¶ Secure Zero-Trust Access: Beyond VPNs
Legacy VPNs, built for the perimeter-based security of the 1980s, are struggling to keep pace with today's decentralized, cloud-first work environments. Their performance limitations, management complexities, vulnerability to attack, and over-permissive access controls create significant security risks. Zero Trust Network Access (ZTNA) offers a superior solution, providing secure access to both private and public-facing applications without the inherent weaknesses of VPNs.
¶ Core principles of Zero-Trust Access
Designed for today’s decentralized networks and workforces, ZTNA is based on three core principles:
|
Assume breach |
Verify explicitly |
Least privilege |
| Any network, device, credential, or user could be compromised at any time. Never assume trust for any of them. | Authenticate user identity, confirm device posture, and evaluate the context of every request. | Only authorize access to specific resources the user needs for their work. |
¶ Benefits of ZTNA
ZTNA is network-agnostic, creating direct connections between users wherever they are located and a company’s resources whether on-premises or in the cloud. Some of the benefits of ZTNA include:
| Unified access control | ZTNA lets companies manage access for remote and on-premises workforces within a single system. |
| Securing development environments | ZTNA improves the security of a company’s most sensitive resources while improving developers’ access. |
| Universal multi-factor authentication | Exium’s ZTNA solution lets you extend MFA to every resource — even to services such as SSH |
| Improved security | ZTNA lets you apply granular, role-based access controls based on the principle of least privilege. |
¶ Agent-based vs. Agentless ZTNA Approaches
As indicated by the name, the Agent-based approach requires software to be installed on the user's device. This software gathers information about identity, security posture, and context before sending it to the ZTNA system. Once authenticated, ZTNA solutions like Exium establish encrypted tunnels between the user’s device and authorized resources.
The choice between approaches depends on factors specific to your organization. Here are three scenarios that outline some trade-offs:
|
Ease of Installation on Managed vs. Personal Devices |
Compatibility with Application Types |
Simplifying Security Architecture Migration |
|---|---|---|
| Installing an agent on a managed device is straightforward. However, logistical and privacy issues may complicate agent installation on employees’ personal devices or third-party devices. In such cases, an agentless approach may be more suitable. | Agentless ZTNA is only compatible with applications accessible via a browser. For accessing legacy applications without web interfaces, users must install a ZTNA agent. | Agent-based ZTNA can simplify transitioning to a new security architecture. The ZTNA agent is similar to VPN clients users may already be familiar with, eliminating the need for them to learn a new browser-based system. This approach allows users to access resources in the same way they always have. |
Exium offers support for both agent-based and agentless ZTNA. This document will guide you through the straightforward steps to begin your agentless ZTNA journey.
¶ Agentless ZTNA: Simple, Secure Access
Accessing company resources with agentless ZTNA is easy: simply open your browser and connect to the ZTNA portal. The portal assesses your device's security and network context, verifies your identity (via password, SSO, or MFA), and then grants access to authorized web-based resources.
Exium's agentless ZTNA secures remote access to all your applications—public and private, cloud-based or on-premises—with end-to-end encryption and granular zero-trust controls. This ensures optimal security for employees, partners, and suppliers, regardless of location.
¶ Unlocking Agentless Access
- Go to the MSP admin console, then navigate to Companies and click on the company name (or directly access the Customer/Client Workspace Sign In).
- Add users who require agentless access to the workspace. If users are already added, you can skip this step.
- Activate Agentless ZTNA access (see instructions in the next section)
- Create Agentless Applications, , follow the steps outlined in this guide.
- If you want users to authenticate access to Agentless Applications via Azure AD Authentication, follow the integration steps outlined in this guide.
- To use the built-in MFA for authentication, ensure users configure MFA before accessing the Agentless Applications.
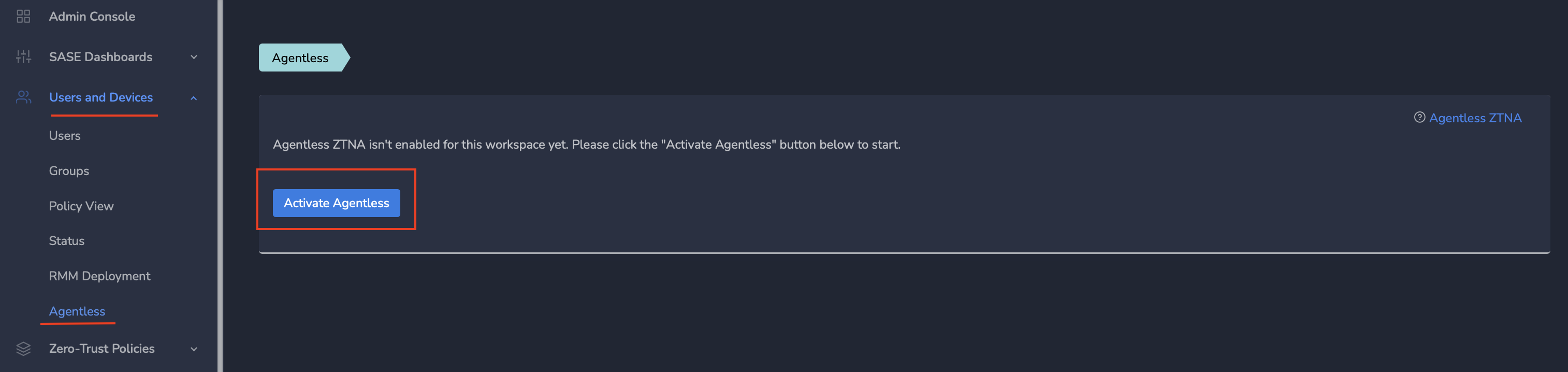
¶ Activate Agentless access
To enable agentless access in the selected workspace, follow these steps:
- Go to the MSP admin console, then navigate to Companies and click on the company name (or directly access the Customer/Client Workspace Sign In).
- Click on “Users and Devices” and then select “Agentless.”
- Click on “Activate Agentless” to enable the agentless service.
Activating the Agentless ZTNA service for the selected workspace may take a few minutes. Once the service is activated, you will receive an email confirming the activation, and all users will receive an email with the necessary links to access the service.
For expert guidance on implementing SASE, XDR, IAM, and GRC solutions, reach out to Exium at partners@exium.net. If you are ready to get started, check out our testing and onboarding process.