¶ What is Port Forwarding?
Port forwarding, or port mapping, allows remote servers and devices on the internet to access the devices that are within your private local-area network (LAN) and vice versa.
Essentially, port forwarding maps an external “port” on your internet-facing IP address to a particular computer on your local private network. This allows you (or someone else) to access something on your computer from the internet.
¶ How to Setup Port Forwarding?
To Configure Port Forwarding, follow the steps below:
- Navigate to the MSP admin console -> Client Workspace
- Click on Sites in the left menu bar → Local Policies
- Click on Port forwarding tab
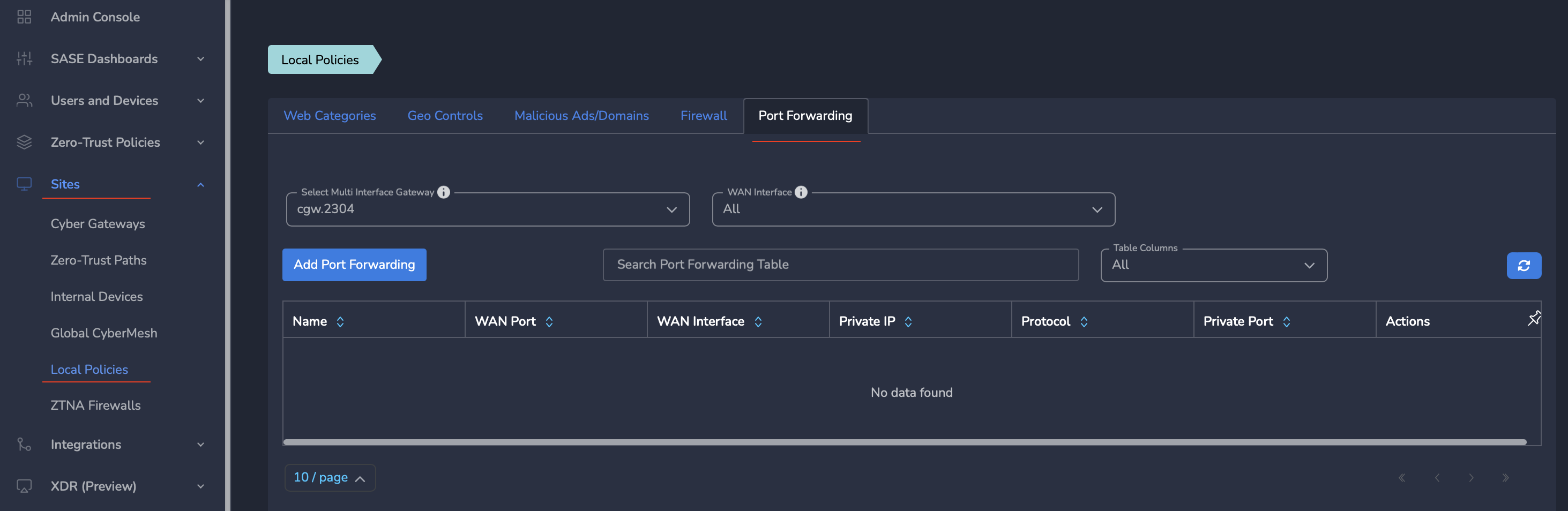
- Click on Add Port Forwarding
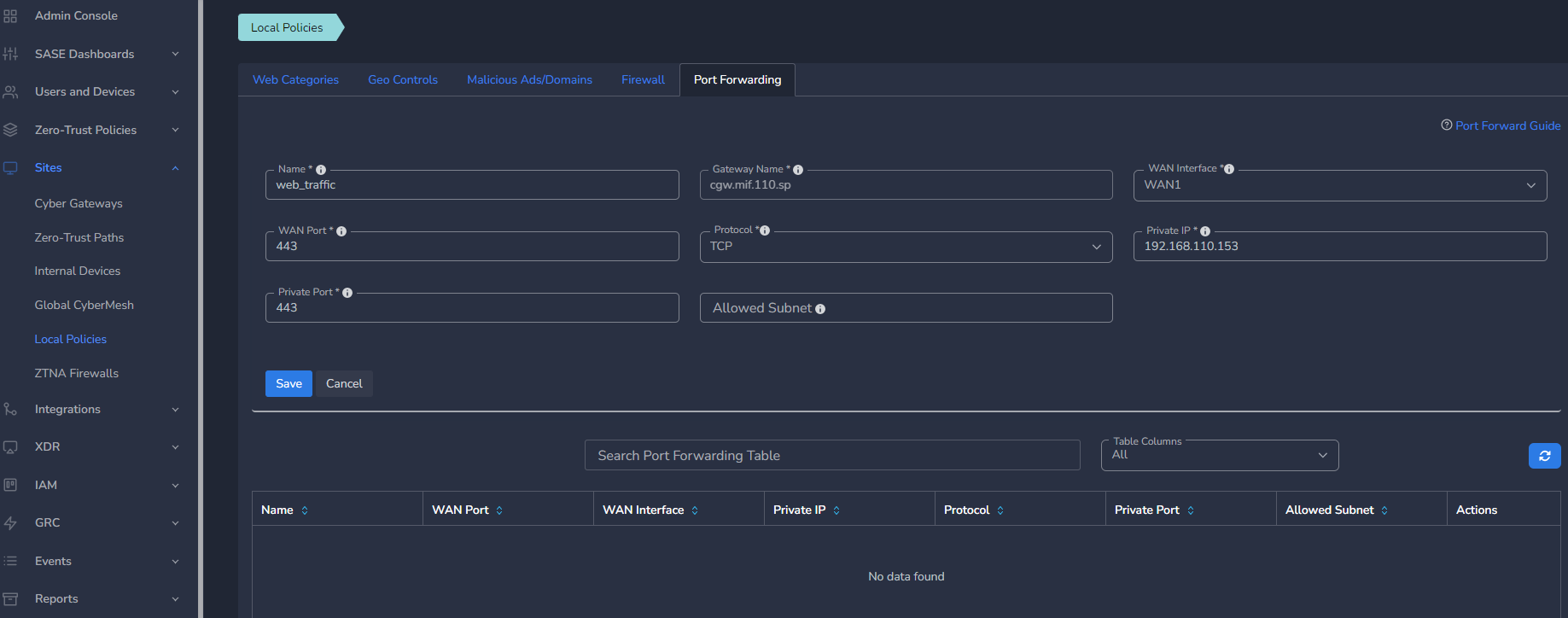
- Enter Name for the port forwarding rule
- Select WAN Interface (If multi-WAN Interface is configured)
- Add Public/WAN Port, and select Protocol
- Add Private IP and Private Port (Target local network IP and port of machine behind CGW, for port forwarding)
- Allowed Subnet is an optional field.
- If provided, only that subnet or IP will be allowed to use port forwarding
- If not provided or blank, there will be no restriction
- Click on Save, Configuration will be applied on CyberGateway immediately.
- Admin can edit/update/delete the rule later as per their requirement.
¶ How to Delete Port Forwarding?
To Delete Port Forwarding, follow the steps below:
- Navigate to the MSP admin console -> Client Workspace
- Click on Sites in the left menu bar → Local Policies
- Click on Port forwarding tab
- On Port forwarding table, scroll to Actions column and Click on Delete action as shown below.
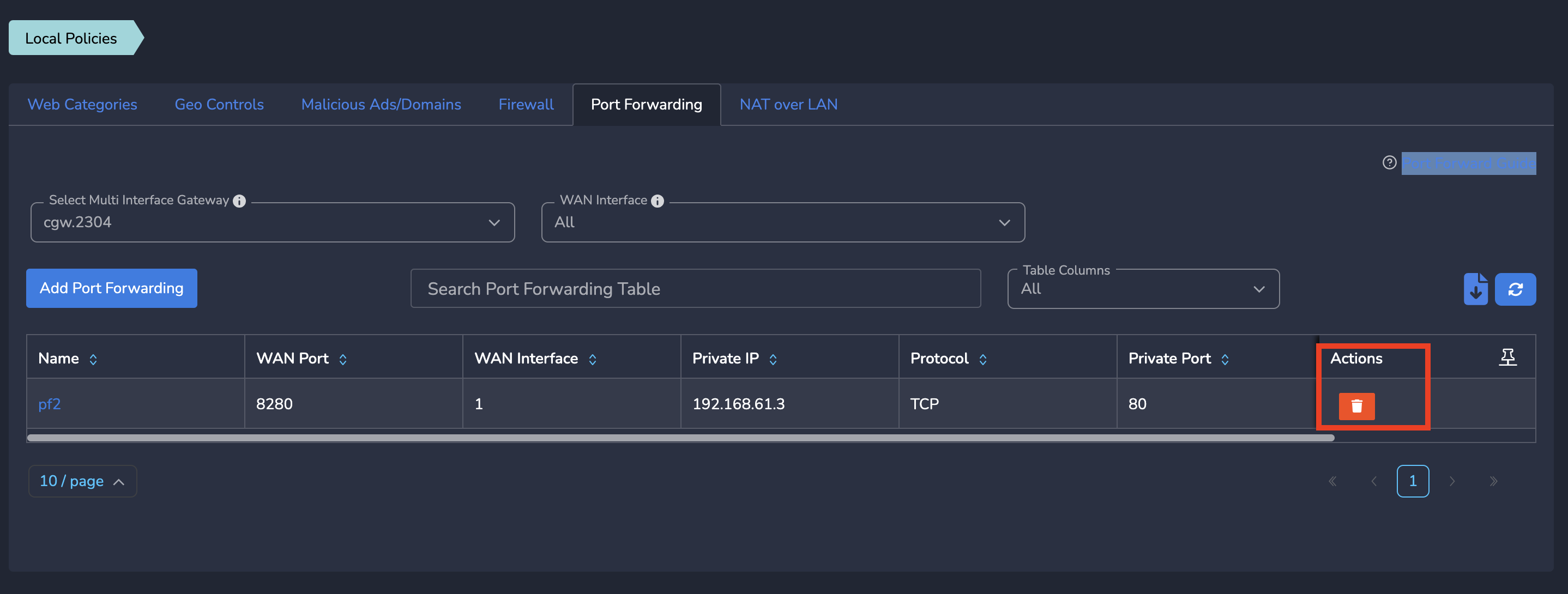
- Click on Delete on confirmation window and it'll delete the port forwarding rule
¶ Troubleshooting
- If CGW machine is running on a public cloud, then make sure the WAN port configured for port forwarding is allowed to be accessed.
- For eg., if CGW is running on Azure cloud, then make sure that WAN interface on CGW has inbound rules configured in Network Security Group (NSG) to allow WAN port configured for port forwarding. WAN interface should have any rules or NSG to block the traffic from public internet except you would like to allow specific IPs to use port forwarding.
¶ How to debug if traffic is not received on WAN interface of Azure VM?
¶ 1. Check Public IP Assignment
- Ensure the VM has a public IP address:
- Go to the Azure portal → Virtual Machines → Your VM → Networking.
- Confirm that the VM has a public IP assigned under the Public IP address section.
¶ 2. Verify Network Security Group (NSG) Rules
The Network Security Group (NSG) may be blocking the incoming traffic.
Steps to check:
- Go to Virtual Machines → Select your VM → Networking.
- Under Inbound port rules, verify if there’s a rule allowing traffic on the required port (e.g., SSH on port 22, RDP on port 3389, HTTP on port 80, HTTPS on port 443).
- Ensure the Source is set to allow traffic from the internet (
Anyor specific allowed IP range). - Ensure the Protocol is correctly set to
TCP,UDP, orAny, depending on your traffic type. - Check that the rule Priority is lower (higher priority) than any blocking rules.
You can also use the IP Flow Verify feature in Network Watcher to check if the NSG rules are correctly configured for specific source and destination addresses.
¶ 3. Check VM Operating System Firewall
Sometimes the VM's internal firewall may block incoming traffic even if the Azure NSG is configured correctly.
Check iptables or ufw:
Ensure that the firewall allows traffic on the port you are trying to use (e.g., 22 for SSH, 80 for HTTP, 3389 for RDP).
¶ 4. Use Azure Network Watcher
Network Watcher provides tools to monitor and troubleshoot networking issues.
- IP Flow Verify: This tool allows you to check whether a specific flow (source IP, destination IP, and port) is allowed or denied by NSGs. If the flow is denied, it will also show which NSG rule blocked the traffic.
- Go to Azure Network Watcher → IP Flow Verify → Select the VM → Enter source/destination IP and ports to test.
- Network Security Group (NSG) Flow Logs: Enable NSG flow logs to capture detailed information about traffic flowing through your NSG.
- Go to Network Watcher → NSG Flow Logs → Enable and configure for the NSG attached to the VM.
- Connection Troubleshoot: Use the connection troubleshoot feature to test connectivity from the VM to a target destination or from external sources to the VM.
- Go to Network Watcher → Connection Troubleshoot → Select the VM → Enter the IP and port you want to test.
¶ 5. Check Azure Route Table Configuration
If custom routing is used, incorrect routes may prevent traffic from reaching your VM.
Steps to check:
- Go to Virtual Networks → Subnets → Route Table.
- Ensure there’s a route to the internet (e.g.,
0.0.0.0/0with next hop set toInternet). - Check if there are any user-defined routes that might block inbound/outbound traffic.
¶ 6. Test Connectivity Using Network Tools
Ping the VM's public IP: Ping can help check basic connectivity, although it might not work if ICMP is blocked.
Use Telnet or Netcat:
- From your local machine, try connecting to the VM's public IP on the relevant port (e.g.,
22for SSH,80for HTTP,3389for RDP).
¶ 7. Check Azure Load Balancer (if applicable)
If your VM is behind an Azure Load Balancer, ensure the load balancer is properly configured:
- Ensure the load balancer’s health probes are correctly configured and the VM is in a healthy state.
- Check the load balancer rules to ensure the correct port is being forwarded to the VM.
- Ensure that the backend pool includes the correct VM and NIC.
Please contact support@exium.net in case issue is not resolved.