¶ Cyber Gateway Deployment on NanoPi R5S
The NanoPi R5S (as “R5S”) is an open-sourced gateway device with two 2.5G and one Gbps Ethernet ports, designed and developed by FriendlyElec, 4GB RAM LPDDR4X, 32GB eMMC 5.1 Flash. It has one microSD, one M.2 NVME, two USB 3.0, and USB Type-C power delivery. It uses Rockchip RK3568 chip, which is a high-range general-purpose SoC, made in 22nm process technology, integrated 4-core ARM architecture A55 processor.
¶ Hardware Checklist
Before deployment, make sure you have everything in the checklist below.
|
Number |
Item |
Quantity |
Remarks |
|
1 |
1 (2) |
2 for HA (high availability deployment) |
|
|
2 |
1 (2) |
2 for HA |
|
|
3 |
SanDisk 64GB Ultra microSDXC Memory Card |
1 (2) |
2 for HA |
|
4 |
1 |
To burn image on the SD card |
|
|
5 |
3 (6) |
Each NanoPi R5S box requires 3 LAN/ WAN cables |
¶ Common Deployment Architectures
There are 3 kinds of architectures, you can adopt as per your requirement.
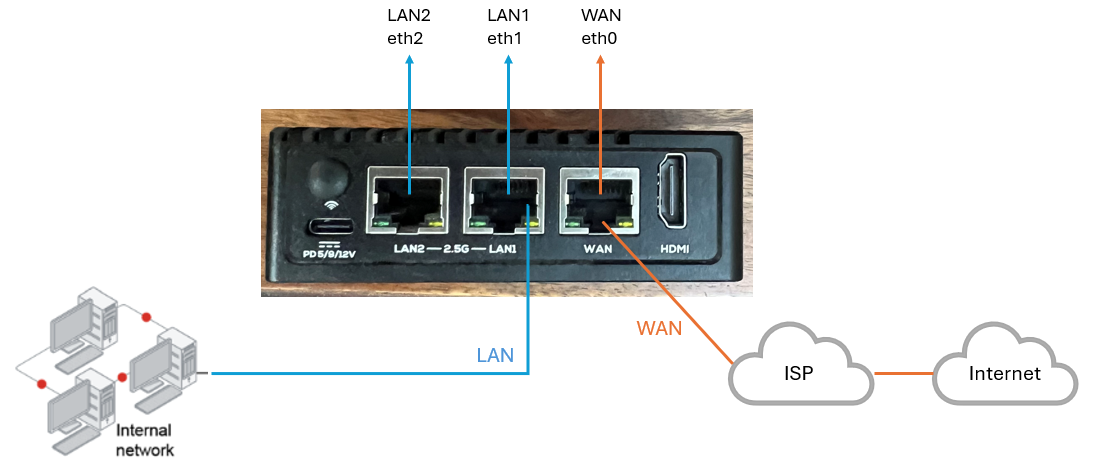
¶ Single WAN with Single LAN
A common deployment scenario for the NanoPi R5S deployment is to replace the Firewall. The architecture includes single WAN interface connecting to an ISP for Internet connection and single LAN towards your private network as described in below diagram.
Your WAN port/interface - Connect your physical WAN cable (coming from ISP modem) to the physical WAN port of the NanoPi box. This WAN port on NanoPi box is located next to HDMI port. After login to machine, you can see WAN interface with name eth0.
Your LAN port/interface - Connect your physical LAN cable (coming from your LAN switch which is connected to your private network) to the physical LAN1 port of the NanoPi box. This LAN1 port on NanoPi box is located next to WAN port. After login to machine, you can see LAN1 interface with name eth1.
After deployment physical port LAN2 (eth2 on OS level) which is not in use, will not have any IP address. It will be in down state.
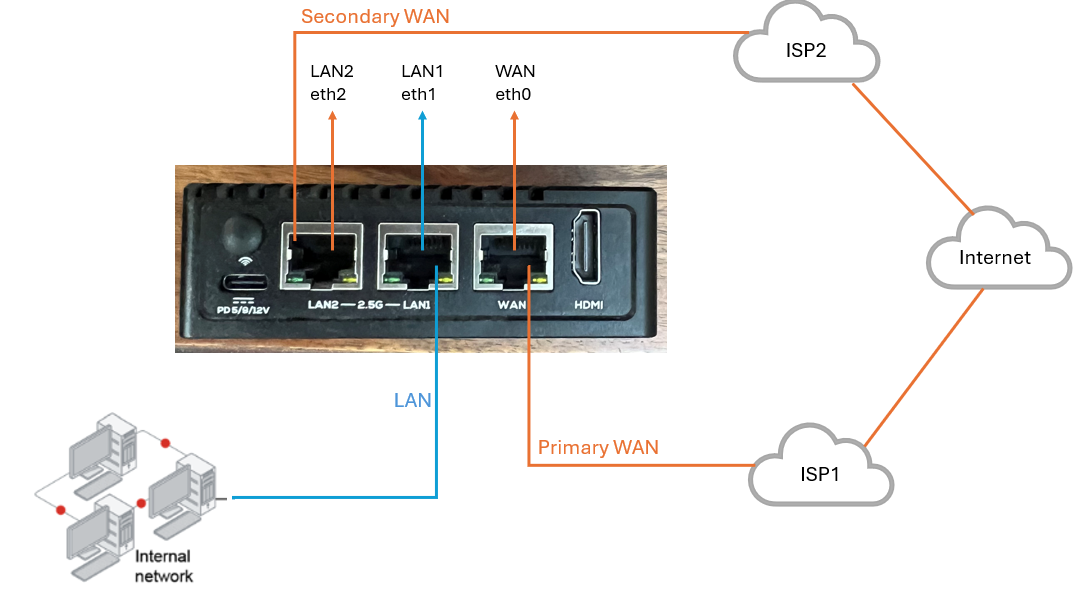
¶ Dual WAN with Single LAN
This deployment can address the WAN Aggregation and Failover. The architecture includes dual WAN interfaces connecting to two different ISPs for Internet connections to facilitate ISP failover. It includes single LAN towards your private network as described in below diagram.
Your Primary WAN port/interface - Connect your Primary WAN physical cable (coming from ISP1 modem) to the physical WAN port of the NanoPi box. This WAN port on NanoPi box is located next to HDMI port. After login to machine, you can see WAN interface with name eth0.
Your Secondary WAN port/interface - Connect your Secondary WAN physical cable (coming from ISP2 modem) to the physical LAN2 port of the NanoPi box. This LAN2 port on NanoPi box is located next to type-C power port. After login to machine, you can see secondary WAN interface with name eth2.
Your LAN port/interface - Connect your physical LAN cable (coming from your LAN switch which is connected to your private network) to the physical LAN1 port of the NanoPi box. This LAN1 port on NanoPi box is located next to WAN port. After login to machine, you can see LAN1 interface with name eth1.
After successful deployment, box will reboot. Default IP configuration on LAN1 (eth1) port of NanoPi box will be replaced with values which you will configure on admin console for LAN Interface Subnet.
Primary and secondary WAN interfaces will also use configuration provided on admin console.
For more details on how to configure Multi WAN on admin console for a CGW, please refer here.
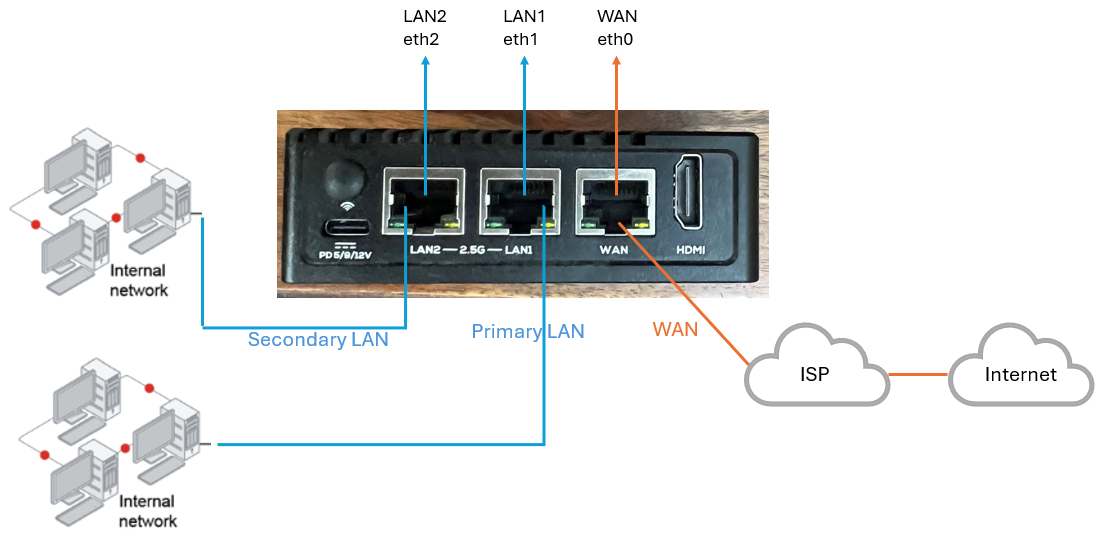
¶ Single WAN with Dual LAN
In this architecture single WAN will connect to one ISP for internet connection and you can connect your two separate private networks physically to the box on different LAN ports.
Your WAN port/interface - Connect your WAN physical cable (coming from ISP modem) to the physical WAN port of the NanoPi box. This WAN port on NanoPi box is located next to HDMI port. After login to machine, you can see WAN interface with name eth0.
Your Primary LAN port/interface - Connect your physical LAN cable (coming from your LAN switch which is connected to your private network1) to the physical LAN1 port of the NanoPi box. This LAN1 port on NanoPi box is located next to WAN port. After login to machine, you can see LAN1 interface with name eth1.
Your Secondary LAN port/interface - Connect your Secondary LAN physical cable (coming from your LAN switch which is connected to your private network2) to the physical LAN2 port of the NanoPi box. This LAN2 port on NanoPi box is located next to type-C power port. After login to machine, you can see LAN2 interface with name eth2.
After successful deployment, box will reboot. Default IP configuration on both LAN1 (eth1) and LAN2 (eth2) ports of NanoPi box will be replaced with values which you will configure on admin console for LAN Interface Subnets.
For more details on how to configure Multi LAN on admin console for a CGW, please refer here.
¶ Deploying Cyber Gateway on NanoPi R5S
To deploy Cyber Gateway on NanoPi R5S. follow the instructions below:
Keep the device powered off until Step 4 below.
¶ Step 1: Download the cyber gateway image file
- Download the image in gz file format from Exium downloads page here.
- Insert the SD card in the SD card reader and plug the reader in the USB port of a Windows (or Mac) machine.
¶ Step 2: Burn the image on to the SD card
- Download and launch balenaEtcher software on your windows (or Mac) machine: https://www.balena.io/etcher
- Unzip the OS image file that you downloaded in your file folder, and then select the unzipped OS image (Disk image file format) in the balenaEtcher and flash onto the SD card. You may also directly import the gz file without unzipping.
¶ Step 3: Insert the SD card into the NanoPi R5S
- When flash is completed, remove the SD card from the SD card reader.
- Power off your NanoPi R5S (if it is already not powered off), insert the SD into the NanoPi-R5S’s microSD card slot.
¶ Step 4: Power on the NanoPi R5S
- Turn on NanoPi-R5S, it will boot from the SD card and automatically run EFlasher to install the OS to the board’s eMMC.
- After flashing is complete, you will see the message below if you have connected a monitor via NanoPi-R5S’s HDMI slot.
- Eject the SD card from NanoPi-R5S, NanoPi-R5S will automatically reboot and boot from eMMC.
¶ Step 5: Login to the NanoPi R5S box
- Connect a monitor, keyboard, and mouse to the NanoPi R5S via its HDMI and USB ports to access the console. Alternatively, if direct console access isn't possible, use network scanning software like nmap to find the NanoPi R5S's local IP address and then connect via SSH.
- Login with username:
piand password:pi. We recommend that you change the default password immediately before deploying the cyber gateway.
To change password, at the command prompt, type “sudo passwd pi” and press Enter. Enter the root user password (which is also pi). Enter the new user password. Retype the new password a second time.
¶ Step 6: Deploy the Cyber gateway on the NanoPi R5S
- Follow the instructions for Multiple interface Cyber Gateway deployment
In case of Multiple Interface Cyber Gateway, after successful deployment, box will reboot. Default IP configuration on LAN ports of NanoPi box will be replaced with values which you will configure on admin console for LAN Interface(s).
For SSH login, you can use LAN Gateway IP of the LAN Interface Subnet which you configured on admin console.
¶ What Performance to expect on NanoPi R5S?
In the Multiple Interface cyber gateway, security controls such as Firewall and Web security is provided locally in the CGW. Therefore, we recommend that only the Secure Private Access (SPA) traffic goes to the Mesh while the Secure Internet Access (SIA) traffic that has already gone through advanced security controls in the CGW itself can exit locally.
¶ WAN Throughput
See below result of a Speedtest for the SIA traffic exiting locally, where the ISP speed is 1.0Gb/s. We can see that the Cyber gateway can support network speeds matching to the ISP speed of about 1.0 Gb/s.
¶ LAN Throughput
The two LAN ports on NanoPi R5S are rated for 2.5 Gb/s while the port labeled WAN is rated at 1.0 Gb/s. For the lateral East-West traffic that stays local to the site and does not exit towards WAN, NanoPi R5S can support higher network speeds. The results of an iperf Throughput test on the LAN network are provided below. We can see that the Cyber gateway can support LAN network speeds of about 2.0 Gb/s.
Accepted connection from 192.168.9.5, port 53024
[ 5] local 192.168.9.251 port 5201 connected to 192.168.9.5 port 53028
[ ID] Interval Transfer Bitrate Retr Cwnd
[ 5] 0.00-1.01 sec 212 MBytes 1.76 Gbits/sec 17 512 KBytes
[ 5] 1.01-2.01 sec 255 MBytes 2.14 Gbits/sec 0 571 KBytes
[ 5] 2.01-3.01 sec 264 MBytes 2.22 Gbits/sec 0 609 KBytes
[ 5] 3.01-4.00 sec 249 MBytes 2.09 Gbits/sec 0 618 KBytes
[ 5] 4.00-5.01 sec 256 MBytes 2.14 Gbits/sec 0 621 KBytes
[ 5] 5.01-6.01 sec 256 MBytes 2.15 Gbits/sec 0 624 KBytes
[ 5] 6.01-7.01 sec 235 MBytes 1.97 Gbits/sec 0 628 KBytes
[ 5] 7.01-8.01 sec 236 MBytes 1.98 Gbits/sec 0 636 KBytes
[ 5] 8.01-9.01 sec 232 MBytes 1.95 Gbits/sec 0 641 KBytes
[ 5] 9.01-10.01 sec 236 MBytes 1.98 Gbits/sec 0 641 KBytes
[ 5] 10.01-10.04 sec 6.25 MBytes 1.92 Gbits/sec 0 641 KBytes
- - - - - - - - - - - - - - - - - - - - - - - - -
[ ID] Interval Transfer Bitrate Retr
[ 5] 0.00-10.04 sec 2.38 GBytes 2.04 Gbits/sec 17 sender
-----------------------------------------------------------
Server listening on 5201To learn more about implementing SASE for your organization and explore tailored solutions that meet your unique requirements, contact Exium at partners@exium.net for a consultation or demonstration. If you are ready to get started, check out our testing and onboarding process.