¶ Google SAML SSO Integration
Exium’s Intelligent Cybersecurity Mesh provides secure access to distributed workforce and IoT devices, protecting businesses from malware, ransomware, phishing, denial of service, and botnet infections in one easy to use cloud service.
Google Exium integration handles users seamless access to Exium. Administrators can easily attach Exium security policy groups to Google users. Unique features of this integration are
- Simple steps to integrate Google API with Exium
- Push New Users from Google to Exium
- Push User Deactivation from Google to Exium
- Reactivate Users from Google to Exium
- Single sign-on from Google to sign-on to Exium
This note explains how to configure Google Exium application settings and Exium Workspace settings so that Google Users can be synced with Exium Workspace in real time and SSO from Google can be used to sign-on to Exium Service.
Following steps elaborate Google SAML2 API Integration with Exium
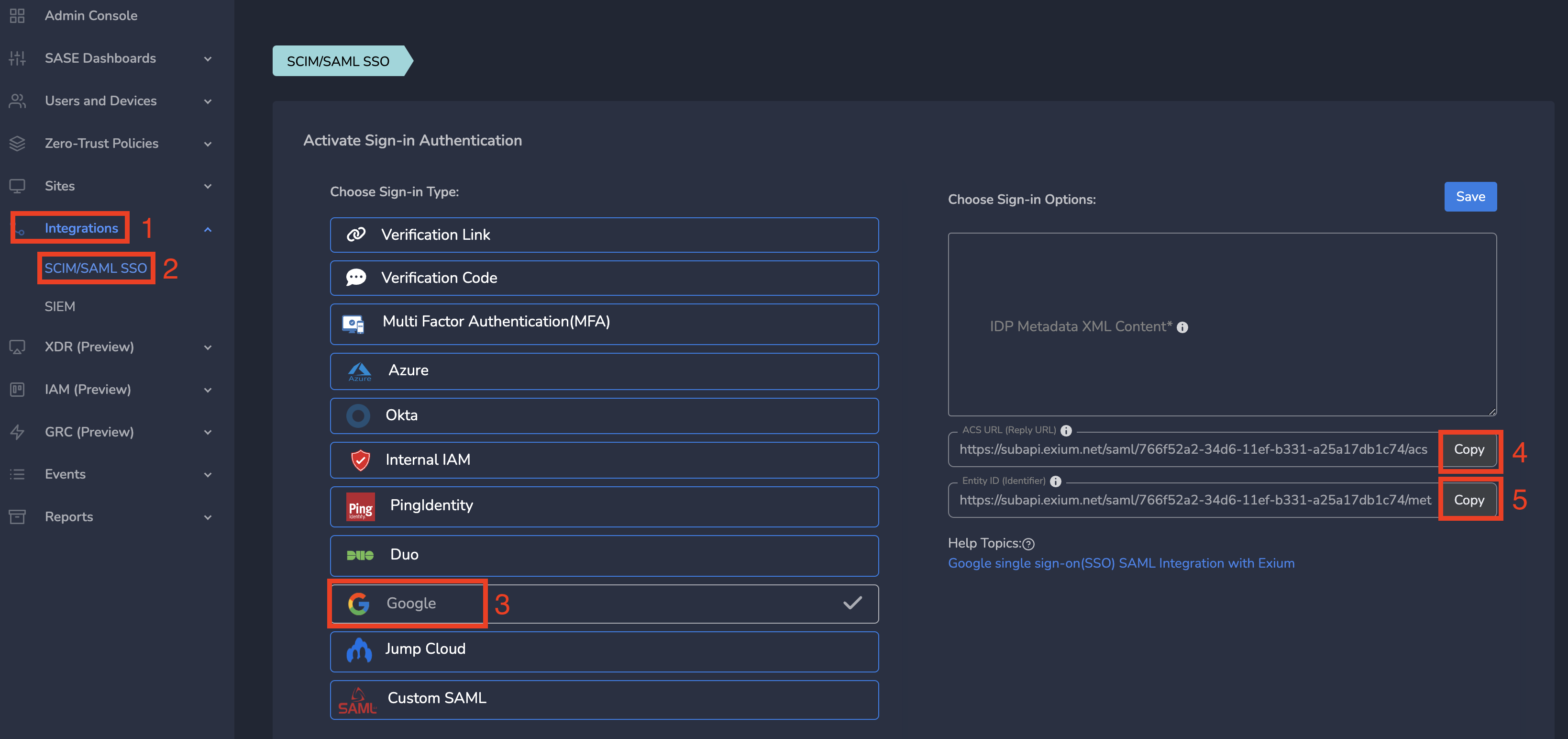
¶ 1. Select Google as Sign-in Option on Exium
As a first step, configure Google as Sign-in Type. Follow below steps.
- Navigate to the MSP admin console → Companies
- Click on Integrations → SCIM/SAML SSO
- Select Google as Sign-In Type
- Copy ACS URL (Reply URL) and Entity ID (Identifier) one after other to paste in Duo as explained in next step.
¶ 2. Create Exium app on Google
In your Google admin account (admin.google.com), you can create Exium application by creating custom SAML app with required configuration settings. On left nav bar, click on Apps, expand it and then click on Web and mobile apps. Click on Add app on top bar, expand it and then click on Add custom SAML app as shown below.

¶ 2.1 Enter App details
Enter App name and Description. Optionally, you can also upload an App icon and click on Continue.

¶ 2.2 Download Identity Provider (IdP) Metadata
Click on Download Metadata. This will download GoogleIDPMetadata.xml to your desktop. This file content has to be copied to Exium portal in step 3. Click on Continue.

¶ 2.3 Update Service Provider (SP) Details
On Service provider details, paste ACS URL (ACS URL on Exium Portal) and Entity ID (Entity ID on Exium Portal) from Exium Portal(copied on step 1). Click on Name ID Format and select EMAIL. Click Continue.

¶ 2.4 Update Attribute Mapping
On Attributes section, click on ADD MAPPING, select First name from drop down under Google Directory attributes and enter firstname under App attributes.
Click on ADD MAPPING, select Last name from drop down under Google Directory attributes and enter lastname under App attributes.
Click on ADD MAPPING, select Phone number from drop down under Google Directory attributes and enter mobile under App attributes.
After all details are entered as shown below, click on FINISH.

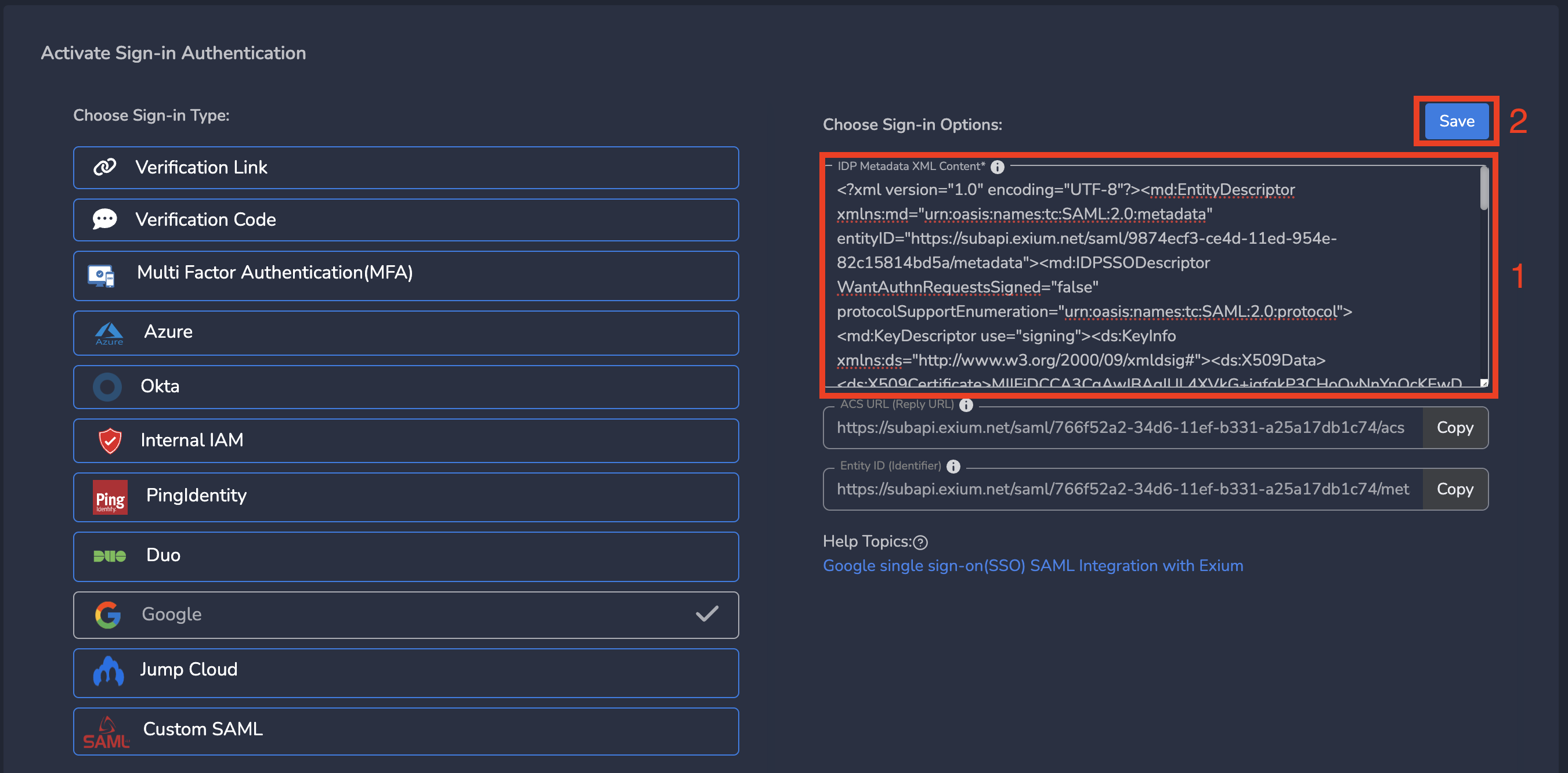
¶ 3. Update Metadata XML on Exium Portal
As a next step, Sign-in option on Exium Portal has to be saved by filling-in IDP Metadata XML Content. The contents of this metadata xml shall be copied from Metadata file downloaded on step 2.2.
Open the GoogleIDPMetadata.xml downloaded on step 2.2 with any editor locally available. Select file contents and copy to clipboard. Paste the contents on IDP Metadata XML Content as shown below and click Save.
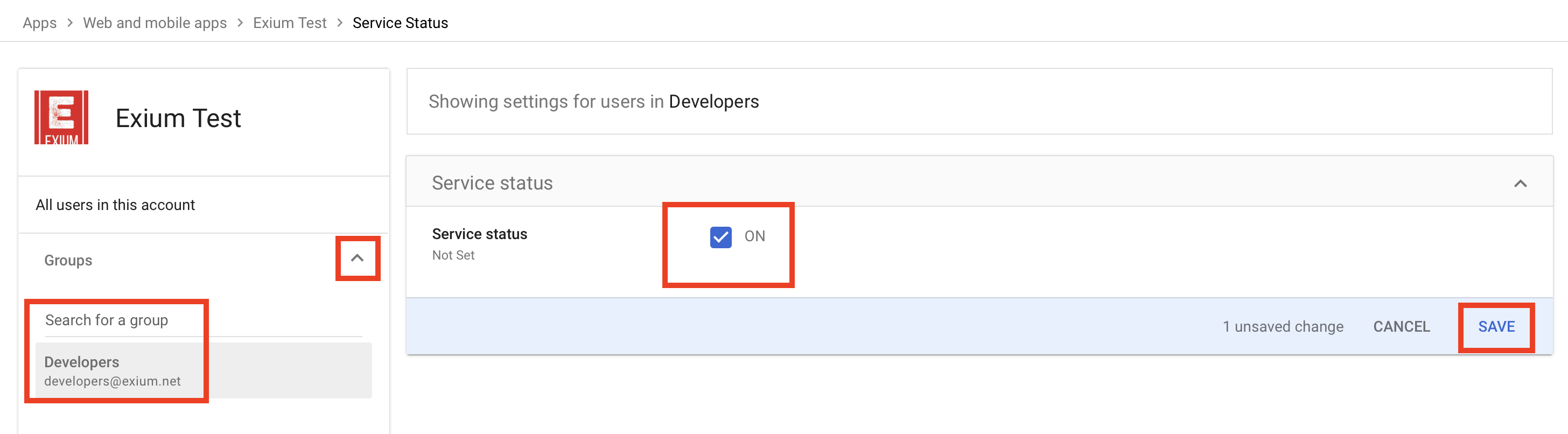
¶ 4. Assigning User Groups on Google
As a next step, you can assign user groups to Exium app on Google. This can be done whenever you wish to add more users or groups to Exium app. Click on Expand(V) icon on top right corner of User access section as shown below.

Click on Expand(V) icon on Groups on left nav bar. Search for a group by entering few characters, select a group. Click on select box next to ON for Service Status and then click Save as shown below.
¶ 5. Verify SSO on Exium Service URL
If you are part of admin group, you can access admin console through SSO. you can press your workspace name on service portal by entering the workspace name. Browser opens one more tab for google authentication. (Note: Some browsers block popups. You need to allow the popup to allow one more tab to be opened to take google authentication)

After successful authentication, it’ll show the message that “User is successfully Verified.” You can close the tab, then you’ll be in admin console in the original tab where you have entered workspace name. If the SSO verified user is not part of admin user, it gives an error that you don’t have access
If you have any issue during integration, contact us at support@exium.net or raise a ticket on https://exium.net/help-center/
If you would like to see how Exium can help defend your organisation, contact us at hello@exium.net