¶ Overview
In the evolving landscape of network security, DNS plays a pivotal role in ensuring seamless access and security for users and applications. Exium’s SASE solution leverages robust DNS Security alongside the capability to integrate private DNS servers, offering a fortified approach to Zero Trust Network Access (ZTNA).
¶ DNS Security and Private DNS Servers
¶
|
Enhanced Security with DNS Traffic Inspection |
Seamless Integration with Private DNS Servers |
|---|---|
| Exium's SASE solution utilizes DNS traffic relaying through our cloud-based Cybermesh, enabling rigorous inspection of DNS queries to detect and block potential threats and malicious activities. This proactive approach ensures that all DNS traffic is secure, providing an added layer of defense within the network. | Organizations can configure their own private DNS servers within the Exium admin console. This integration empowers remote users to access private applications using intuitive private or local domains, eliminating the need for cumbersome IP addresses. By proxying DNS traffic via our DNS server, Exium delivers the best of both worlds: the flexibility of private DNS servers for internal domains and heightened security through comprehensive DNS traffic inspection. |
¶ DNS Suffix: Simplifying Access to Internal Services
The DNS suffix is an essential component that facilitates the resolution of unqualified hostnames into fully qualified domain names (FQDN). By setting a DNS suffix such as "exium.local," users connected to the CyberMesh can effortlessly access services by simply typing the service name—such as "http://service," "ping service," or "ssh service." This feature streamlines user access to internal resources, enhancing productivity and user experience.
The DNS Suffix can be configured at both the workspace level and the user group level. When set at the workspace level, the DNS Suffix applies to all users within that workspace. However, this can be overridden for specific users in a group by assigning a different DNS Suffix at the user group level.
For example, if the DNS Suffix at the workspace level is set to exium.local and the DNS Suffix at the apptest group level is set to speerity.local:
- User A, who is part of the
apptestgroup, will receive the DNS Suffixspeerity.local. - User B, who is not part of the
apptestgroup, will continue to use the DNS Suffixexium.local.
¶ Setup DNS Suffix - Workspace level
Step 1: Log into the partner admin console and navigate to the company workspace.
Step 2: In the Admin Console, click on Configurations.
Step 3: On the Private DNS page, select the appropriate workspace from the dropdown menu.
Step 4: Enter the desired DNS Suffix and click Update as shown below.
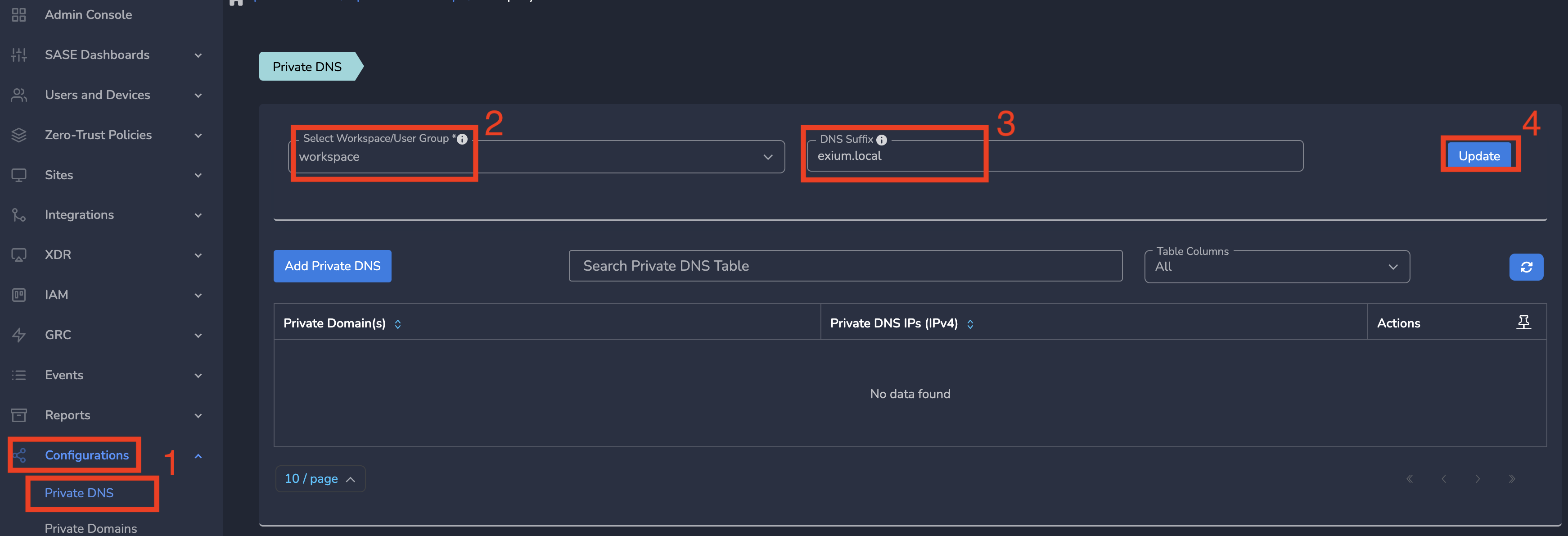
All users in workspace will be configured with DNS Suffix entered here.
¶ Setup DNS Suffix - Group level
To change the DNS Suffix at group level, here are the steps:
Step 1: Log into the partner admin console and navigate to the company workspace
Step 2: On Admin Console, Click on the Configurations
Step 3: On Private DNS page, Select group from the dropdown menu.
Step 4: Enter DNS Suffix, Click Update as shown below.
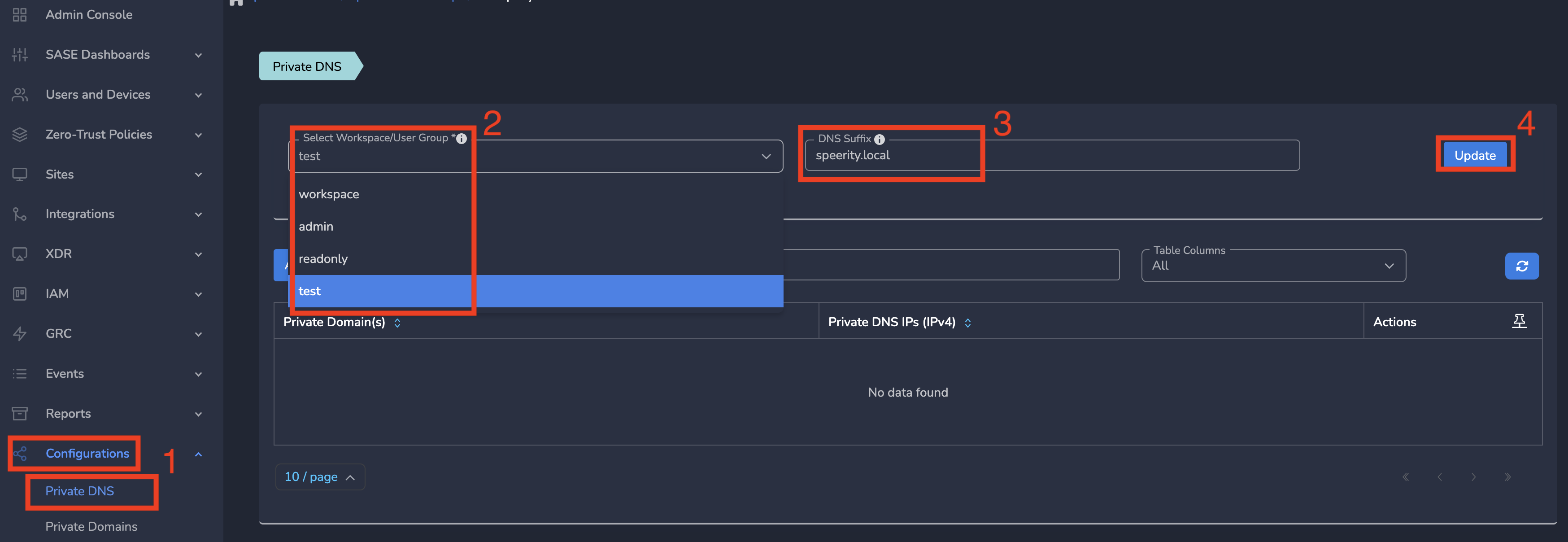
All users in this group will be configured with DNS Suffix entered here
¶ Private DNS - Extending DNS Security to your DNS
You can extend DNS security offered by Exium Cybermesh to your existing DNS servers to resolve your private domains.
¶ DNS Traffic Flow
The DNS traffic flow is shown in the figure below. Your devices always see Exium DNS servers, 172.18.8.100 and 172.19.53.1 in the example below. These DNS servers forward any DNS queries for your internal domains to your DNS servers, 10.10.37.43 and 192.168.21.78 , for example, running on-prem. The devices securely get back response to their DNS queries for both public and private domains.
Often only few private domains needs resolution from private DNS servers. Cybermesh allows you to set private DNS against only required private domains. Optionally Cybermesh allows all domains to be resolved by private DNS server but this is not recommended because of performance and latency impact on user experience. Following table summarises both options.
|
Domains |
Example Domins |
Example DNS |
|
|---|---|---|---|
| Selective Private Domains |
Selective |
exium.local, exium.net |
10.20.30.1,10.20.30.2 |
| All Private Domains |
All |
all |
10.20.30.3,10.20.30.4 |
Note: These private DNS server IPs should be part of one of the Trustpaths behind a CGW so that these are reachable from cybermesh
¶ Setup Private DNS for Selective Domains
To change the DNS providers to your private DNS servers, you can edit the settings at the workspace level. Here are the steps:
Step 1: Log into the partner admin console and navigate to the company workspace
Step 2: On Admin Console, Click on the Configurations
Step 3: On Private DNS page, Click on Add Private DNS as shown below.
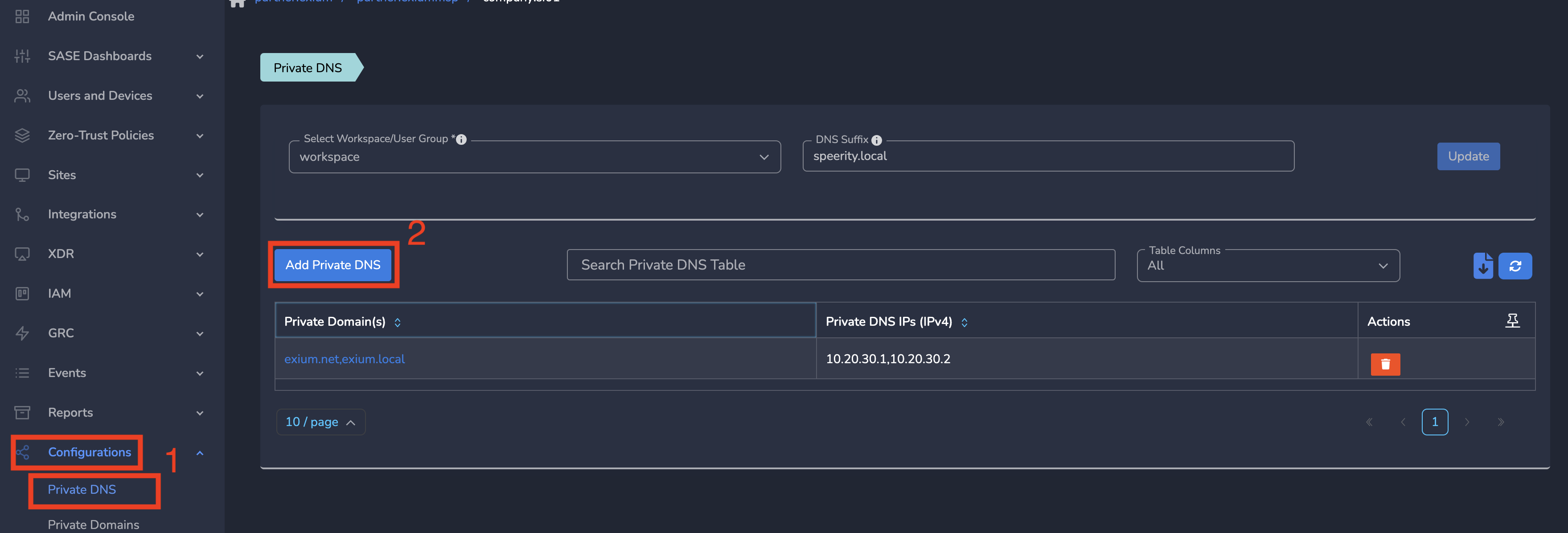
Step 4: Enter Private Domain(s) and Enter Private DNS IPs (IPv4), Click Save as shown below.
Note that you can add multiple domains in Private Domain(s) field and multiple DNS IP addresses in Private DNS IPs (IPv4) field, one after the other, press space or enter on the keyboard before entering the next one.
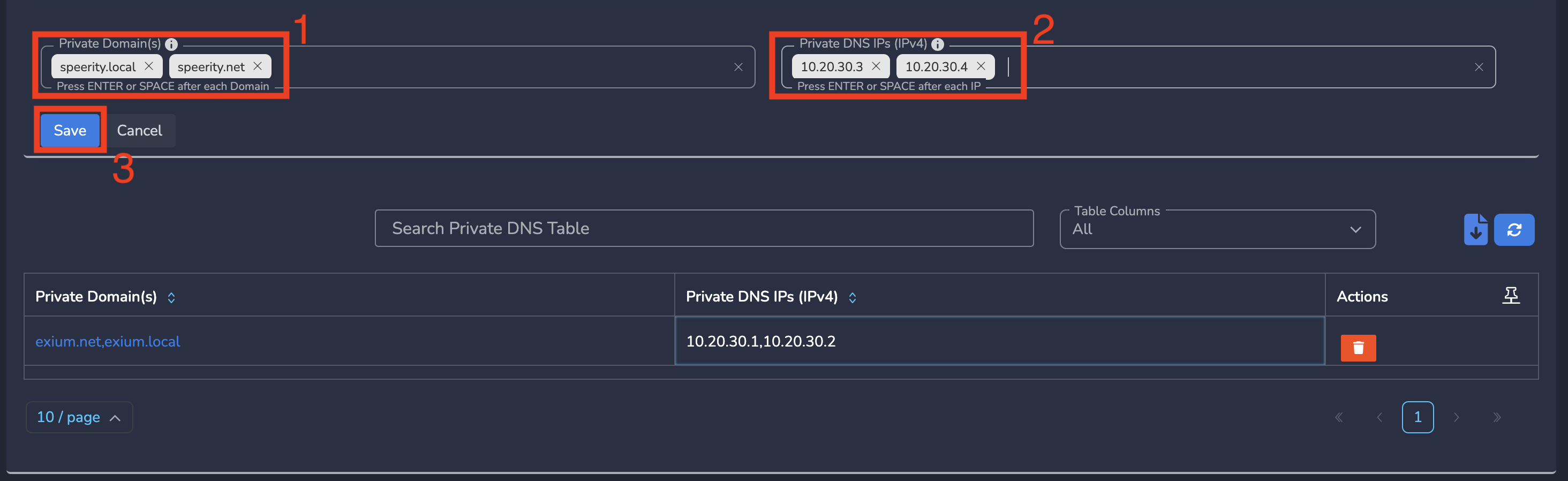
Your DNS traffic is now fully secured while resolving both public and private domains.
¶ Setup Private DNS for All Domains
To change the DNS providers to your private DNS servers, you can edit the settings at the workspace level. Here are the steps:
Step 1: Log into the partner admin console and navigate to the company workspace
Step 2: On Admin Console, Click on the Configurations
Step 3: On Private DNS page, Click on Add Private DNS.
Step 4: Enter Private Domain(s) as all and Eneter Private DNS IPs (IPv4), Click Save as shown below.
Note that you can add multiple DNS IP addresses in Private DNS IPs (IPv4) field, one after the other, press space or enter on the keyboard before entering the next one.
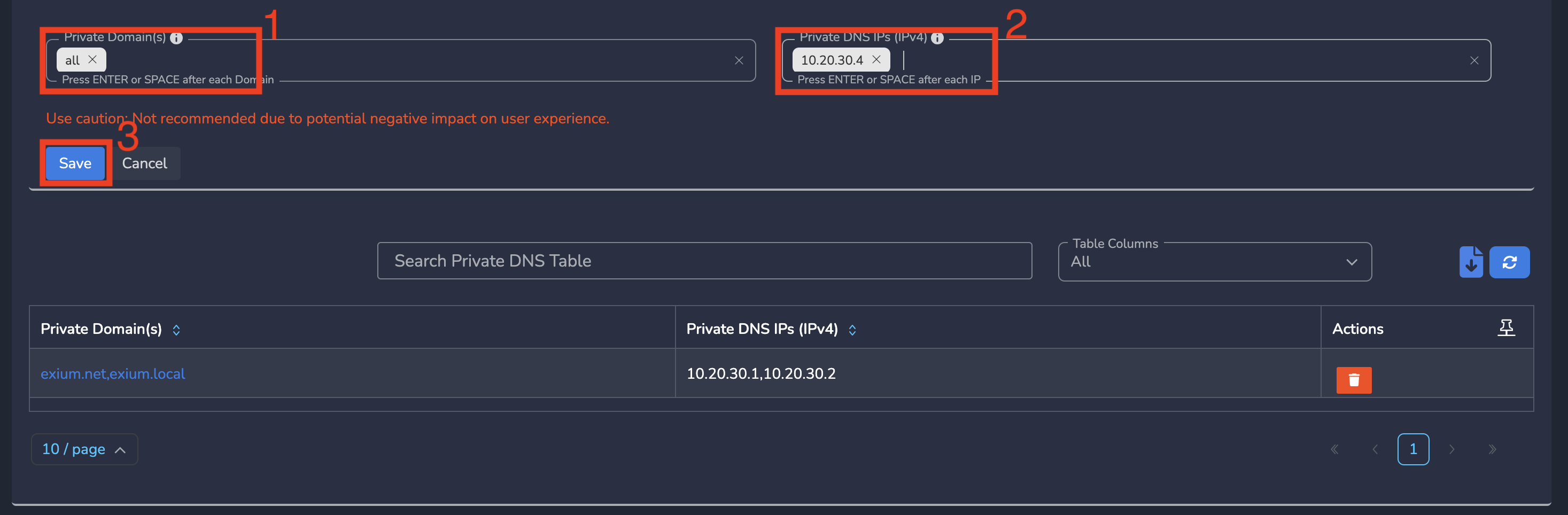
Your DNS traffic is now fully secured while resolving both public and private domains.
¶ Private Domains - Configure private domains
In case if you don't have private DNS server but have some private domains which needs to be resolved by Exium cybermesh, you can configure these domains by following below steps
Step 1: Log into the partner admin console and navigate to the company workspace
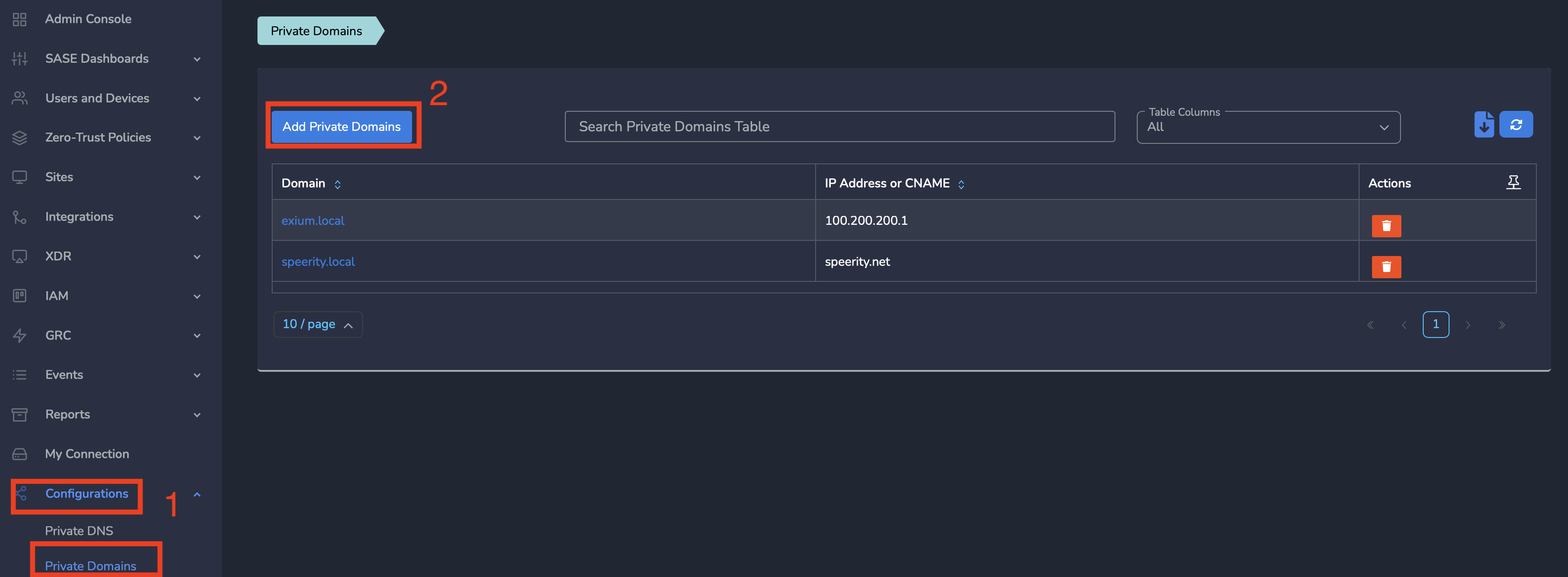
Step 2: On Admin Console, Click on the Configurations and on Private Domains
Step 3: On Private Domains page, Click on Add Private Domains as shown below.
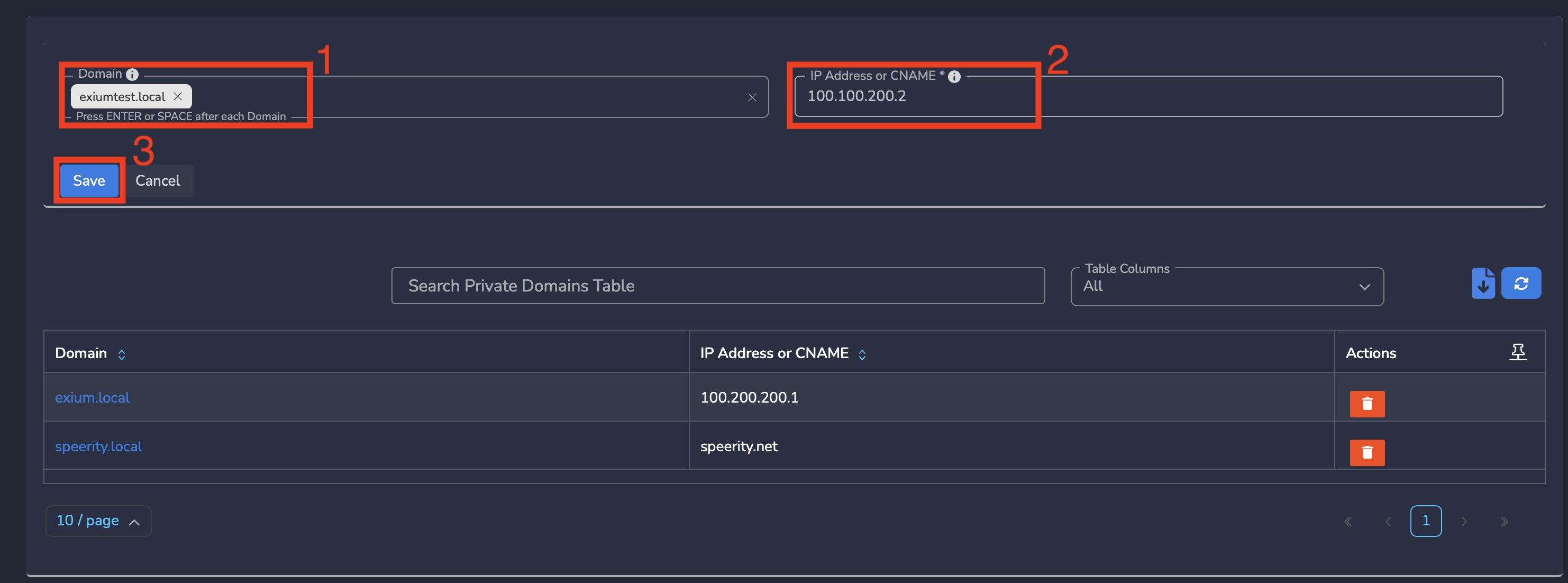
Step 4: Enter Domain and Enter IP address or CNAME, Click Save as shown below. You can also enter CNAME so that the domain gets resolved to IP of CNAME.
Your DNS traffic is now fully secured while resolving both public and private domains.
¶ Configure Zero-Trust Policies for Private-Domains
When you configure private DNS servers, you can configure and apply Zero-Trust security policies to your private domains the same way you apply security policies to public domains for Web and SaaS Security.
For example you may have two local apps:
- app.mycompany.local
- db.mycompany.local
You may like to give access to all employees to the application domain app.mycompany.local and give access to only developer group for the database private domain db.mycompany.local
You can define private domain policies at workspace, group and at user level. To create private domain policies policies, Follow below steps
- Navigate to the Service Portal admin console or navigate to the MSP admin console -> Client Workspace
- Click on Zero-Trust Policies in the left menu bar and Click on Rules
- Select the Workspace, group name or user
- Give a name to the policy, Select Block or Allow
- Enter the private domain name in the Domain entry
- Click Save
The screenshot below the case where we are blocking access to the private domain app.exium.local for the group “US Team”.
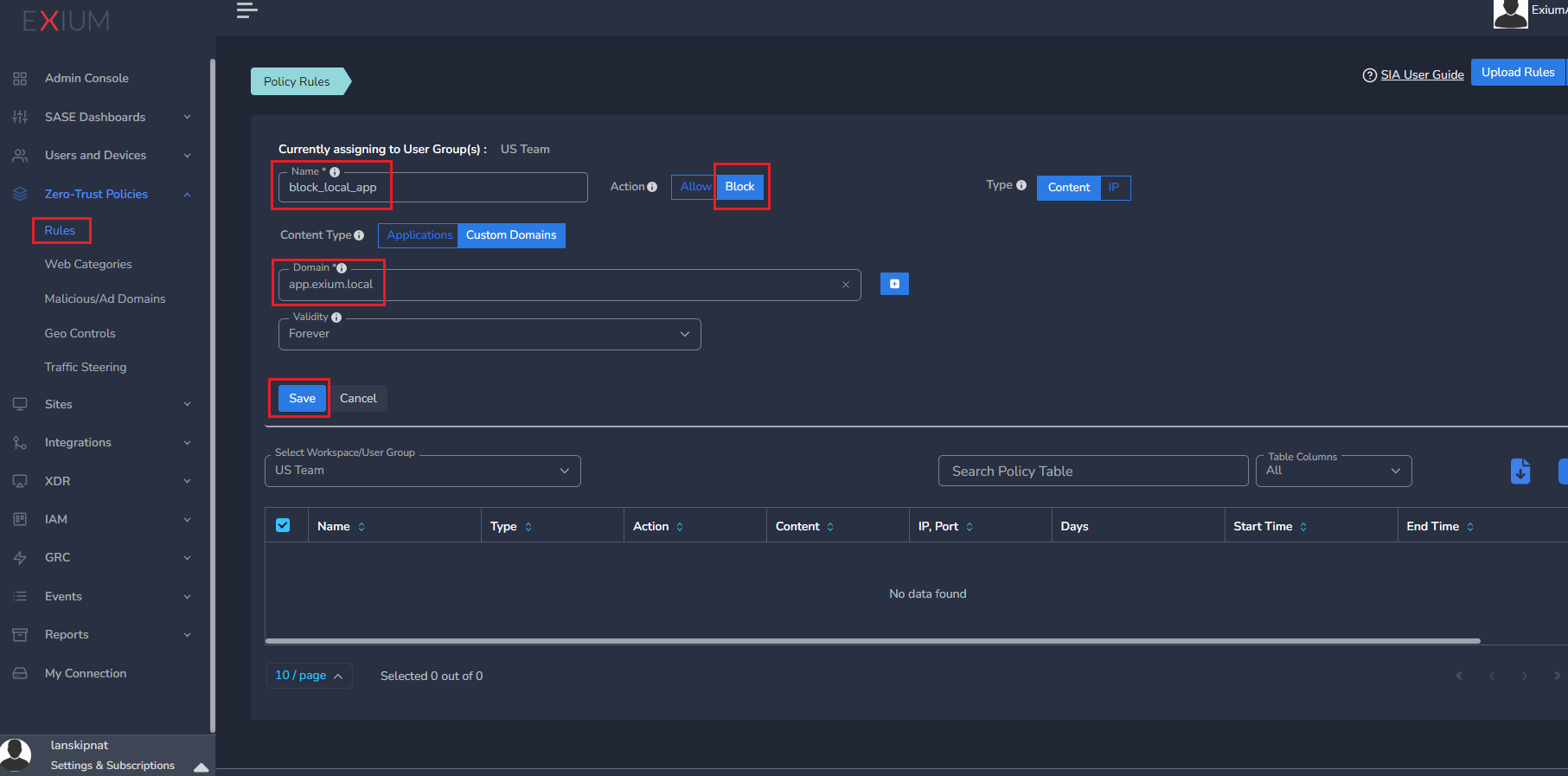
After adding this policy, all the users in group “US Team” will not have access to app.exium.local.
¶ Conclusion
Exium’s SASE solution stands at the forefront of network security by integrating DNS Security and the capability to configure private DNS servers. This dual approach not only safeguards DNS traffic from threats but also empowers organizations to maintain seamless internal domain resolution through customizable DNS Suffix settings. By adopting Exium’s innovative solution, organizations can enforce Zero Trust principles while ensuring efficient and user-friendly access to critical applications and resources.
To learn more about implementing SASE, XDR, IAM, and GRC for your organization and explore tailored solutions that meet your unique requirements, contact Exium at partners@exium.net for a consultation or demonstration. If you are ready to get started, check out our testing and onboarding process.