¶ Introduction
Firewalls are a critical component of network security that regulate incoming and outgoing traffic based on predefined rules. In this solution brief, we will explore the importance of inbound and outbound rules, specifying IP addresses, ports, and protocols, in securing network infrastructures.
¶ Challenges
Network Security: Ensuring that unauthorized or malicious traffic is blocked while allowing legitimate traffic is a constant challenge.
Application and Service Requirements: Businesses must strike a balance between security and ensuring that necessary applications and services can function effectively.
Complex Network Topologies: In modern networks, there are diverse devices and network segments, making rule management complex.
Adaptation to Evolving Threats: As threats evolve, firewall rules must be regularly updated to remain effective.
¶ Solution: Firewall Rules and Policy
¶ Inbound and Outbound Rules
Utilize Access Control Lists (ACLs) to specify allowed or denied IP addresses, ports, and protocols for both inbound and outbound traffic.
|
|
Inbound Rules |
Outbound Rules |
|---|---|---|
| Rule-Based Configuration |
Specify rules that dictate which external sources are permitted to access internal resources |
Control which internal devices can communicate with external resources |
| Port-Based Filtering |
Define which external ports are allowed access to specific internal services |
Regulate which internal applications can use specific ports for external communication |
| Protocol Filtering |
Define rules to allow or deny specific protocols such as TCP, UDP, ICMP, and others |
|
¶ Stateful Inspection:
- Implement stateful inspection to monitor the state of active connections, allowing the firewall to make informed decisions on permitting or blocking traffic.
¶ Logging and Monitoring:
- Regularly review logs to identify unusual traffic patterns or unauthorized access attempts.
- Set up real-time alerts for suspicious activities.
¶ User and Group-Based Rules:
- Implement rules that consider the user or group identity to manage access based on authentication.
¶ Benefits of Exium's Cyber Gateway Firewall
Firewall inbound and outbound rules, specifying IP addresses, ports, and protocols, are foundational to network security. By carefully crafting and managing these rules, organizations can maintain a robust defense against threats, facilitate business operations, and ensure data security. Implementing these rules as part of an overall security strategy is essential for safeguarding modern network infrastructures. Benefits of Exium's Cyber Gateway Firewall are listed below:
|
Enhanced Network Security |
Granular Control |
Adaptability |
Compliance |
Improved Performance |
| Define and enforce specific rules to filter both inbound and outbound traffic, reducing the attack surface. | Allows for precise control over what is allowed and what is denied, enhancing network security without disrupting necessary operations. |
Easily adapt to evolving threats and changing business needs by modifying rules as necessary. |
Help meet regulatory compliance requirements by controlling data flows and access to sensitive information. | Streamline network traffic, reducing latency, and ensuring a more efficient network. |
¶ Configuring Cyber Gateway Firewall Rules
In Exium's platform, you can configure Firewall Rules both in the central admin console as well as Local Firewall Rules for the LAN traffic at a location where the Cyber Gateway is deployed.
Central Firewall Rules: Applies to remote SIA/ SPA users as well as Inter-site WAN traffic from the Cyber Gateway
Local Firewall Rules: Applies to traffic that stays at the location, typically East-West LAN traffic
¶ Configuring Central Firewall Rules
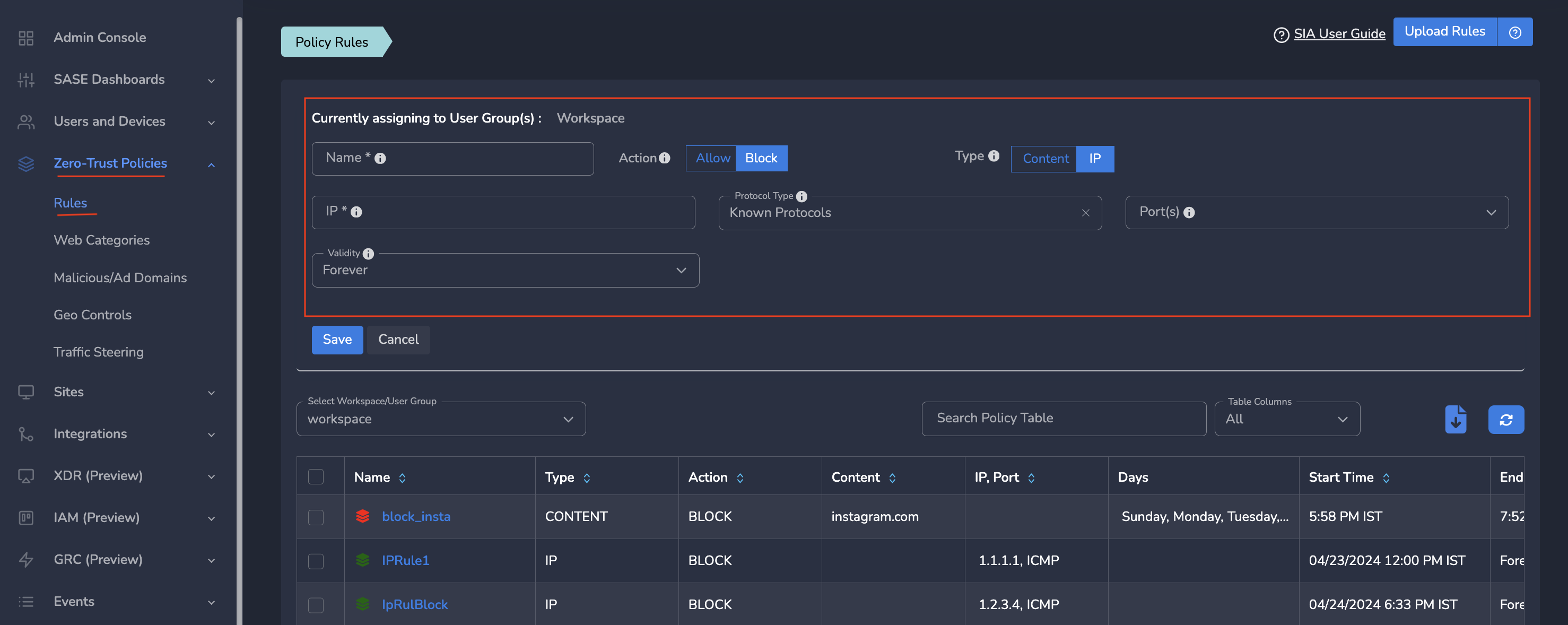
To Configure Central Firewall Rules, follow the steps below:
- Navigate to the MSP admin console -> Client Workspace
- Click on Zero-Trust Policies in the left menu bar → Add Rule
- Enter a name for the policy
- Select Type as “IP”
- Select “Allow” or "Block
- Enter the IP address or subnet you like to apply the rules to
- Select Protocol Type, Port, and Validity, and Save
¶ Configuring Site specific (CGW) Firewall Rules
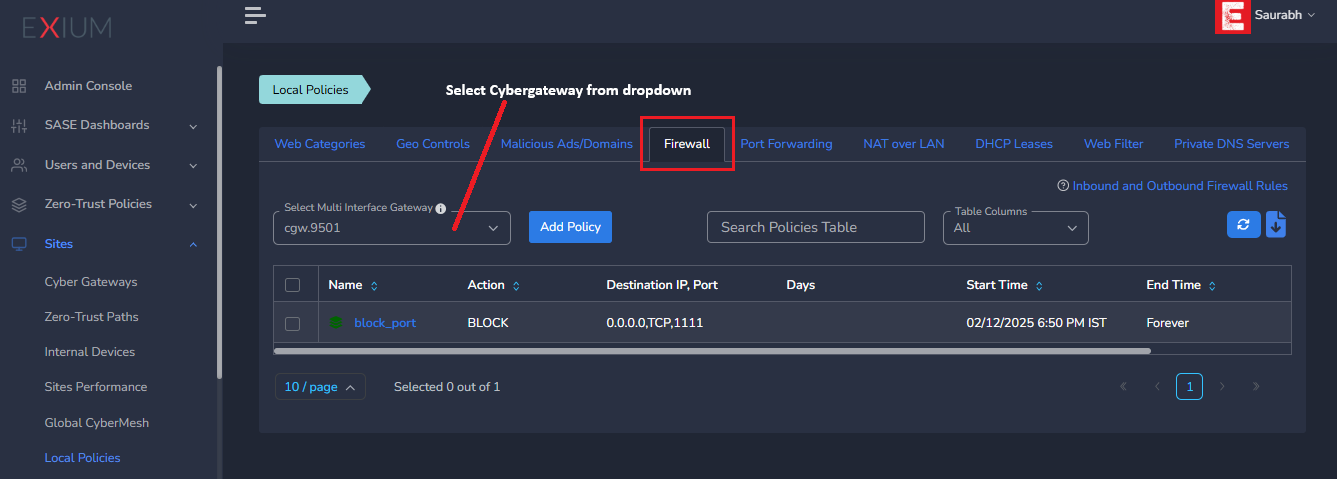
To Configure Central Firewall Rules, follow the steps below:
- Navigate to the MSP admin console -> Client Workspace
- Click on Sites in the left menu bar → Local Policies
- Select Firewall tab → select Cyber Gateway → Click on “Add Policy”
- Enter a name for the policy
- Select Type as “IP”
- Select “Allow” or "Block
- Enter the IP address or subnet you like to apply the rules to
- Select Protocol Type, Port, and Validity, and Save

To learn more about implementing SASE for your organization and explore tailored solutions that meet your unique requirements, contact Exium at hello@exium.net for a consultation or demonstration.