¶ Introduction
Web security is a critical concern for organizations of all sizes, as the internet remains a primary vector for cyber threats. This solution brief explores the integration of URL filtering and DNS security as a comprehensive approach to safeguarding networks and data from web-based threats.
¶ Challenges
Web-Based Threats: The internet is riddled with malware, phishing sites, and other cyber threats, making it easy for malicious actors to target your organization.
Data Leakage: Sensitive information can be unintentionally exposed through unauthorized web access, putting your organization at risk of data breaches.
Compliance: Regulatory requirements necessitate stringent control over web access, especially in industries such as healthcare (HIPAA), finance (PCI DSS), and more.
Balancing Productivity and Security: Enforcing web security without hampering productivity can be a challenging task.
¶ Solution: Cloud-Delivered Web and SaaS Security
Domain and URL filtering is a cornerstone of web and SaaS security. By implementing comprehensive Web filtering policies and controls, organizations can mitigate risks, protect sensitive data, ensure regulatory compliance, and promote a security-conscious culture. In an evolving threat landscape, robust Web filtering is essential for safeguarding digital assets and maintaining a resilient security posture.
URL Categorization and Filtering: Exium categorize websites based on content, and define policies to allow or block access to specific categories.
Real-time Threat Intelligence: Integrates real-time threat intelligence feeds to stay updated on known malicious domains, URLs, and emerging threats.
Granular Policies: Define and enforce granular access policies that control web access for different user groups, departments, or roles.
SaaS Security: Extend URL filtering to cloud-based SaaS applications to ensure that users comply with web security policies while using these services.
Logging and Reporting: Maintain detailed logs and reports to monitor web activity, access patterns, and security incidents, which can aid in threat detection and compliance.
¶ Benefits of Exium's Web and SaaS Security Approach
Enhanced Security: URL filtering prevents access to malicious websites and reduces the risk of malware infections, phishing attacks, and other web-based threats.
Compliance: Adhere to regulatory requirements, reducing the risk of non-compliance-related fines and penalties.
Increased Productivity: Strike a balance between security and user productivity, ensuring efficient web usage without sacrificing protection.
Reduced Risk: Prevent unauthorized web access and data breaches, minimizing the potential impact of security incidents.
¶ Configure & Apply Web Security Policies
Exium enables workspace admins with multiple options to configure web security policies.
| Web Policies |
Workspace level |
Group level |
User level |
|---|---|---|---|
| Web domains/ URLs policies |
√ |
√ |
√ |
| Web Categories policies |
√ |
- |
- |
| IP (Firewall) policies |
√ |
√ |
√ |
- Admins can define web category policies at workspace level which will be applied to all users in the workspace
- Admins can define web domain policies and at workspace level which will be applied to all users in the workspace.
- Admins can define web domain policies at group level which will be applied to all users in that group.
- Admins can define web domain policies and at a user level which will be applied to that particular user.
- Admins can define IP policies and at workspace level which will be applied to all users in the workspace.
- Admins can define IP policies at group level which will be applied to all users in that group.
- Admins can define IP policies and at a user level which will be applied to that particular user.
¶ Web Policies Precedence
Admins can attach override policies at higher precedence. User level policies are at highest precedence, followed by the group level policies and finally workspace level policies are at lowest precedence.
¶ Web Category Policies
Web Category Policies enable admins to configure ALLOW/BLOCK web categories.
¶ Workspace level Web Category Policies
You can define web category policies at workspace level which will be applied to all users in workspace. To create web category policies, Follow below steps
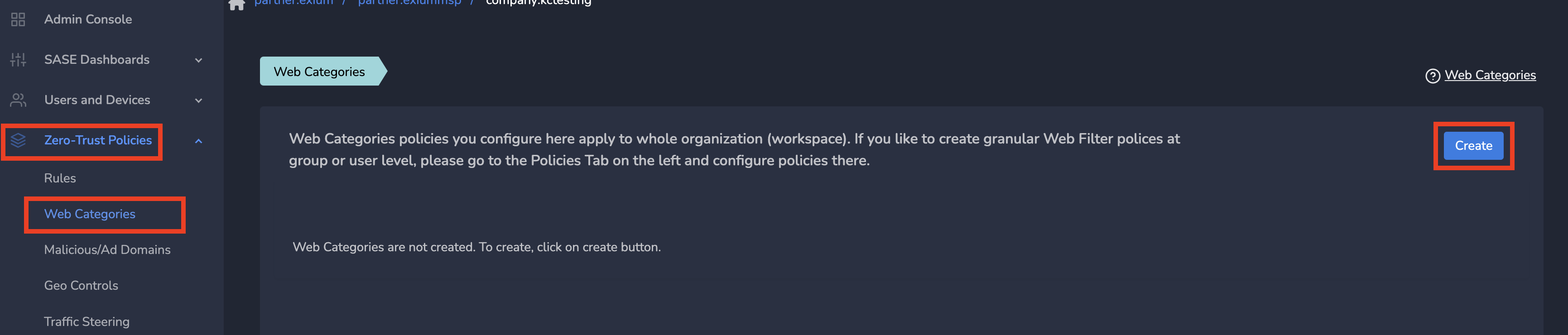
- Log into the partner admin console and navigate to the company workspace.
- Click on Zero-Trust Policies in the left menu bar and Click on Web Categories
- Click on the Create as shown below
By default, some categories like Illegal Content, Hate Content etc. are blocked. If you want to change (BLOCK to ALLOW and vice versa) some of the web categories as per end customer requirements, please follow below steps.
- Change Web Categories as per end customer requirements and Submit as shown below
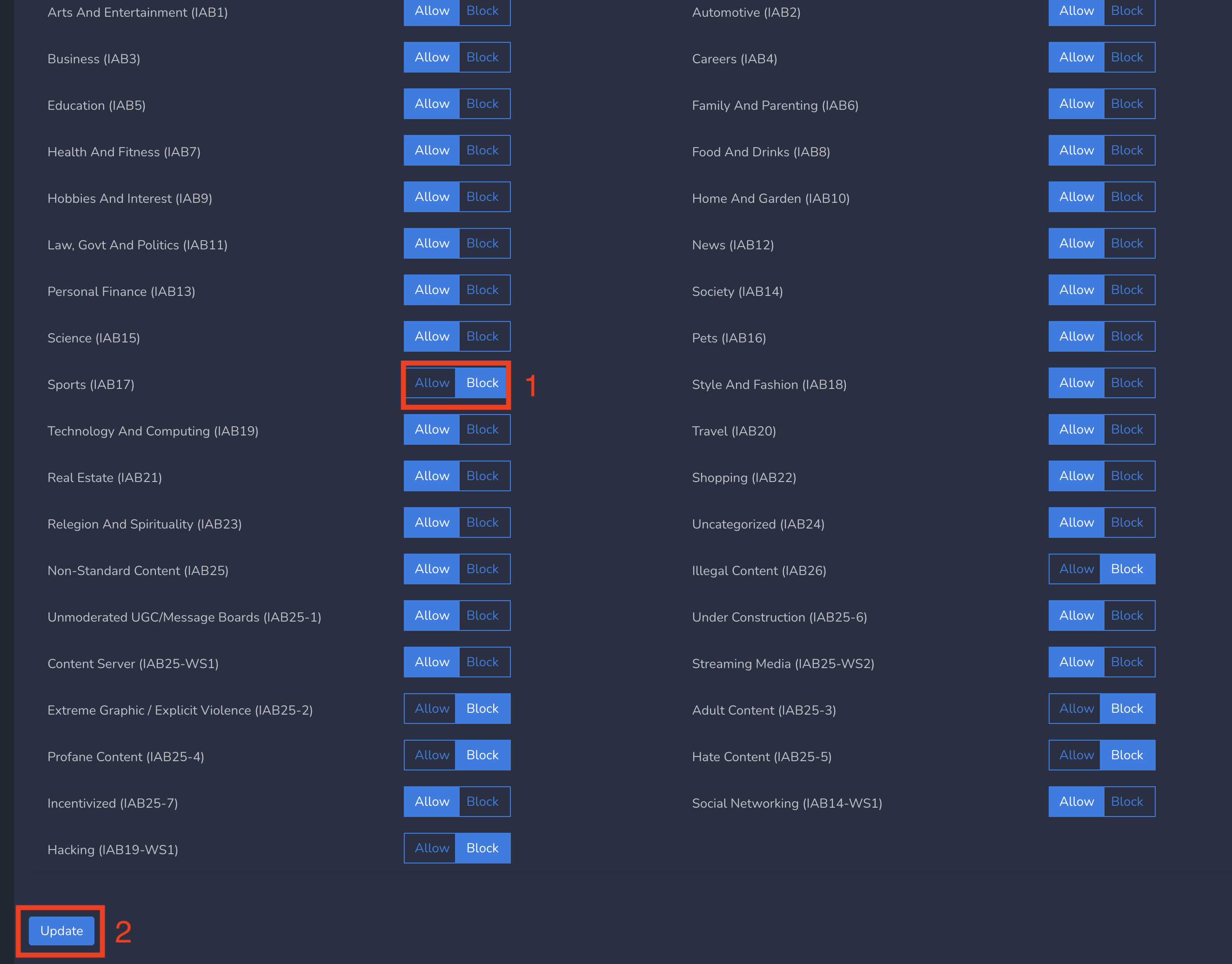
Web Category policies gets applied to all users immediately after submitting.
¶ Check/Test Domain for a Web Category
You can test a domain to know which web category, it belongs to. To check/test domains, Follow below steps
- Log into the partner admin console and navigate to the company workspace.
- Click on Zero-Trust Policies in the left menu bar and Click on Web Categories
- Enter Domain in Domain field and Click on Check Category as shown below
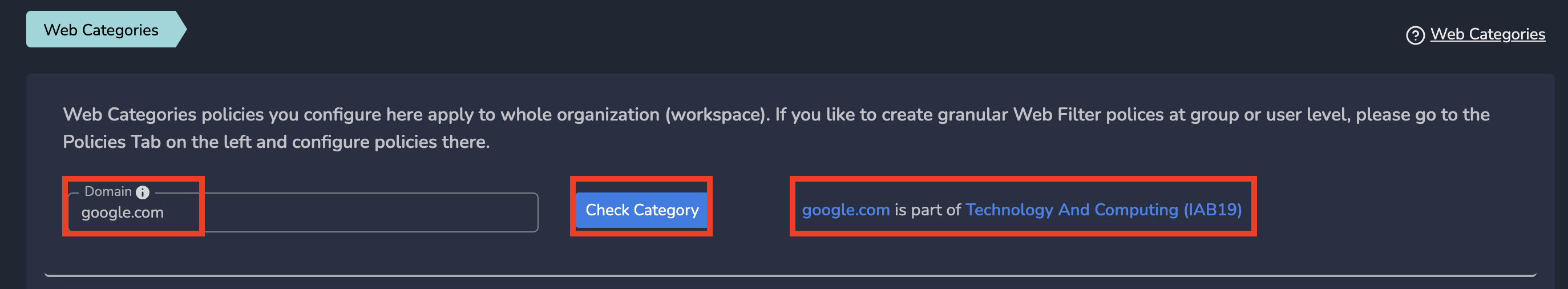
It will show the category to which this domain belongs to
¶ Local site level (CyberGateway) Web Category Policies
You can define web category policies at each site level (where CyberGateway is deployed) which will be applied to all users in the site. To create web category policies, Follow below steps
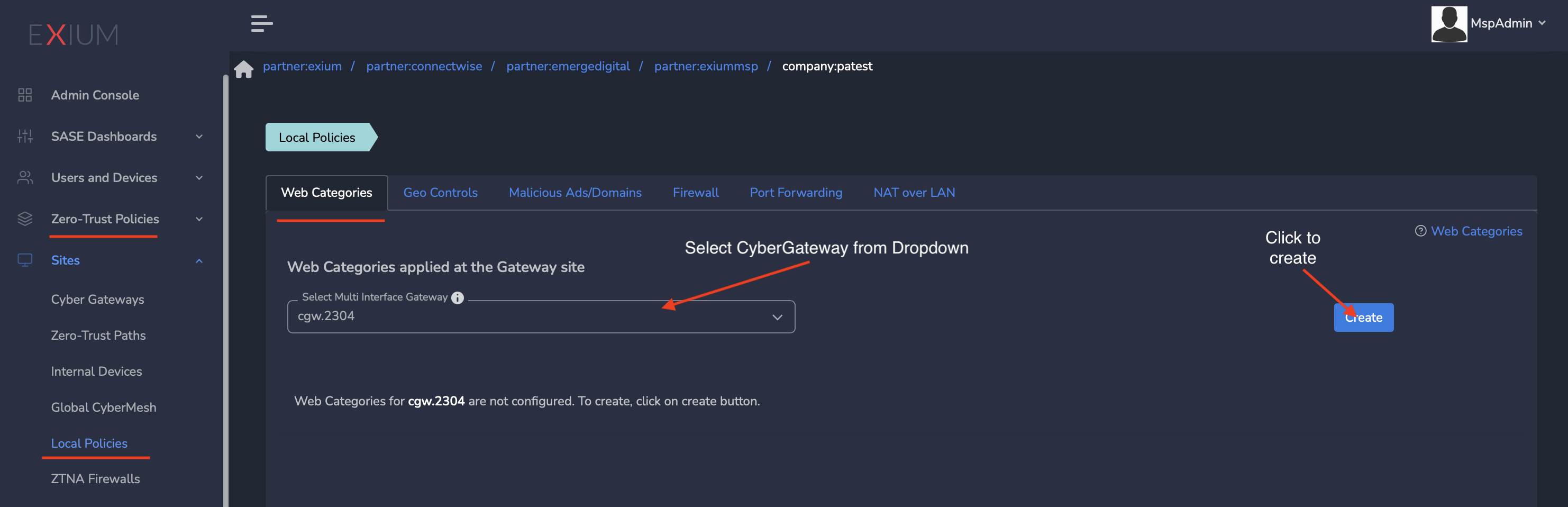
- Log into the partner admin console and navigate to the company workspace.
- Click on Sites in the left menu bar and Click on Local Policies
- Select CyberGateway from Drop down
- Click on the Create as shown below
By default, some categories like Illegal Content, Hate Content etc. are blocked. If you want to change (BLOCK to ALLOW and vice versa) some of the web categories as per end customer requirements, please follow below steps.
- Change Web Categories as per end customer requirements and Submit as shown below

Web Category policies gets applied to all users in site immediately after submitting.
¶ Web Domain Policies
Web Domain Policies enable admins to configure ALLOW/BLOCK specific web domains.
¶ Workspace level Web Domain Policies
You can define web domain policies at workspace level which will be applied to all users in workspace. To create web domain policies, Follow below steps
- Log into the partner admin console and navigate to the company workspace.
- Click on Zero-Trust Policies in the left menu bar and Click on Rules
- Select workspace from drop down and click on Add Rule as shown below
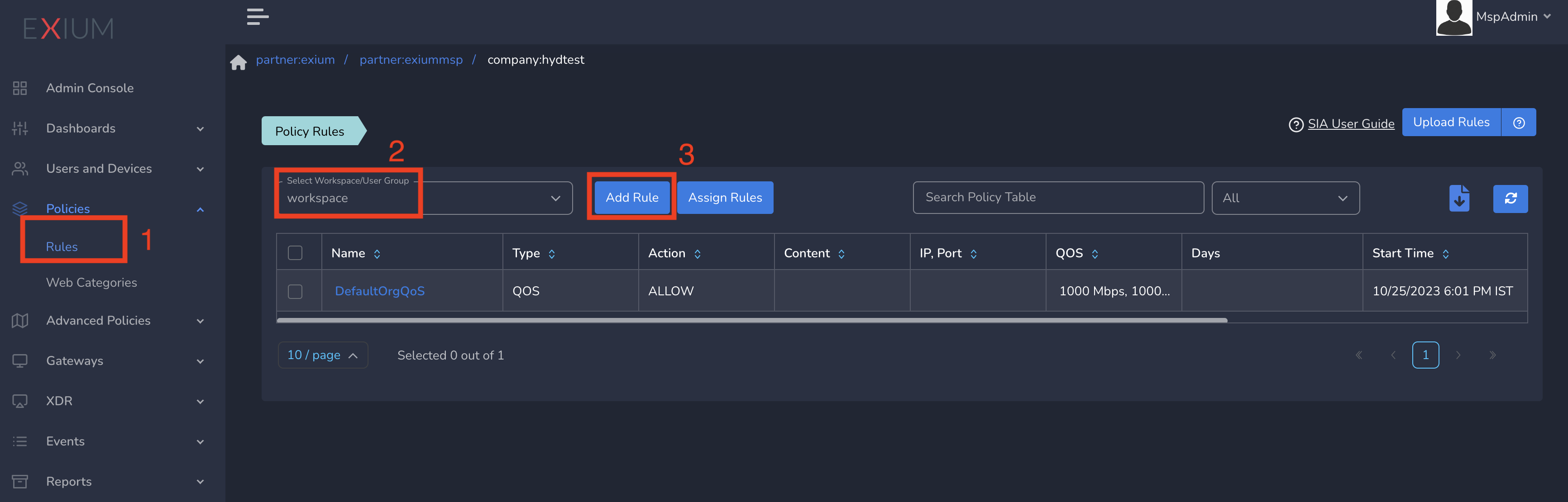
On Create Policy form, follow below steps
- Enter a name for policy
- Select Action as Allow/Block (based on requirement). By default, Block is selected.
- Enter the domain. Some domains are pre populated. If the domain you are entering shows up in drop down, you can select
- Optionally multiple domains can be added by clicking on + icon next to first domain
- Finally click on Save as shown below
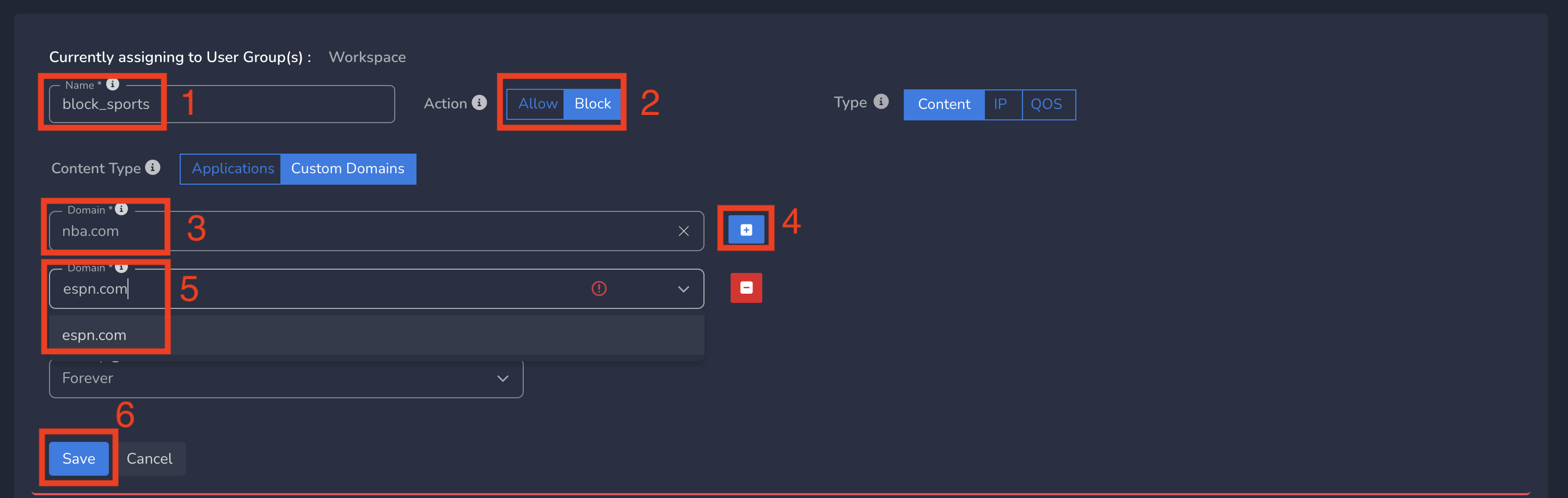
Web Domain policies gets applied to all users in workspace immediately after submit.
¶ Group level Web Domain Policies
You can define web domain policies at group level which will be applied to all users in that group. To create web domain policies, Follow below steps
- Log into the partner admin console and navigate to the company workspace.
- Click on Zero-Trust Policies in the left menu bar and Click on Rules
- Select group from drop down and click on Add Rule as shown below
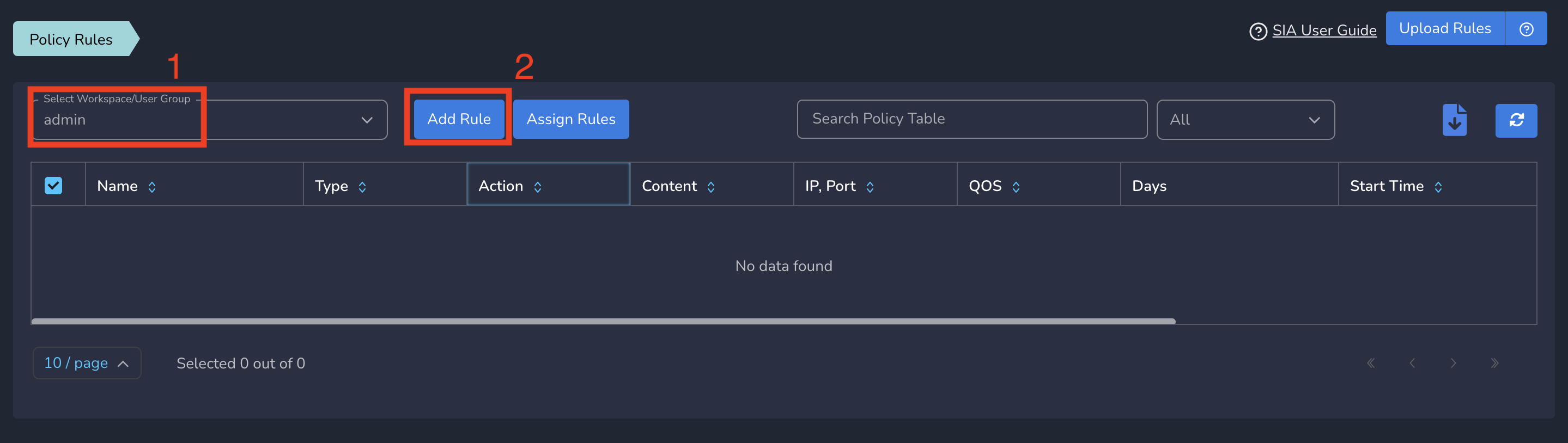
On Create Policy form, follow below steps
- Enter a name for policy
- Select Action as Allow/Block (based on requirement). By default, Block is selected.
- Enter the domain. Some domains are pre populated. If the domain you are entering shows up in drop down, you can select
- Optionally multiple domains can be added by clicking on + icon next to first domain
- Finally click on Save as shown below
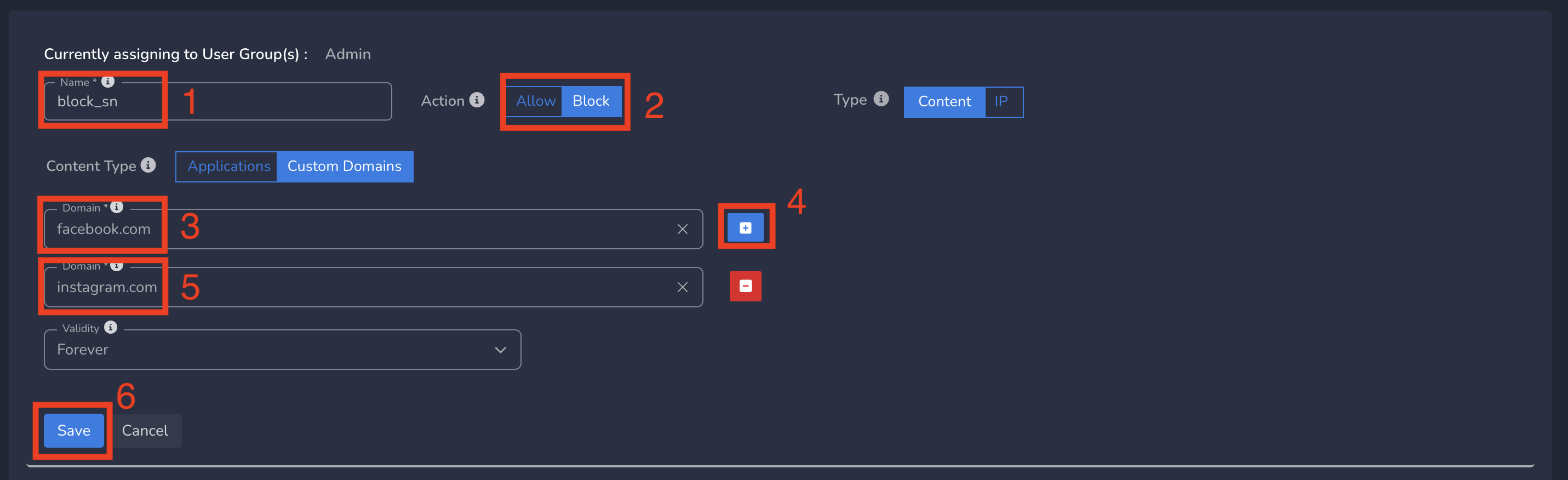
Web Domain policies gets applied to all users in that group immediately after submit.
¶ User level Web Domain Policies
You can define web domain policies at user level which will be applied to that user. To assign web domain policies to user, Follow below steps
You can define the policy as shown in above step. You can select “All” in policies table before creating the policy
To Assign the policy to User, follow below steps
- Click on Users and Devices in the left menu bar and Click on Users
- Select the user and click on username as shown below
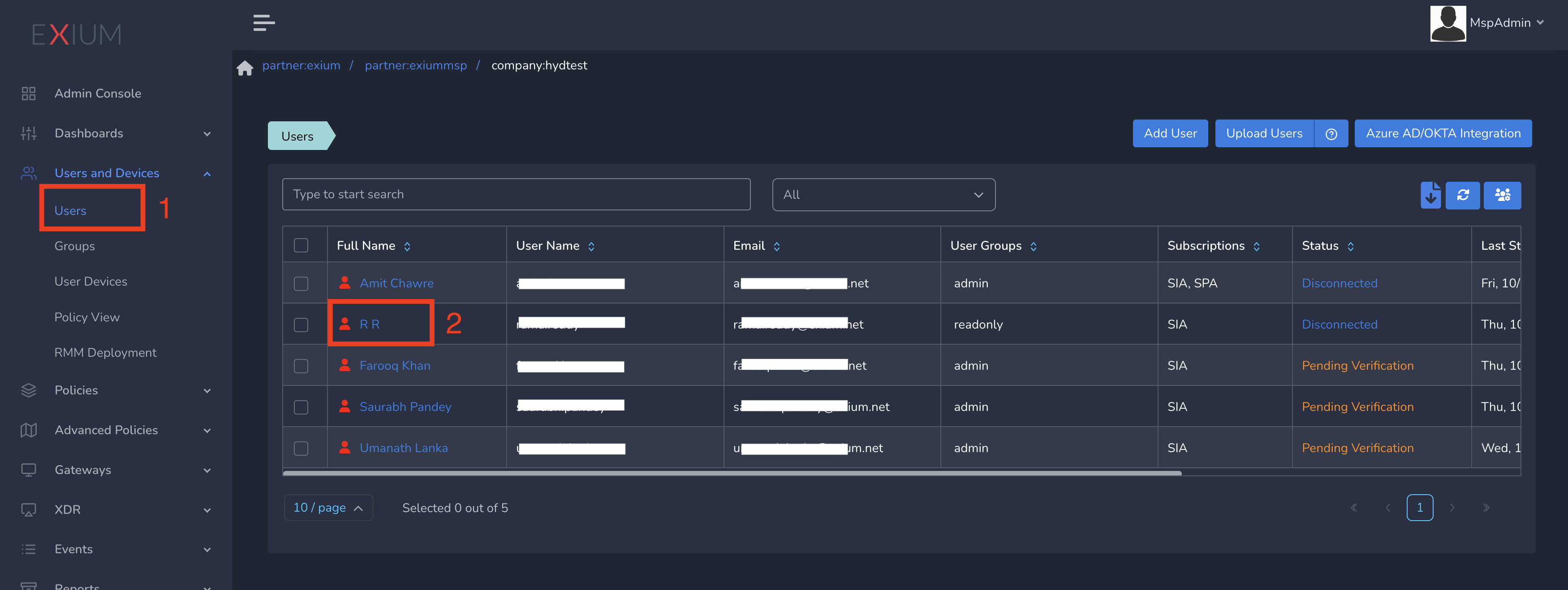
- Select Policy from drop down and Submit as shown below
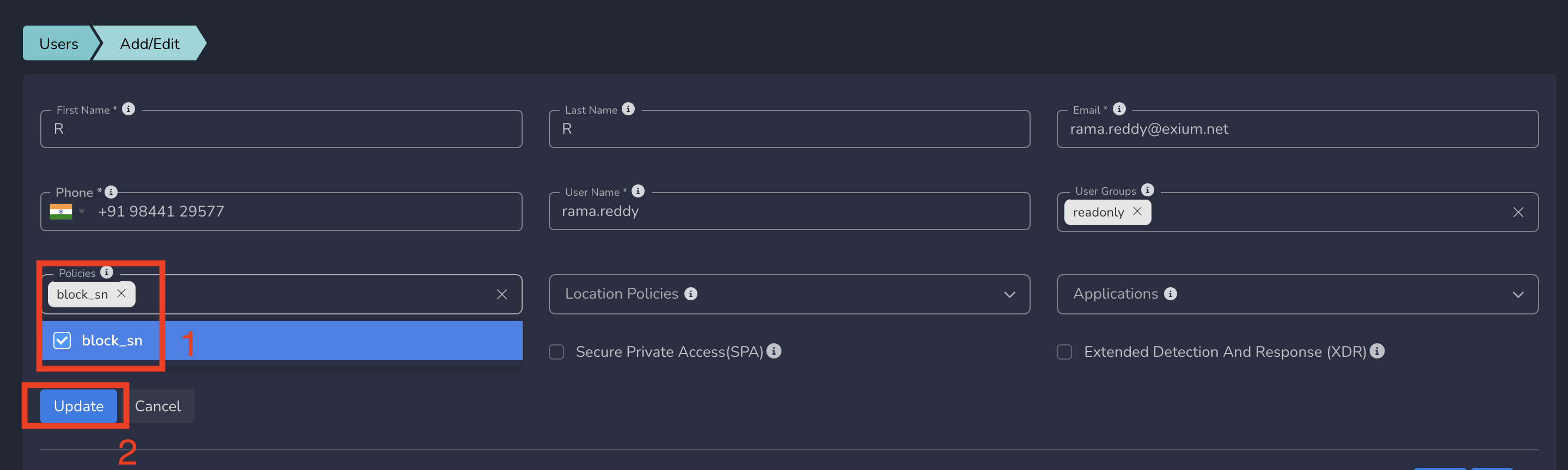
Web Domain policies gets applied to that user immediately after submit.
¶ IP (Firewall) Policies
IP (Firewall) Policies enable admins to configure ALLOW/BLOCK specific destination IP address (along with port/protocol).
¶ Workspace level IP Policies
You can define IP policies at workspace level which will be applied to all users in workspace. To create IP policies, Follow below steps
- Log into the partner admin console and navigate to the company workspace.
- Click on Zero-Trust Policies in the left menu bar and Click on Rules
- Select workspace from drop down and click on Add Rule as shown below

On Create Policy form, follow below steps
- Enter a name for policy
- Select Action as Allow/Block (based on requirement). By default, Block is selected.
- Select Type as IP
- Enter the IP
- Optionally you can select protocol type and port(s)
- Finally click on Save as shown below
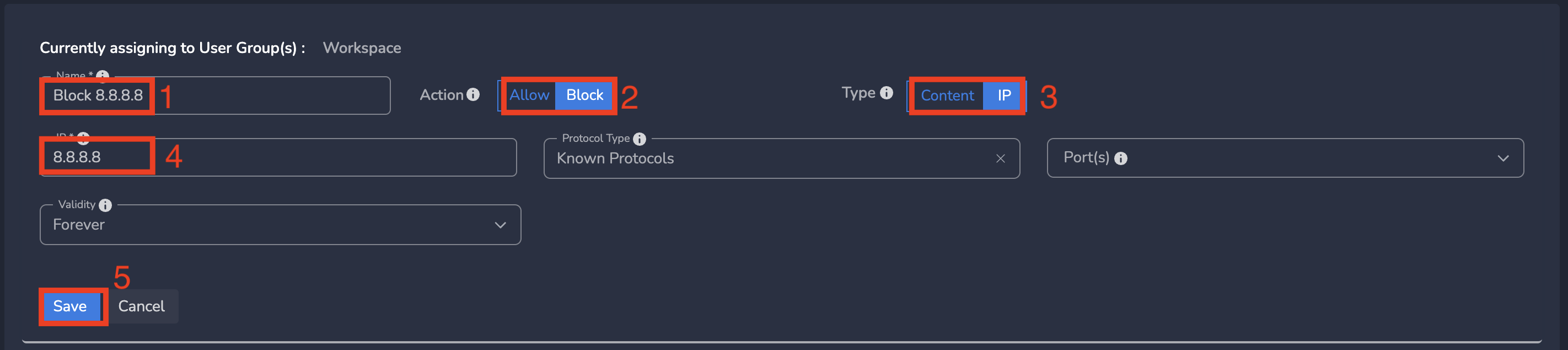
IP policies gets applied to all users in workspace immediately after submit.
¶ Group level IP Policies
You can define IP policies at group level which will be applied to all users in that group. To create IP policies, Follow below steps
- Log into the partner admin console and navigate to the company workspace.
- Click on Zero-Trust Policies in the left menu bar and Click on Rules
- Select group from drop down and click on Add Rule as shown below

On Create Policy form, follow below steps
- Enter a name for policy
- Select Action as Allow/Block (based on requirement). By default, Block is selected.
- Select Type as IP
- Enter the IP
- Optionally you can select protocol type and port(s)
- Finally click on Save as shown below
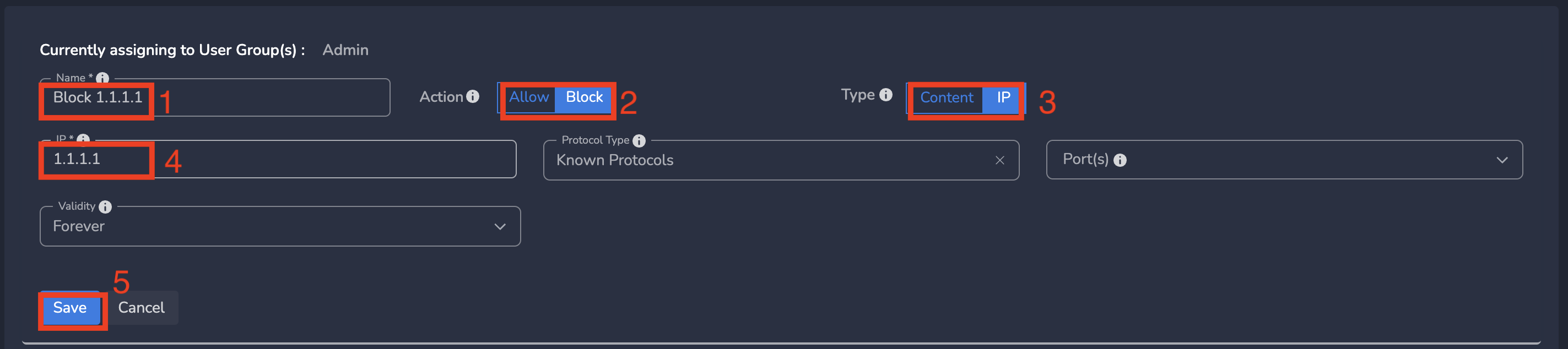
IP policies gets applied to all users in workspace immediately after submit.
¶ User level IP Policies
You can define IP policies at user level which will be applied to that user. To assign IP policies to user, Follow below steps
You can define the policy as shown in above step. You can select “All” in policies table before creating the policy
To Assign the policy to User, follow below steps
- Click on Users and Devices in the left menu bar and Click on Users
- Select the user and click on username as shown below

- Select Policy from drop down and Submit as shown below
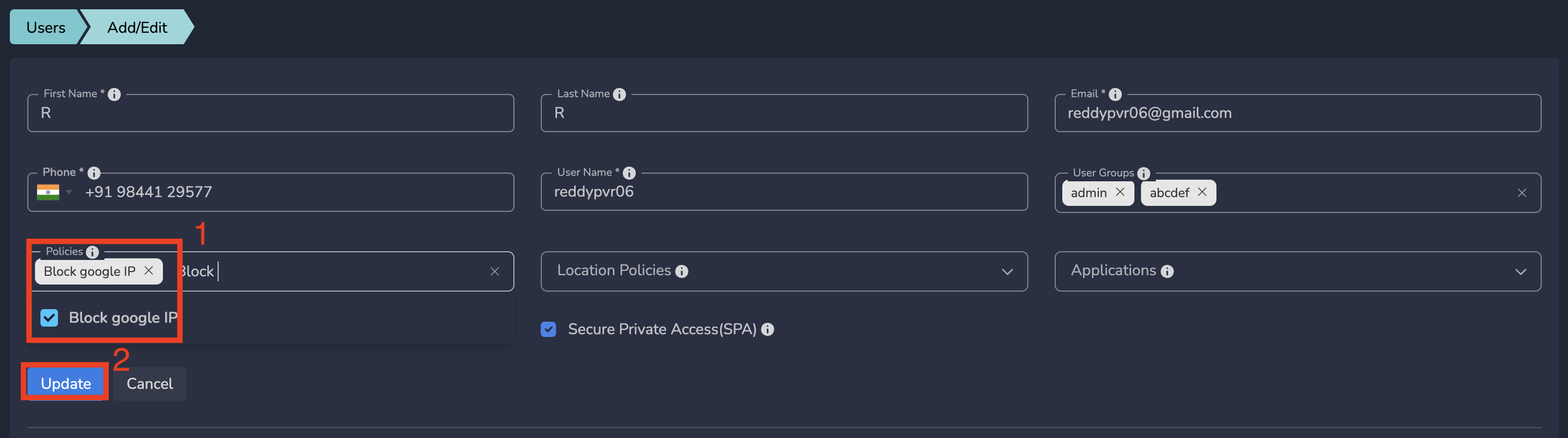
IP policies gets applied to that user immediately after submit.
¶ Override Policies and Policy Precedence View
When a user belongs to multiple groups and if the same domain is defined in multiple policies attached to multiple groups or workspace, the domain rule part of a group which has highest level of precedence will be applied. At workspace level, web domain policies will take precedence over web category policies.
We provide some examples below to clarify this. For all the examples, userA is assumed to be a part of a group groupA.
- If Sports Category is Blocked and if
fifa.comis Allowed at workspace level, for all users part of workspace (including userA),fifa.comwill be allowed and all other sports domains will be blocked. - If Sports Category is Blocked and if
fifa.comis Allowed at groupA level, for all users part of the groupA (including userA),fifa.comwill be allowed and all other sports domains will be blocked. For the users not in groupA,fifa.comwill be blocked. - If Sports Category is Blocked and if
fifa.comis Allowed at userA level, for userA,fifa.comwill be allowed and all other sports domains will be blocked. For all other users,fifa.comwill be blocked. - If Sports Category is Blocked,
fifa.comis Allowed at groupA level andfifa.comis blocked at userA level, for userAfifa.comwill be blocked, for all users part of groupA (excluding userA),fifa.comwill be allowed and all other sports domains will be blocked. For the users not in groupA,fifa.comwill be blocked.
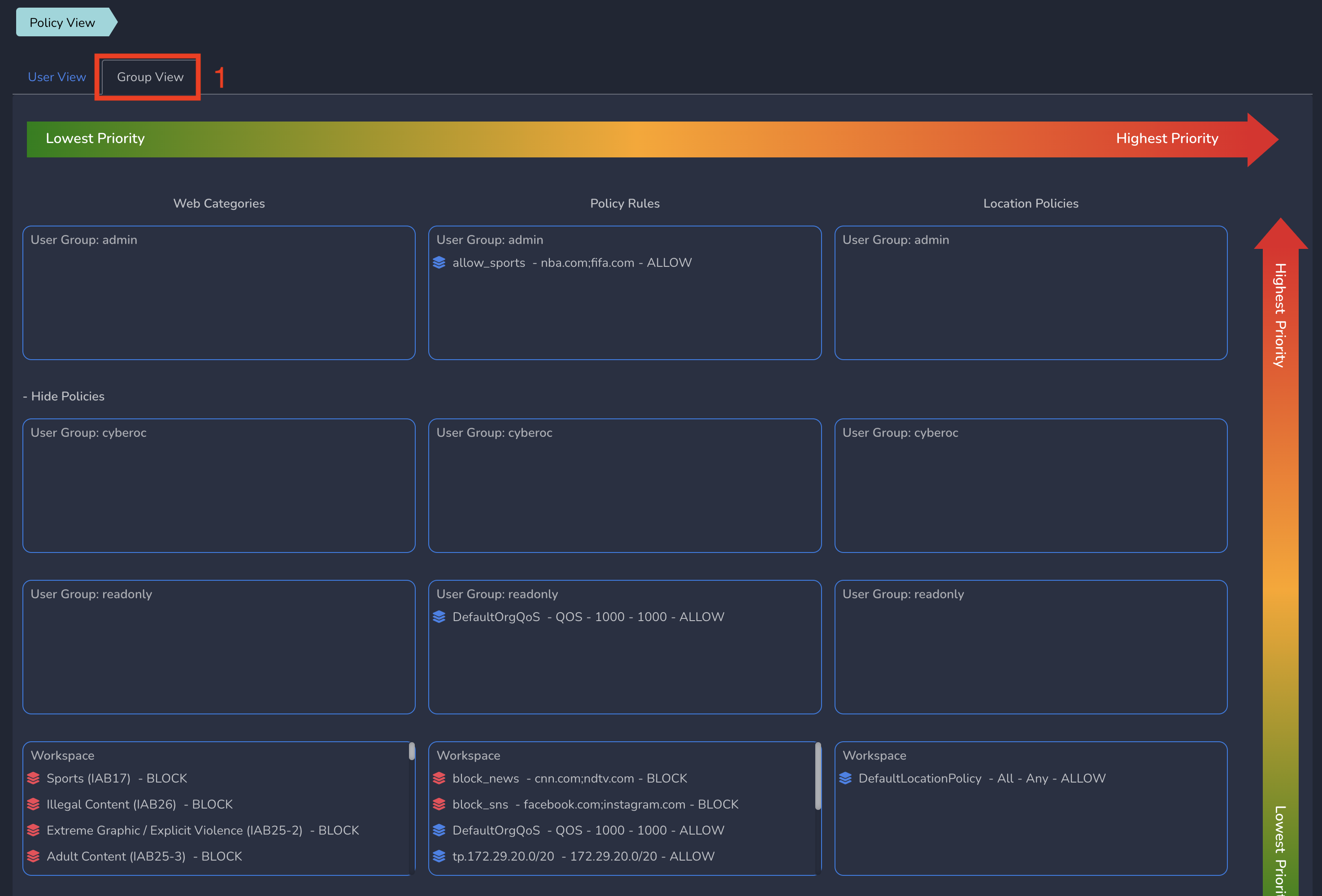
Exium provides Policy Precedency View (Generic Group level view and per user view) which will help admins to get an overview of all the policies placed in different groups and workspace level in the order of precedence.
To view Overall policy view, Click on Policy View under Users and Devices in left menu bar and select Group View tab as shown below
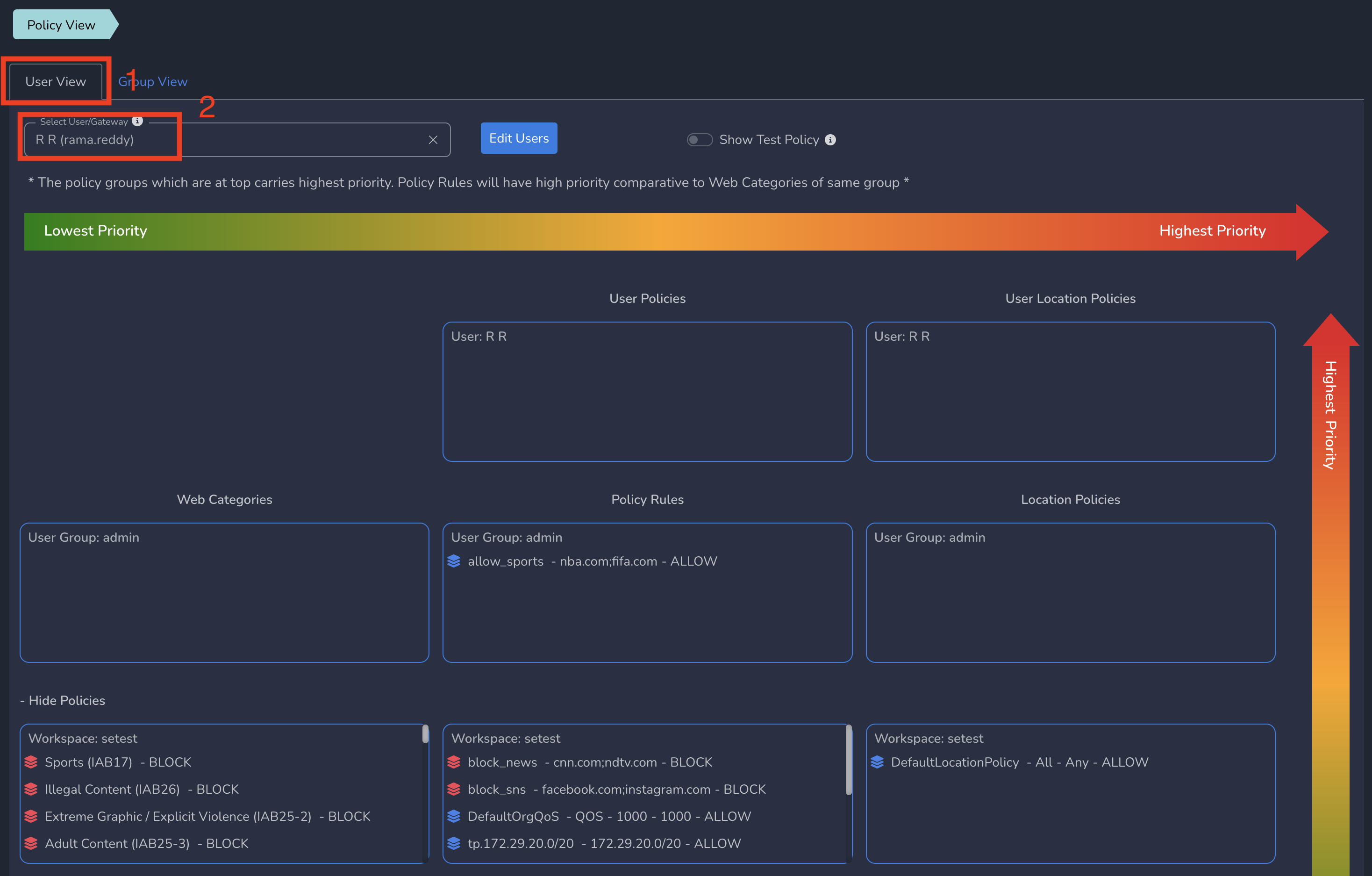
To view User level policy view, Click on Policy View under Users and Devices in left menu bar and select User View tab. Select a User from drop down as shown below
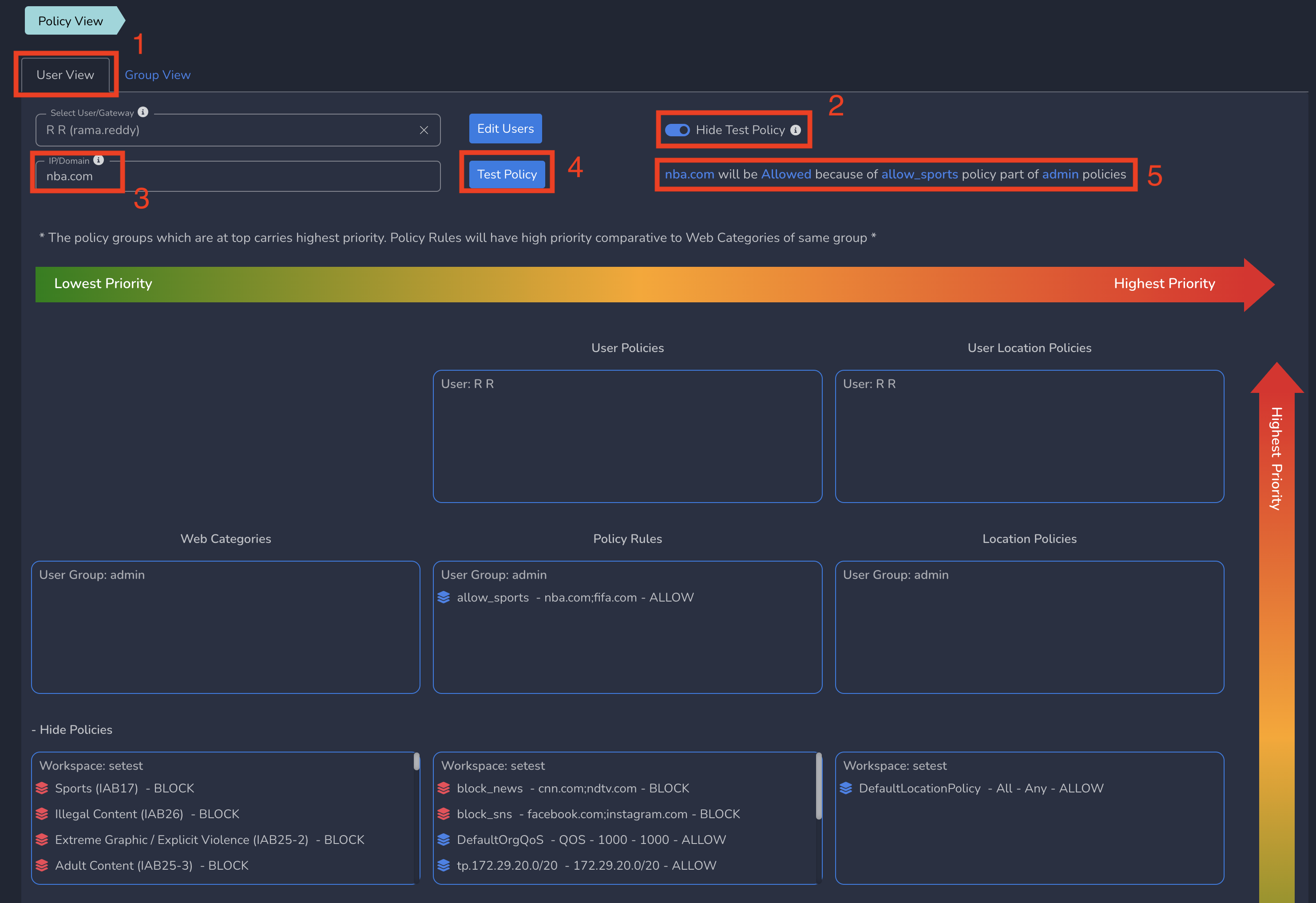
You can also use this page to test a domain at user level to check if that domain will be blocked for that user or not. In User View, you can enter a domain and see the result as shown below.
¶ Creating and Applying Grouped Policies
Create aggregate policies similar to blocked web categories at group level as shown below and add exceptions.
¶ Managing Applied (Blocked) Policies
When policies are blocked as pert of enforcement of policies, those Blocked Threat/Policies are visible on admin console. For more details, refer Management of Blocked Threats/Policies document.
To learn more about implementing SASE for your organization and explore tailored solutions that meet your unique requirements, contact Exium at hello@exium.net for a consultation or demonstration.