¶ Zero Trust Network Access Control
Zero Trust Network Access Control offers a transformative approach to securing private applications and sensitive data. By focusing on identity-based access, continuous verification, and least privilege principles, organizations can effectively mitigate security risks, enable user mobility, and achieve compliance while maintaining operational efficiency.
ZTNA is crucial for modern enterprises navigating the evolving threat landscape and the demands of remote and cloud-based work environments. You can configure and apply ZTNA policies in the centralized admin console for Cyber Gateways
Exium enables workspace admins with multiple options to configure ZTNA policies. ZTNA policies are defined in the central admin console and applied in the Exium Cloud CyberMesh platform. Admins can configure Zero-Trust paths to provide access to all services in a network or limited access to specific services in a network.
The architectural representation of Zero Trust Network Access (ZTNA) below illustrates remote users gaining access to a private network with various subnets, all governed by Zero Trust policies. Each remote device installs an agent, while a cyber gateway is deployed within the private network.
Subnets (also called Trust Paths due to the Zero Trust controls in place) that are directly accessible (highlighted in green) on Layer 2 from the cyber gateway do not require the configuration of a Next Hop Gateway IP. Conversely, if certain local subnets within the private network are not directly accessible (highlighted in blue) on Layer 2 from the cyber gateway, specifying a Next Hop Gateway IP is necessary, as detailed in the below table.
|
Trust Path (Destination Subnet) |
Next Hop Gateway IP Address |
|
|---|---|---|
| 1 | 10.10.120.0/24 | Not applicable |
| 2 | 192.168.110.0/24 | Not applicable |
| 3 | 10.10.115.0/24 | Not applicable |
| 4 | 10.20.150.0/24 | 10.20.150.1/24 |
| 5 | 10.30.150.0/24 | 10.20.150.1/24 |
¶ Configuring Zero-Trust Paths and Next Hop Gateway
- To enable Zero-Trust Network Access for every local subnet at a site where a CyberGateway is deployed, each subnet must be designated as a trust path via the admin console.
- In Multi-Interface CyberGateway setups, any LAN and VLAN settings added during the creation or updating process in the admin console automatically integrate as trust paths.
- For Single-Interface CyberGateway setups, the local subnet where the CyberGateway is deployed becomes the default trust path.
- Additional LAN subnets at a site must be configured as trust paths to maintain Zero-Trust Network Access for remote users and connected sites.
- If LAN subnets are not directly accessible on the L2 network, configuring a Next Hop Gateway IP is required.
- If LAN subnets are directly accessible on the L2 network, configuring a Next Hop Gateway IP is not necessary.
Following the steps below to configure a trust paths and next hope gateway IP address (if needed). Note that these steps can be completed when you are deploying a new cyber gateway or configuring new trust paths for an existing cyber gateway.
¶ Step 1: Login to the admin console and Create Trust Path
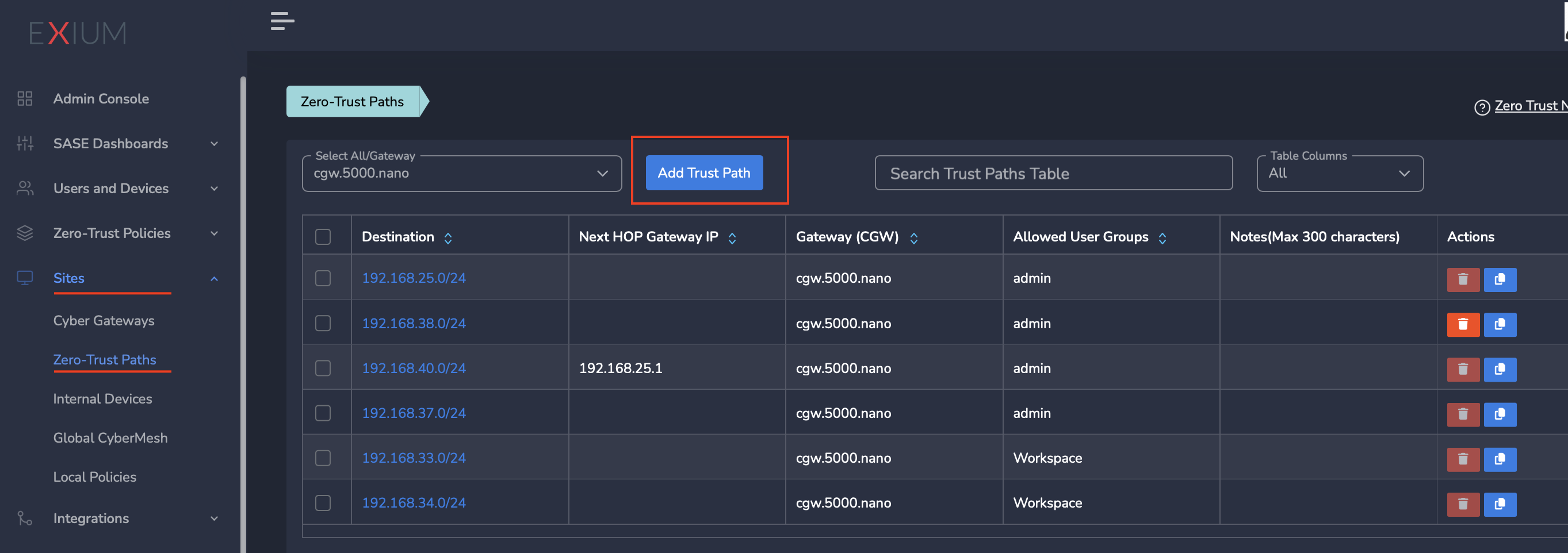
- Navigate to the MSP admin console -> Companies
- Click on Gateways in the left menu bar and Click on Trust Paths
- Select a gateway from drop down and click on Add Trust Path
- Enter LAN network subnet in Network Destination
¶ Step 2: Specify Next HOP Gateway IP (if needed) and User Group(s)
- if network subnet is reachable on L2, skip Next HOP Gateway IP.
- if network subnet is reachable via a Gateway, enter that IP as Next HOP Gateway IP ( as showing in picture)
- and select the workspace in Allowed User Groups. If you want to allow only specific groups to have access please add them.
- Click on Save
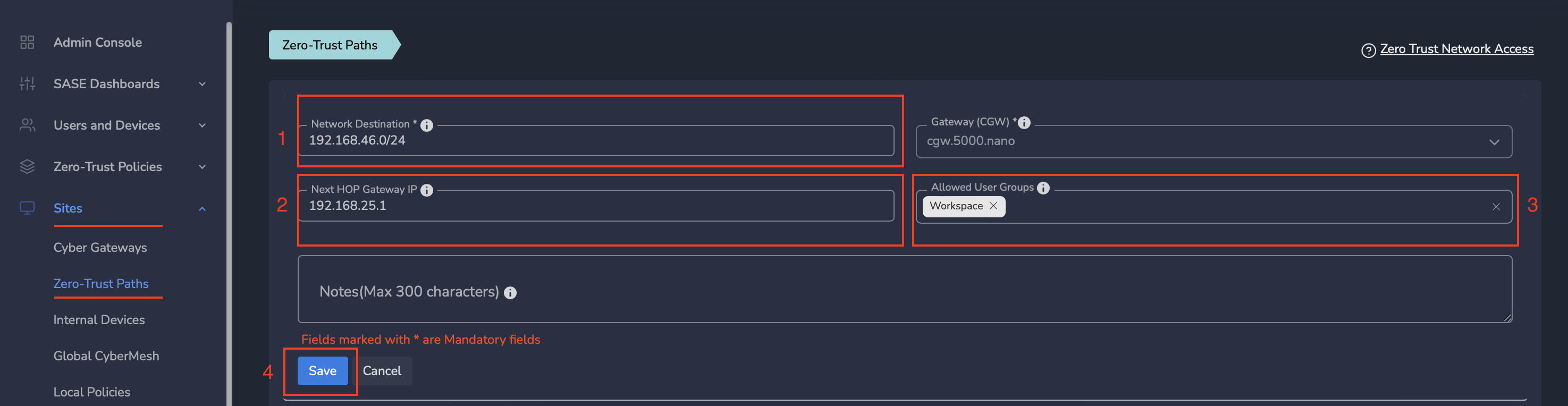
¶ Step 3: Secure Success
Congratulations! Your Trust path and the Next HOP Gateway IP is created as shown in the screenshot below.
For expert guidance on implementing SASE, XDR, IAM, and GRC solutions, reach out to Exium at partners@exium.net. If you are ready to get started, check out our testing and onboarding process.