¶ Introduction
In today's complex cybersecurity landscape, organizations require proactive measures to detect and mitigate threats. Intrusion Detection Systems (IDS) and Intrusion Prevention Systems (IPS) are crucial components of a comprehensive security strategy.
¶ Challenges
Evolving Threat Landscape: Cyber threats are constantly evolving, becoming more sophisticated and harder to detect.
Data Security: Protecting sensitive data from unauthorized access and breaches is a top priority for organizations.
Compliance Requirements: Many industries are bound by regulatory requirements that mandate robust security measures.
Balancing Network Performance: Ensuring security without sacrificing network performance and user productivity is an ongoing challenge.
¶ Solution: IPS and IDS
An IDS is designed to provide an alert about a potential incident, which enables a security operations center (SOC) analyst to investigate the event and determine whether it requires further action. An IPS, on the other hand, takes action itself to block the attempted intrusion or otherwise remediate the incident.
¶ Intrusion Detection System (IDS)
|
Feature |
Description |
|---|---|
| Traffic Monitoring | IDS continuously monitors network traffic for unusual or suspicious patterns, such as known attack signatures or anomalies. |
| Alert Generation | When potential threats are identified, IDS generates alerts to notify security teams, allowing for investigation and response. |
| Packet Analysis | Deep packet inspection and analysis provide visibility into network traffic, enabling the identification of malicious activities. |
| Logging and Reporting | Maintain logs and reports to document detected intrusions and support compliance requirements. |
| Anomaly Detection | Some IDS solutions employ machine learning and behavioral analysis to detect previously unknown threats. |
¶ Intrusion Prevention System (IPS)
|
Feature |
Description |
|---|---|
| Real-time Threat Blocking | IPS goes beyond detection and actively blocks suspicious traffic, preventing threats from reaching their targets. |
| Policy Enforcement | Define security policies to enforce access control, block malicious activities, and filter traffic based on rules |
| Signature-Based Protection | Employ signature-based mechanisms to recognize known threats and block them in real-time. |
| Content Filtering | Filter content for malware, exploits, and malicious payloads to prevent their entry into the network. |
| Traffic Shaping | Balance network performance and security by controlling bandwidth usage and application access. |
¶ Benefits of IDS and IPS
Enhanced Security: IDS and IPS work together to detect and prevent a wide range of cyber threats, reducing the risk of data breaches and network compromises.
Compliance: Support regulatory compliance by maintaining detailed logs, which are essential for auditing and compliance reporting.
Proactive Threat Mitigation: IPS goes beyond detection to proactively block threats, reducing the potential impact of security incidents.
User Productivity: Balance security with network performance, ensuring uninterrupted business operations.
Reduced Risk: Minimize the risk of unauthorized access, data breaches, and potential data loss.
Intrusion Detection System (IDS) and Intrusion Prevention System (IPS) are essential components of Exium's Workplace security offering delivered by our cyber Gateway. By identifying and preventing security threats in real-time, we help organizations protect their digital assets, ensure compliance with regulatory requirements, and maintain a strong security posture in the face of ever-evolving cyber threats.
¶ Enabling IDS in the Multi Interface Cyber Gateway
Exium's Multi Interface Cyber gateway initially supports only IDS features.
To configure IDS for a new Cyber Gateway deployment, follow the steps below.
¶ Step 1: Open the Cyber Gateway Configuration Page
- Navigate to the MSP admin console -> Client Workspace
- Click on Sites → CyberGateways in the left menu bar → Add Gateway if deploying a new CGW
- If this is for a new cyber gateway deployment, follow the instructions for Multiple interface CGW deployment
- For updating existing CyberGateway click on CyberGateway in list to update configuration
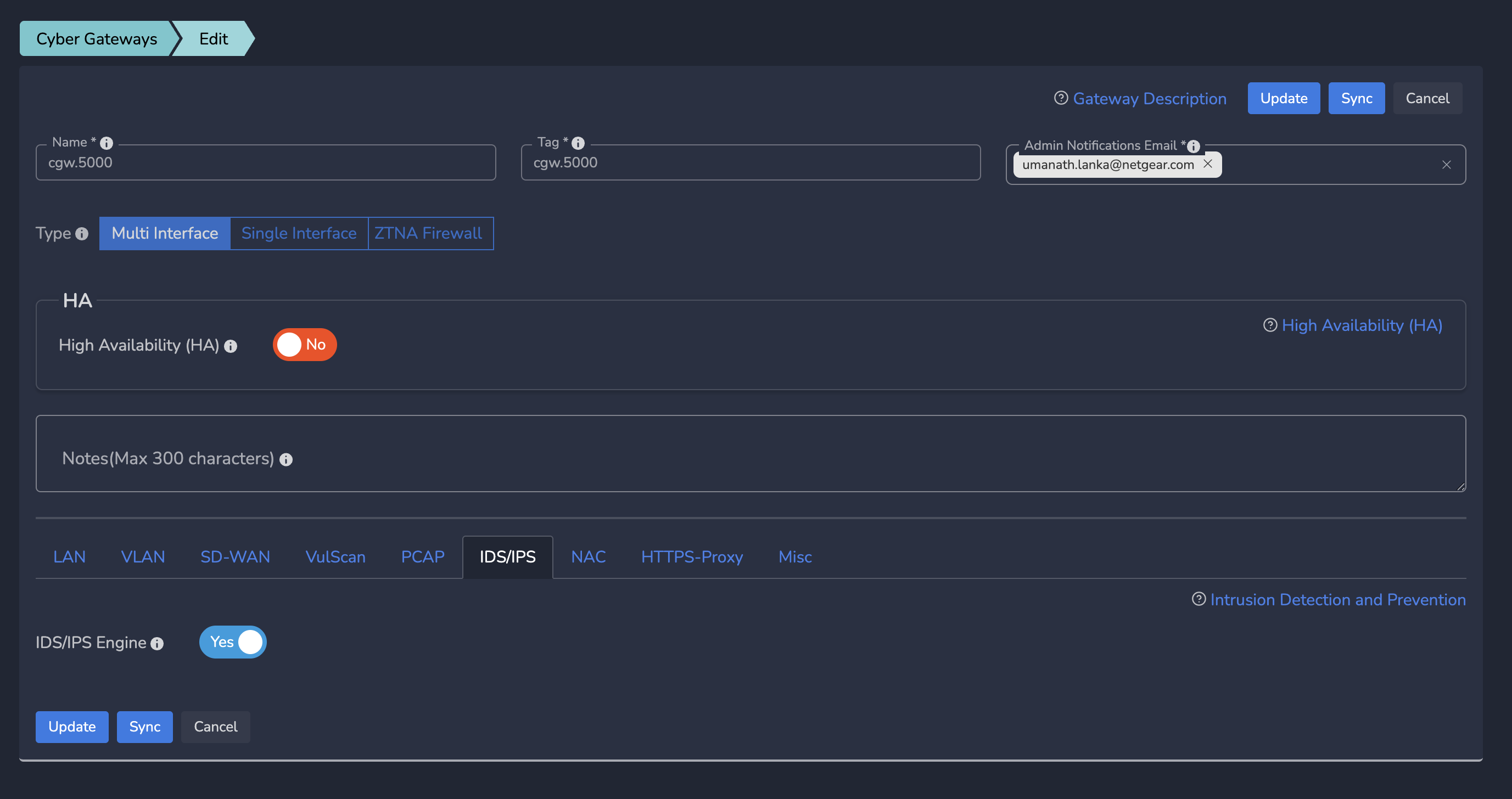
¶ Step 2: Enable IDS
- Go to IDS/IPS Tab for CyberGateway
- Toggle IDS/IPS Engine switch to “YES” , click “Update”
¶ Unlocking the IDS/ IPS Dashboards
To unlock the IDS/ IPS Dashboards, follow the steps below:
¶ Step 1: Get Your Login Credentials
- Navigate to the MSP admin console → Companies → Click on Company name (or directly go to the Customer/ Client Workspace Sign In)
- Click on “XDR” in the left menu bar → Login → copy the password in the line “Dashboard”
¶ Step 2: Login to the XDR360 Console
- Username is the same as the workspace name (for example, "exiumngcnusa" in the screenshot below)
- Click on “Dashboard” in the left menu-bar → Login with the username and the password you copied in Step 1
¶ Step 3: Launch the XDR360 Dashboards
- After logging in, you will land on the main dashboard page from where you can navigate further.
- Click on “Threat Hunting”
¶ Step 4: Advanced Filtering of the “IDS” Alerts and Events
- Click on “Add Filter”
- Select rule.groups:ids as show in below → Save
¶ Step 5: Explore the “IDS” Alerts and Events
- Scroll down in the “Threat Hunting” Dashboards to see the details on the “IDS” Alerts and Events
- You can expand the alert/ event details by clicking on the arrow on the left of the event line
¶ Step 6: Filtering “IDS” Alerts and Events for a Site (Cyber Gateway)
- After you filtered results for the “IDS” as in the previous step, you can narrow down to a given cyber gateway or site Alerts
- Click on “Add Filter”
- Select agent.name:"cyber gateway or site name" as show in the screen shot → Save
To learn more about implementing SASE, XDR, IAM, and GRC for your organization and explore tailored solutions that meet your unique requirements, contact Exium at partners@exium.net for a consultation or demonstration. If you are ready to get started, check out our testing and onboarding process.