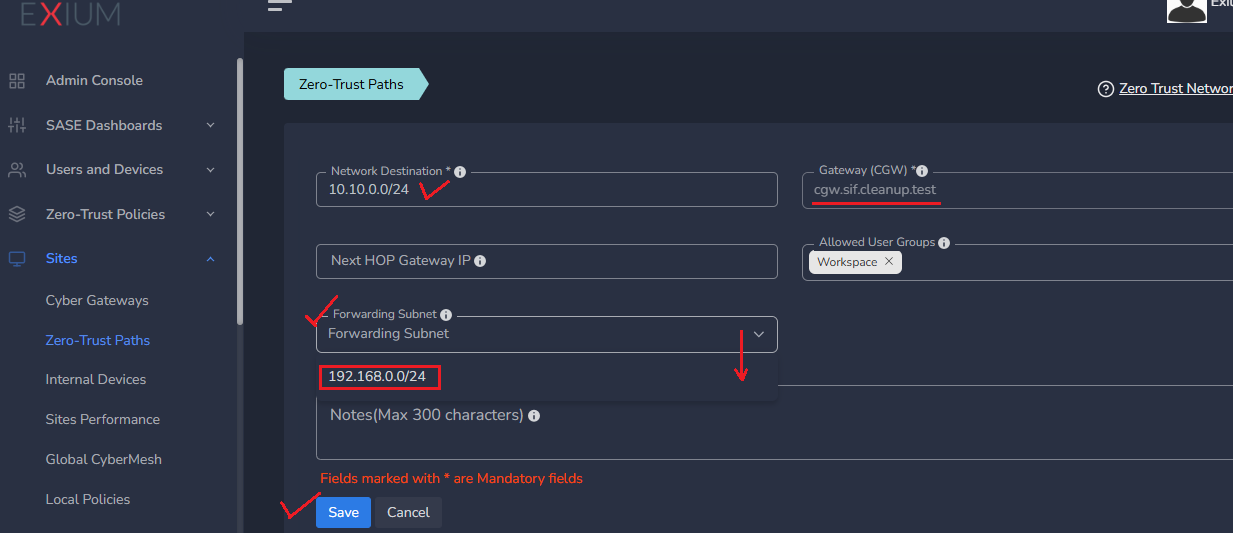
After a few minutes, the cyber gateway will set up rules/policies to map the 10.10.0.0/24 subnet to 192.168.0.0/24. Once configured, the IP range 10.10.0.0/24 will directly correspond to the range 192.168.0.0/24.
Now, users with overlapping subnets can access office resources using the mapped IP addresses. For instance, to access a private office resource with the IP 192.168.0.100, a user with an overlapping subnet should use the IP 10.10.0.100.
The new trust path subnet and the actual office trust path subnet must have the same network mask. For example, if the office network has a subnet of 192.168.0.0/22, the forwarding configuration must be set with a unique subnet also using a /22 subnet, such as 10.10.0.0/22.
¶
Step 3: Set Up Local DNS Entries
Set up the local DNS entries for the new subnet by consulting the guide: Enhancing Security with Exium’s SASE Solution through DNS Security and Private DNS Servers. If the private domain app1.local was previously associated with the IP 192.168.0.100, it can now be linked to the new subnet IP 10.10.0.100.
Alternatively, you can maintain the association of the private domain app1.local with the IP 192.168.0.100, while connecting a new domain, alt.app1.local, to the new subnet IP 10.10.0.100. In this manner, users with overlapping local subnets can access the same application through a different private domain name.
¶ Conclusion
To enhance user experience and maintain seamless connectivity between home and company networks, it is imperative to carefully plan and allocate subnets within the organization. By following the recommendations to avoid common home WiFi subnet ranges and implementing best practices for network design, businesses can empower users with the ability to effectively manage both personal and professional resources without conflict, all while utilizing Exium’s advanced security protocols. Proper subnet management not only facilitates remote access but also strengthens the integrity and security of corporate resources.
To learn more about implementing SASE, XDR, IAM/ MFA, and GRC for your organization and explore tailored solutions that meet your unique requirements, contact Exium at partners@exium.net for a consultation or demonstration. If you are ready to get started, check out our testing and onboarding process.