¶ Introduction
With 63% of enterprises, 92% of industrial organizations and 82% of health care organizations using IoT, almost every company is exposed to cyber-attacks. IoT devices make life easier for businesses. Unfortunately, connecting IoT devices to the network extends the attack surface which provides more entry points for hackers. Many of the IoT devices currently deployed are running on unpatched software, are misconfigured, or use unsecured communication protocols, which makes them extremely vulnerable and easy to hack. Organizations require these devices to enable their business, yet they cannot trust them. IoT devices pose immense cybersecurity risks as they are largely unregulated. In fact, majority of these devices, which often ship with their own vulnerabilities, are susceptible to medium- or high-severity attacks. It is especially concerning when they are network-connected with unfettered access.
Security teams, rarely involved in purchasing, find it extremely challenging to secure these devices due to their incredibly diverse types, long lifecycles, and lack of coverage from traditional security controls.
Most traditional security products can’t see these devices and the ones that can often don’t know what to do with them because they can’t identify them accurately. You need more than just an IP address to tackle threats in a way that’s effective but not disruptive to critical equipment like medical and manufacturing devices.
Current IoT security solutions limit their visibility to manually updated databases of known devices, require single-purpose sensors, lack consistent prevention, don’t help with policy creation, and can only provide enforcement through integrations. All this leaves security teams with heavy lifting, blind to unknown devices, and unable to scale their operations, prioritize efforts, or minimize risk.
¶ Protect Every Device on Your Network
As an integral part of Cyber Gateway (CGW) and CyberMesh platform, Exium ensures IoT and OT devices connecting to your network are secure and protected against cyberattacks that can infect your extended business.
Without any agents or additional hardware, the Exium platform uses the existing infrastructure to discover and identify every device in any environment—enterprise, medical, industrial, and more. The platform analyzes device behavior to identify risks and threats and provides continuous device risk assessments.
¶ Identify & classify devices in any environment.
Exium automatically discovers every connected device and collects comprehensive data on each. See granular details, such as manufacturer, model, version, operating system, location, applications, IP and MAC address, reputation, username, software, behavior, connections, risk factors, and more. View devices by type, such as all physical security devices or all network cameras. Drill down to view specific devices by model and version. Or view devices on specific VLANs or subnets. Exium also decodes more than 100 device and industry-specific protocols for analyzing the application-level behavior of each device. Our machine learning engine classifies each device based on its type and business function.
The platform also performs application-based discovery by looking at the software applications that use IoT devices as sensors, then following the path from the application to the specific devices. This provides additional information about configuration, usage, performance, and device relationships.
¶ Network Segmentation
The Exium platform reveals specific communication flows that each device requires to perform its function. Exium can dynamically apply segmentaiton policies, to ensure that devices can only interact with other necessary devices. For example, an HVAC system can communicate with a trusted smart-building controller using approved protocols while being blocked from communicating to the Internet or another HVAC system.
¶ Create policies for any unmanaged & IoT device
As the Exium platform discovers devices in the environment, it provides the Admin console granular device attributes like the manufacturer, model, operating system, MAC address, and more. It also provides a risk analysis based on contextual understanding of a device’s behavior in your environment.
In the Admin console, you can configure policies based on these attributes, and you can enable policy recommendations made by the Exium platform. This allows you to reduce your risk exposure proactively by ensuring your security gateway has policies for any device in your environment— policies that can react to changes in device attributes, behavior, and risk level.
For example, you can set granular rules that restrict devices from using unapproved protocols, applications, and communication patterns. You can also set policies to alert on anomalies in device behavior or communication patterns. And to avoid confusion or conflicts, Exium keeps policies for unmanaged and IoT devices separated from policies for your entire network.
¶ Detect and respond quickly to threats and vulnerabilities
Exium IoT security solution uses continuous device analysis to detect threats and vulnerabilities associated with unmanaged and IoT devices (i.e., CVE’s, unsupported operating systems, etc.). This analysis is based on information from Exium Device Knowledgebase and from premium, globally-shared threat intelligence feeds.
When the Exium platform identifies a vulnerable device, it can activate security protections automatically, either through virtual patching (by installing the appropriate IPS signatures on the gateways) or through policy enforcement that isolates affected devices. This provides effective protection against unpatched devices, or devices running on unpatchable operating systems and software, all without disrupting critical processes and business operations.
¶ Provide security teams comprehensive device information
Each device also is analyzed for potential risk to the organization. Exium identifies high-value devices, as well as those with vulnerabilities, recall notices, weak or open passwords, and indicators of compromise. Device behavior is analyzed to understand normal communication patterns. We can detect device interaction with known malicious IP addresses or domains. Anomalous device behaviors can be identified based on observed device and network baselines.
Security teams also can see the wealth of information the platform provides about each device directly in the admin console. With rich log records and dedicated IoT event reports, Exium gives security teams a contextual understanding of device behavior and forensics for event investigation. That helps make security teams more well-informed when responding to threats without impacting critical devices, and without ever leaving the admin console.
|
Discover and learn |
Zero-Trust segmentation |
Monitor and control |
Detect and respond |
|---|---|---|---|
| The Exium platform discovers and classifies every managed and unmanaged device in any environment—enterprise, manufacturing, healthcare, retail, and more. | Once the enterprise understands its IoT attack surface, IoT devices can be segmented into policy-driven groups based on their risk profiles. |
See and profile every device on the network, to understand what IoT devices are being deployed.
|
The Exium platform continuously analyzes device activity for abnormal behavior. Whether a device is misconfigured or is the target of an attack, the platform can alert your security team and trigger automated actions to help stop an attack. |
|
It works with your existing IT/security tools and network infrastructure to identify every device, including off-network devices that use Wi-Fi, Bluetooth, and other IoT protocols. |
The policy driven IoT groups and internal network segmentation enable monitoring, inspection, and policy enforcement based on the activity at various points within the infrastructure. | Control access to the network, both connecting to the network and determining where devices can access. |
Automatically detect policy violations, restrict access or quarantine suspicious or malicious devices. |
| This comprehensive device inventory includes critical information like device manufacturer, model, serial number, location, username, operating system, installed applications, connections made over time, and individual risk assessment scores. | Enforce zero trust policies to prevent unauthorized access and lateral movement | Monitor the devices on the network to ensure that they are not compromised and to take automatic and immediate action if they are. |
This automation provides peace of mind that an attack on any device—managed or unmanaged—can be stopped, even if your security team is busy with other priorities.
|
¶ Configuring IoT Security in Exium's SASE Platform
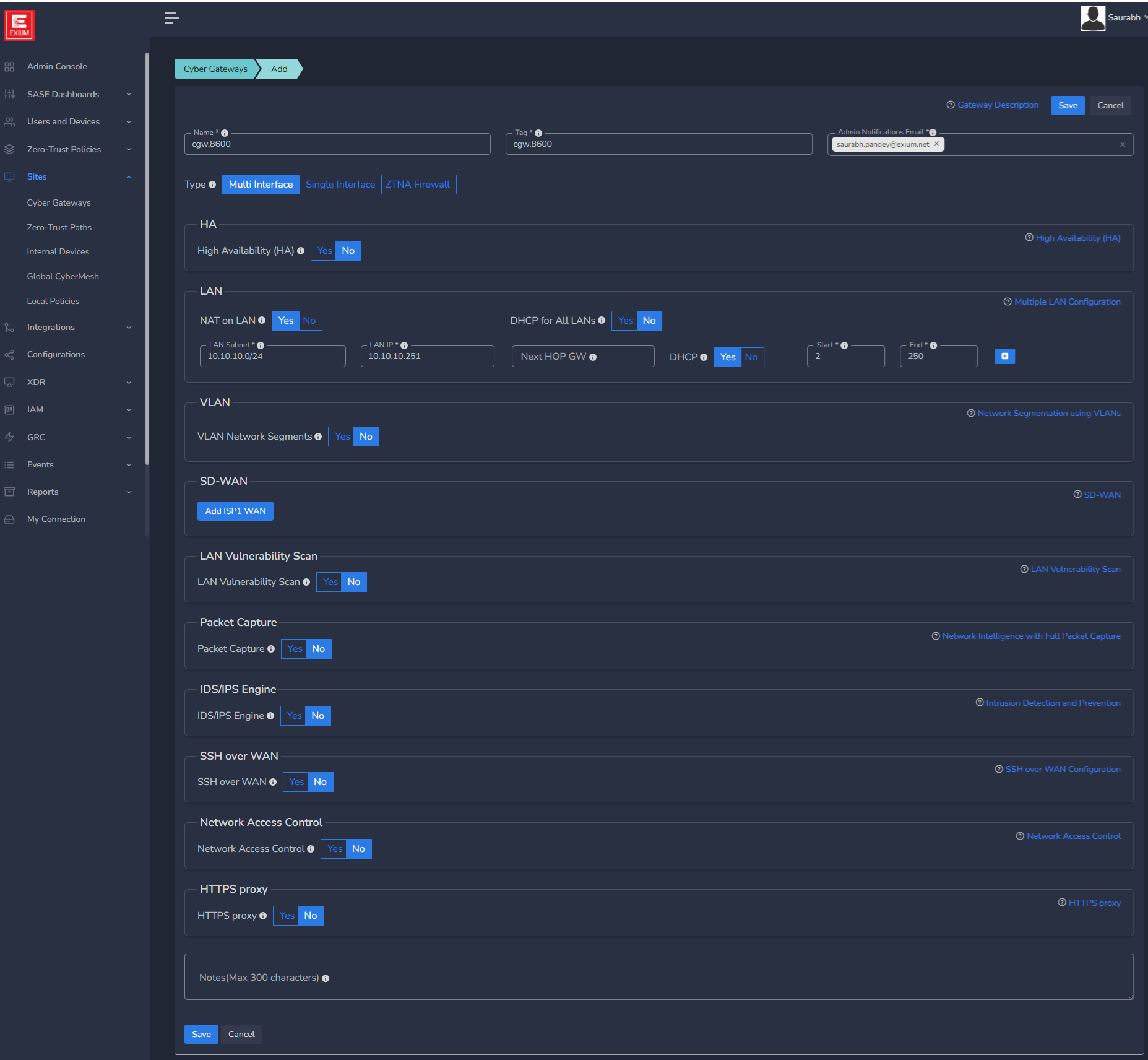
For IoT Security, you would need deploy Cyber Gateways (CGW) on each site, where you like to protect devices. You can create as many CGWs as you wish in the centralized admin console by following the steps below.
- Navigate to the MSP admin console -> Client Workspace
- Click on Sites → Cyber Gateways in the left menu bar → Add Gateway
- Select other options provided and save
- Follow the instructions for Multiple interface CGW deployment
- Repeat the process for each CGW, Note you can use the copy button in the cyber gateway list to copy similar configurations for the other cyber gateways your are deploying after the first one. You would just need to give each cyber gateway a unique name.
¶ Unlocking IoT/ OT Device Visibility in Exium's SASE Platform
There are two options for device visibility:
- Specific site level devices
- All sites' devices
¶ View Site Level Internal / Network Devices
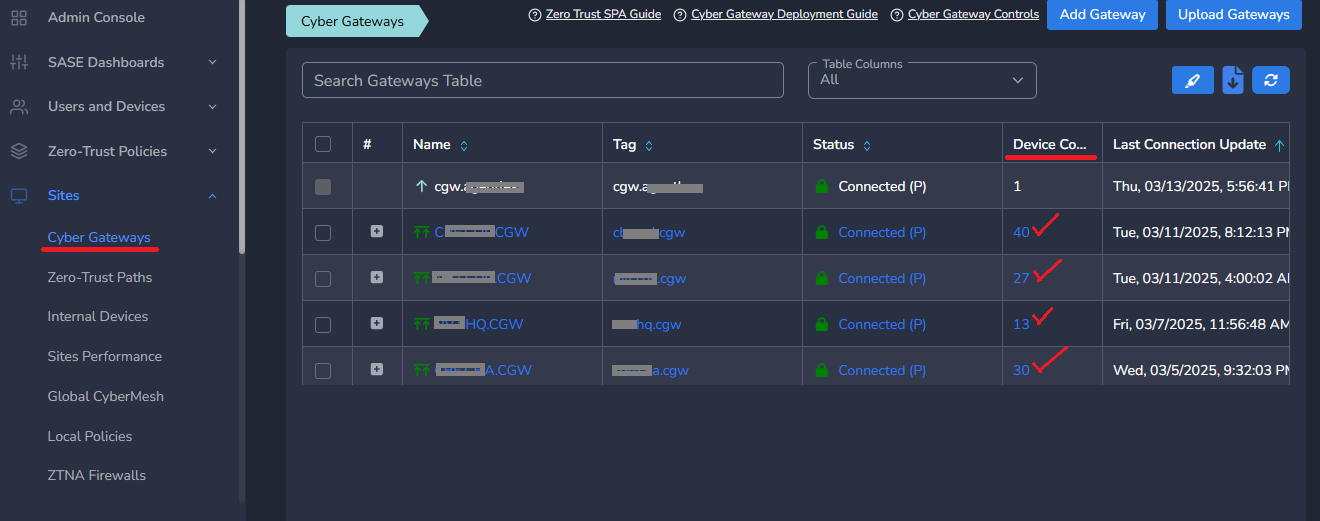
Follow below steps to view the devices behind CGWs:
- Navigate to the MSP admin console -> Client Workspace
- Click on Sites → Cyber Gateways in the left menu bar
- Column Device Count will show devices behind each CGW deployed in your network
- To view details, click on the number showing in Device Count column
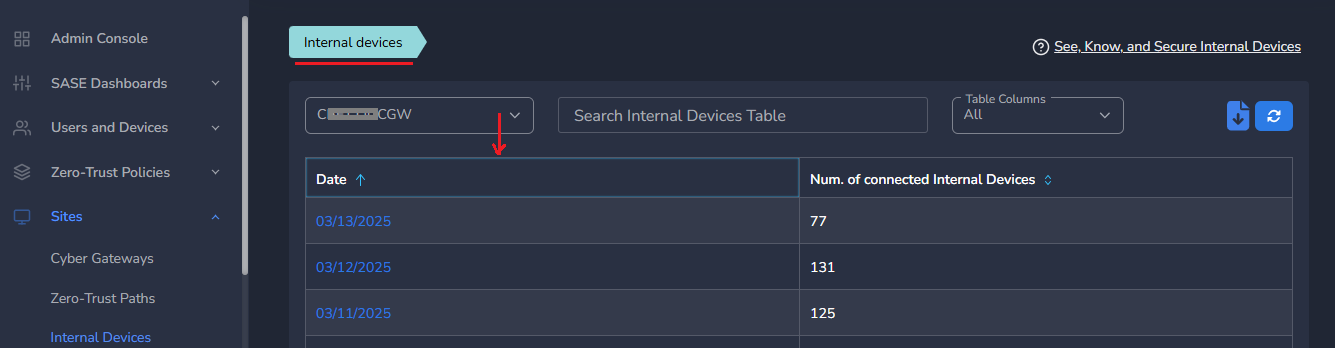
- On Internal Devices Page, device count can be seen datewise
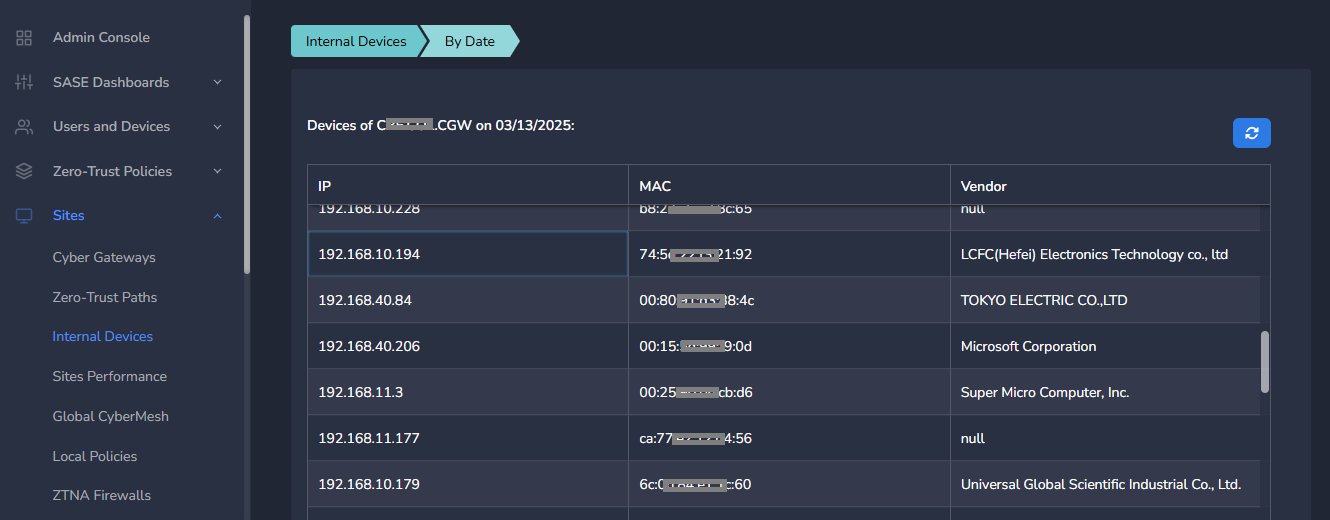
- To view granular details of the device, click on dates
¶ View Aggregated Device Count Across All Sites
Exium platform provides another device visibility option which aggregates device count from all the sites, clubs and shows it date wise.
- Click on Sites → Internal Devices in the left menu bar
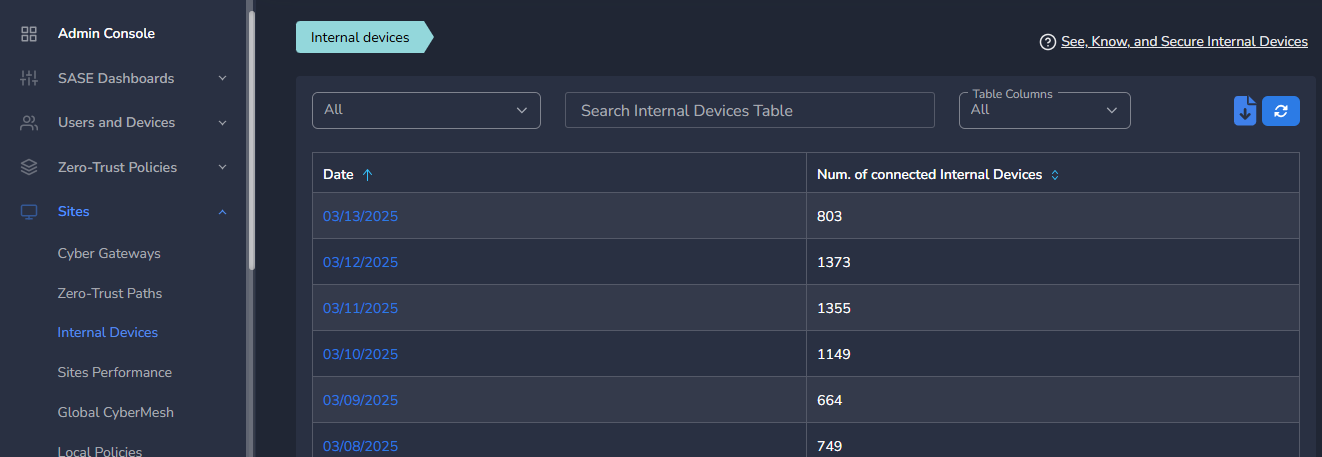
- To view device details, further click on dates.
To learn more about implementing IoT Security for your organization and explore tailored solutions that meet your unique requirements, contact Exium at hello@exium.net for a consultation or demonstration.