¶ Secure Access to Azure Resources by Integrating Azure Firewall with Exium's SASE Cloud
Easily link your Azure Firewall with Exium's SASE cloud through a Site-to-Site VPN tunnel.
¶ Prerequisites
- An active Azure subscription
- Azure login credentials with permissions to create, delete, and manage resources (e.g., resource group, virtual machines, virtual network, subnets, routes, etc.)
- A designated resource group
- A Virtual Network (VNet)
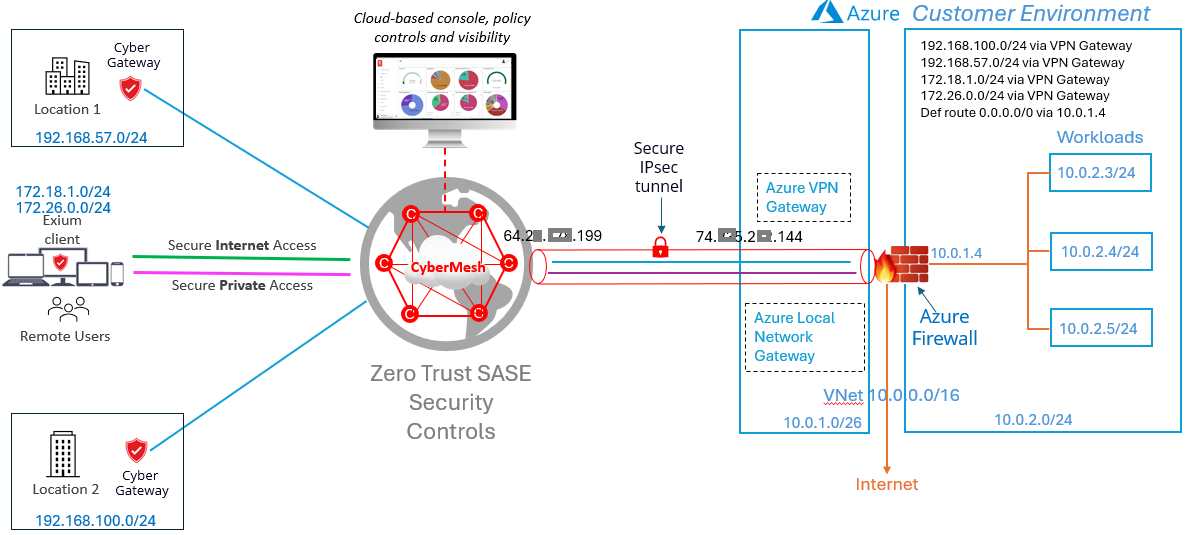
Below is a sample network diagram for your reference.
¶ Create Resource Group on Azure Cloud
Skip this section, if you want to use an existing resource group.
- Sign in to the Azure portal.
- On the Azure portal menu, select Resource groups or search for and select Resource groups from any page. Then select Create.
- For Subscription, select your subscription.
- Provide Resource group name (for e.g. - ztnafw-RG)
- Select Region. All other resources must be created in the same region.
- Select Review + create.
- Select Create.
¶ Create a Virtual Network on Azure Cloud
Skip this section and go to the next section, if you want to use an existing Virtual Network (VNet).
- On the Azure portal menu or from the Home page, search for Virtual Networks.
- Select Virtual Networks in the result pane.
- Select Create.
- For Subscription, select your subscription.
- Select Resource group
- Provide Virtual Network name (For eg. - ztnafw-VN).
- Select Region, select the same region.
- Select Next.
- For Address space, accept the default 10.0.0.0/16, or create new range, as per your requirement. Make sure subnet ranges do not overlap on both sides (Azure cloud and Exium's SASE cloud).
- Under Subnet, select default and change it to new Name (For eg. - ztnafw-workload-SN).
- For Starting address, change it to 10.0.2.0/24 (Or any other range, as pre your requirement).
- Select Save.
- Select Review + create.
- Select Create.
¶ Use Existing Virtual Network on Azure Cloud
On your Azure cloud, in case you are using existing Virtual Network (VNet), then follow below steps to configure required parameters:
- On the Azure portal menu or from the Home page, search for Virtual Networks.
- Select your Virtual Network from the list
- Go to Subnets under Settings
- Create AzureFirewallSubnet with minimum /26 range (For eg. 10.0.1.0/26). Make sure it does not overlap with other subnets in Virtual Network.
- Skip step 4, if AzureFirewallSubnet is already present.
- Create new subnet for your private resources if not already present.
- Skip step 5, if you already have subnet which is being used by your Azure workloads.
¶ Examine your Azure firewall
- Go to the resource group and select the firewall.
- Note the firewall private and public IP address. We will need these addresses later.
¶ Configure Site-to-Site Connection on Azure Cloud
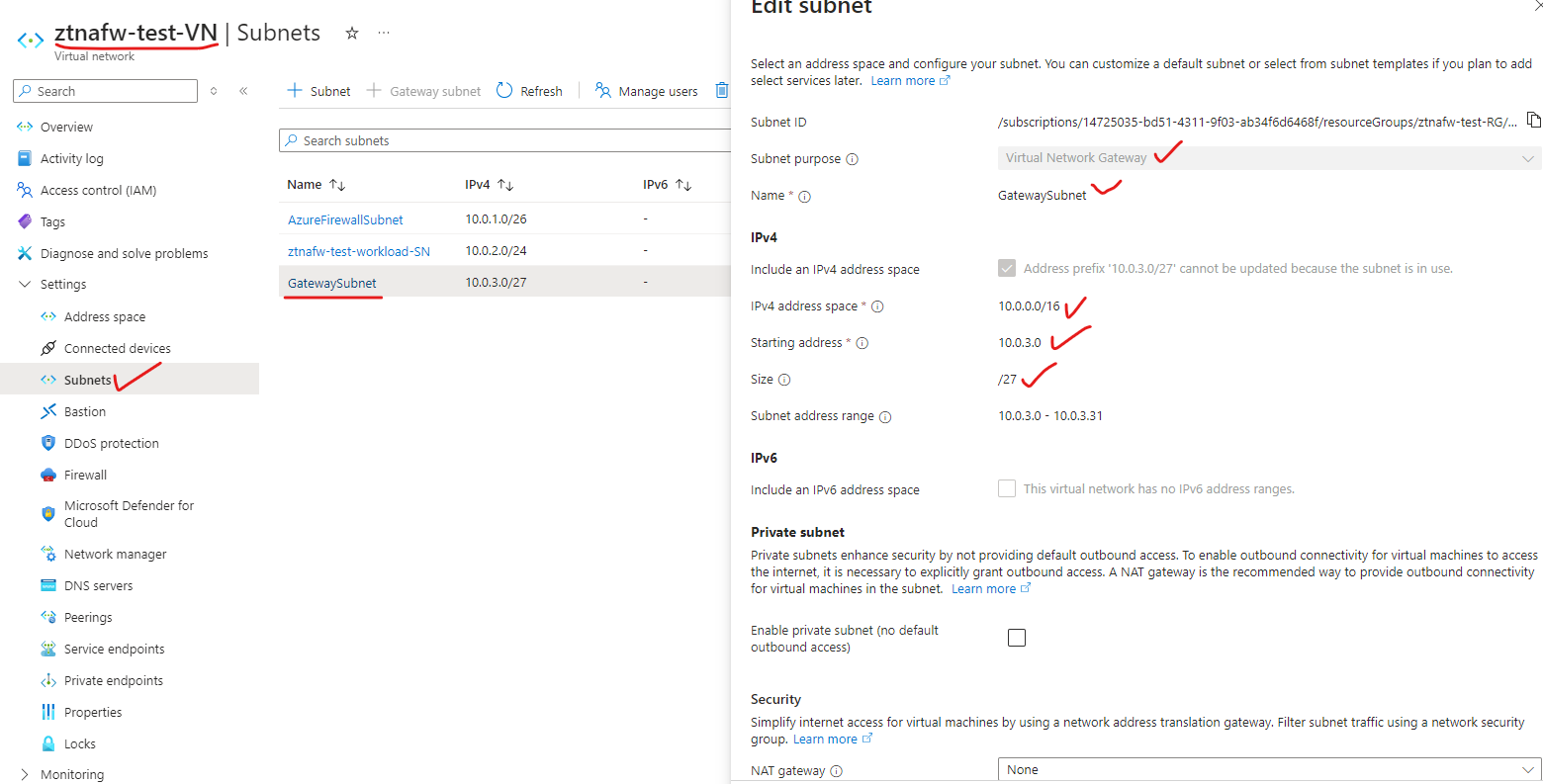
¶ Add a GatewaySubnet on Azure Cloud
The GatewaySubnet is mandatory for deploying a VPN Gateway, which is required for IPsec connectivity.
- Go to Azure Portal > Virtual Networks > Select your VNet
- Go to Subnets under Settings
- Add a new subnet,
- Subnet Purpose: Virtual Network Gateway,
- Name: GatewaySubnet
- IPv4 address space: Same as your virtual network
- Starting address: Provide starting address range (For eg. 10.0.3.0), Ensure the address space doesn’t overlap with any existing subnets (For eg. AzureFirewallSubnet, workload subnets etc.).
- Size: Minimum /27
- Do not enable IPv6 address space
- Save
Below is a sample configuration for your reference.
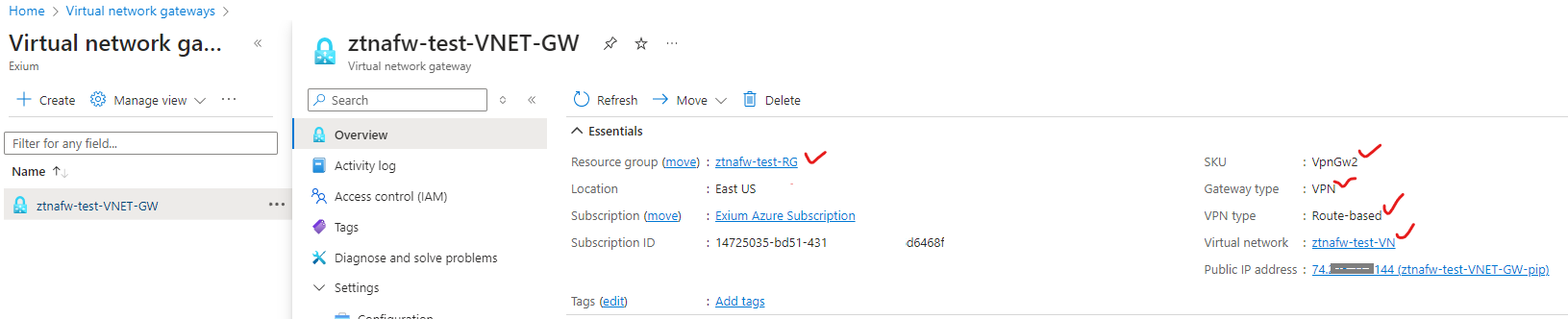
¶ Deploy the Virtual Network Gateway or VPN Gateway on your Azure Cloud
Go to Virtual Network Gateways in Azure Portal > Create.
Configuration:
- Name: provide name
- Region: Same as your resource group's region
- Gateway Type: VPN.
- VPN Type: Route-based.
- SKU: VpnGw2 (Generation2)
- Select your VNet and the new GatewaySubnet created in previous steps
- Assign a Public IP (Select Create new option) to the virtual network/VPN Gateway
- Active-active mode: Disabled
- Gateway Private IPs: Disabled
- Authentication Information: Disabled
Note the public IP of the Virtual Network gateway, it will be used on Exium's SASE cloud Admin console during configuration.
Below is a sample configuration for your reference.
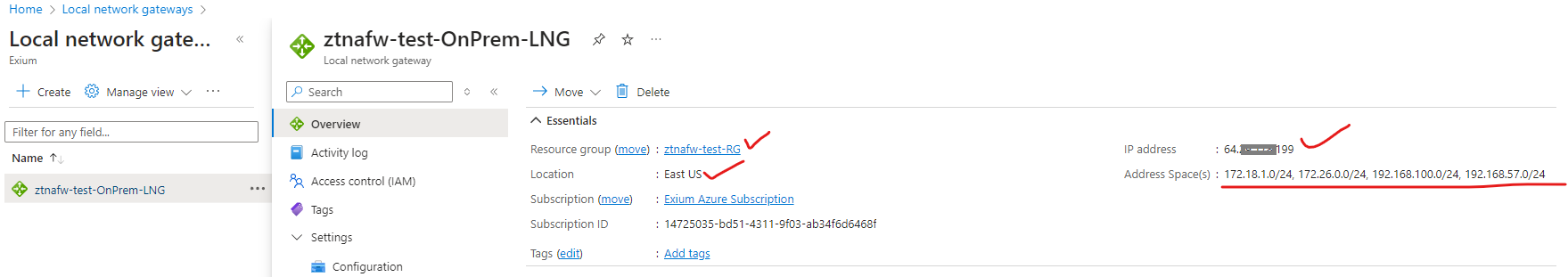
¶ Create a Local Network Gateway on your Azure Cloud
This step can be performed parallelly while you create ZTNA Firewall on admin console. Because Local Network gateway (LNG) creation needs Exium SASE Cloud endpoint's public IP as configuration parameter.
Go to Local Network Gateways > Create.
Configuration:
- Resource group: Select your resource group
- Region: Same region where your resource group is created
- Name: provide name
- Endpoint: IP address
- IP Address: Public IP of Exium SASE Cloud Endpoint (You can get it when you create ZTNA Firewall on Admin console)
- Address Space: The CIDR range of Exium's SASE Cloud network (For e.g. 172.26.0.0/24, 172.18.1.0/24, 192.168.57.0/24, 192.168.100.0/24)
- You can get subnet list when you create ZTNA Firewall on Admin console
Below is a sample configuration for your reference.
¶ Create Firewall endpoint on Exium SASE cloud
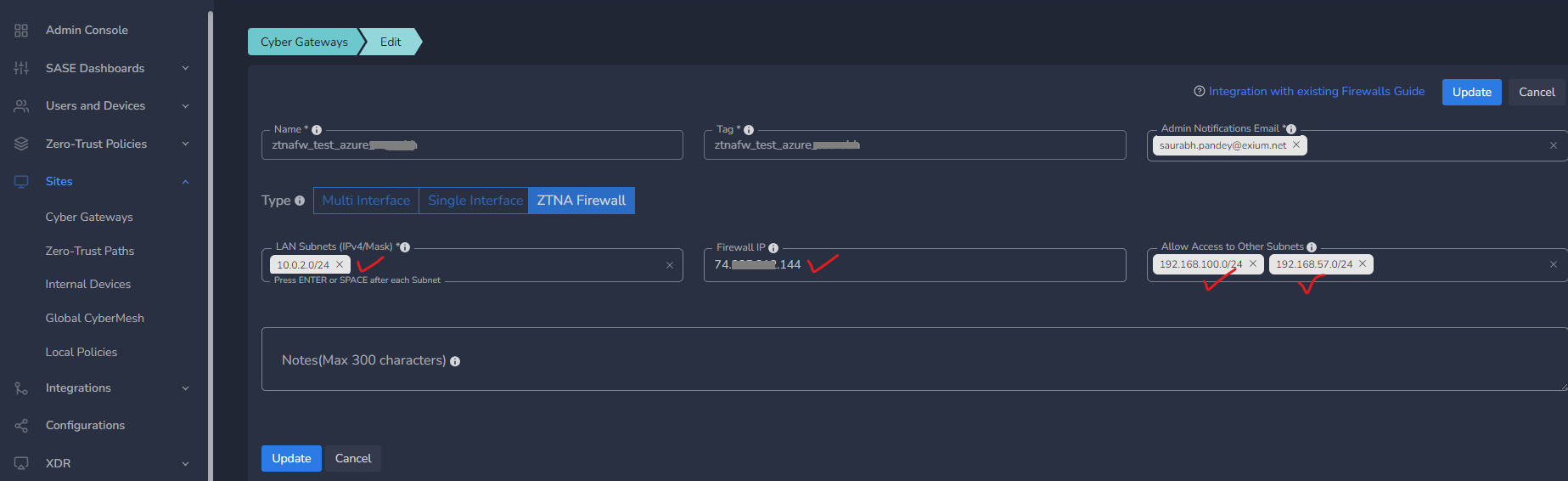
- On Add Gateway form, Enter a logical name for firewall connection
- Optionally, Enter email-ids to receive notifications for this gateway
- Select Type as ZTNA Firewall
- Enter right subnets - the subnets behind your Azure firewall to which you want to give access from Exium SASE Cloud
- Optionally, Enter the public IP of Firewall to allow connections only from that firewall. If there is no IP, Exium's SASE cloud will allow connections from any public IP.
- Enter the subnets (which are part of trust paths) behind Multi Interface Cyber Gateways in Allow Access to Other Subnets
- Optionally, Enter some Notes
- Click on Save as shown below
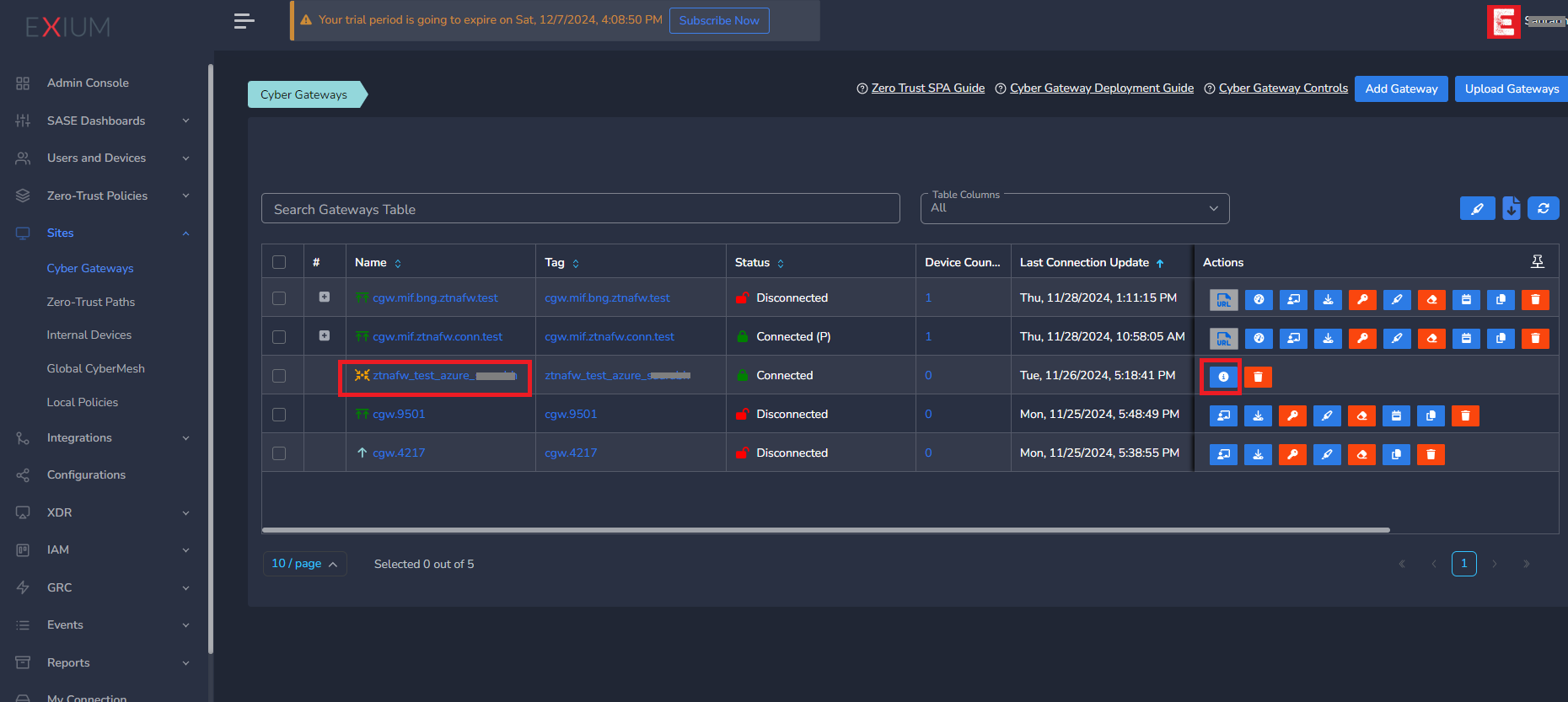
¶ Copy the required information from Exium Admin Console
On Gateways page, Click on ZTNA Firewall Info action in actions column as shown below
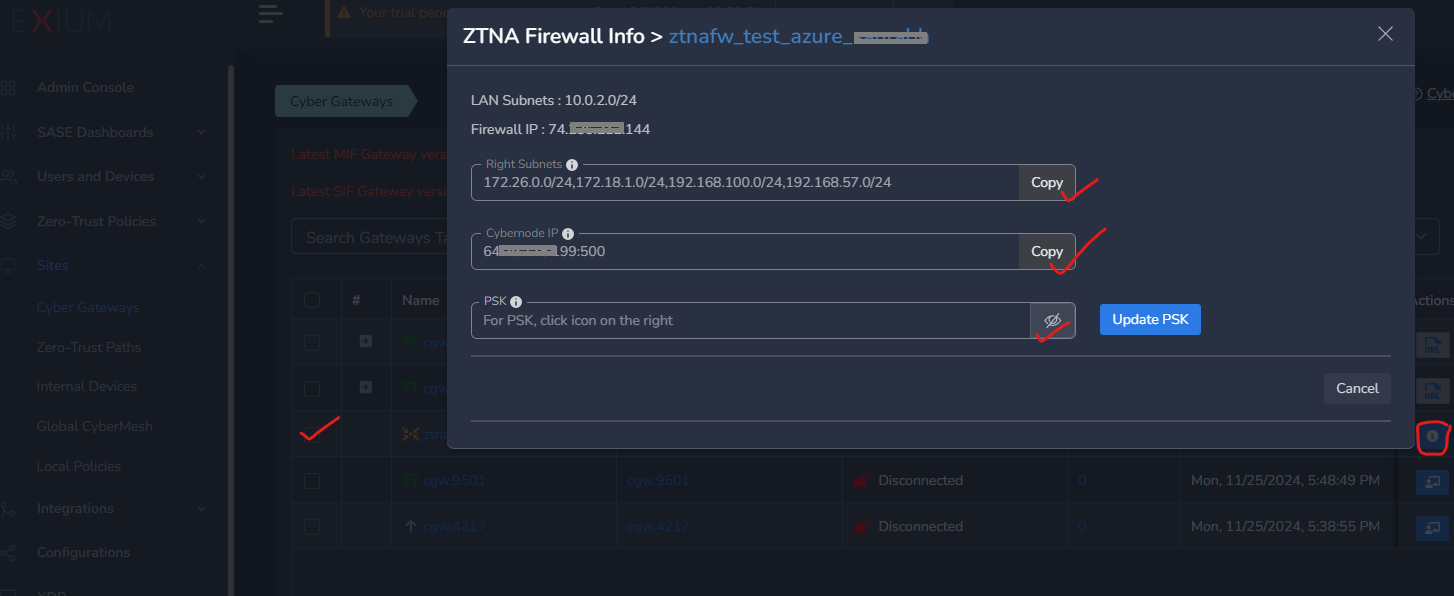
Copy following from the popover as shown in below screenshot
- Workspace Subnet: This is right subnet behind the firewall endpoint on Exium SASE Cloud. This will include the subnets which are selected in previous step. The devices which are part of this subnet will access resources behind your firewall using this subnet. You need to configure this on your firewall as right subnet.
- Cybernode IP: This is the firewall endpoint IP on Exium SASE Cloud. You need to configure this on your firewall.
- PSK: Pre share Key needs to be configured on your firewall to connect to exium SASE cloud firewall endpoint.
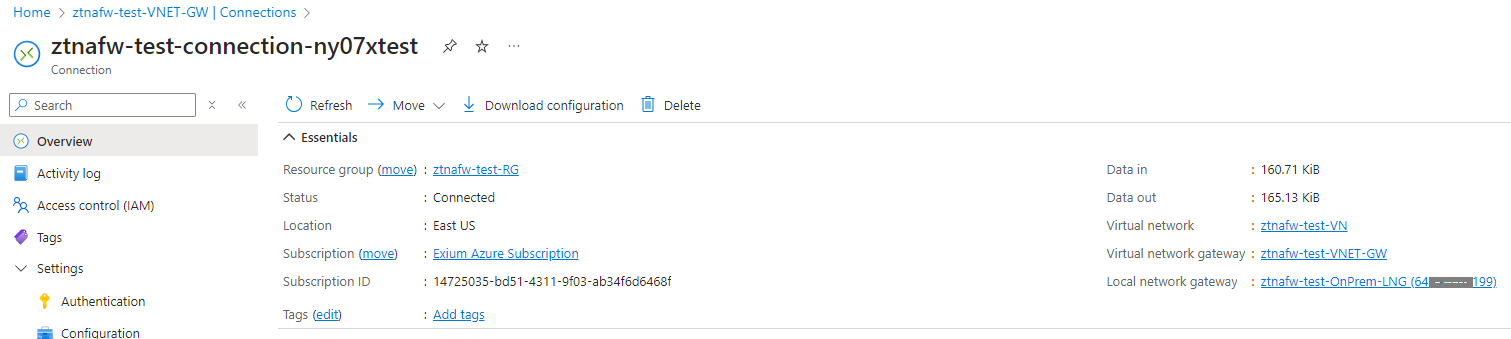
¶ Configure IPsec tunnel on Azure Cloud
Navigate to the Virtual Network Gateway and select your VNet gateway
Go to Connections under Settings and click on Add:
- Resource group: select your resource group
- Connection type: Site-to-Site (IPsec)
- Name: Provide name (ztnafw-test-connection-ny07xtest)
- Region: Same as previous
- Settings:
- Virtual Network Gateway: ztnafw-VNET-GW
- Authentication Method: Shared Key (PSK)
- IKE Protocol: IKEv2
- Use Azure Private IP Address: Disabled
- BGP: Disabled
- IPsec / IKE policy: Custom
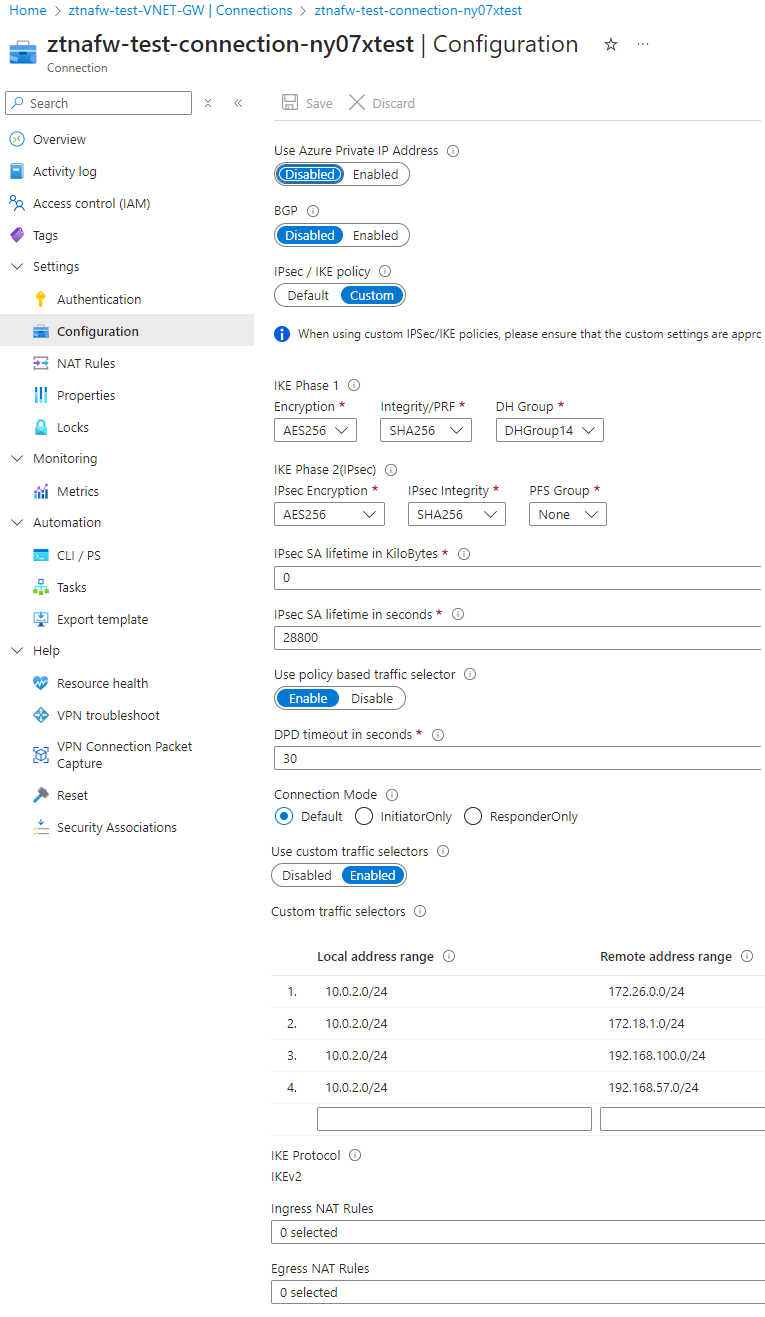
- IKE Phase 1:
- Encryption: AES256
- Integrity/PRF: SHA256
- DH Group: DHGroup14
- IKE Phase 2(IPsec):
- IPsec Encryption: AES256
- IPsec Integrity: SHA256
- PFS Group: None
- IPsec SA lifetime in KiloBytes: 0
- IPsec SA lifetime in seconds: 28800
- Use policy based traffic selector: Enable
- DPD timeout in seconds: 30
- Connection Mode: Default
- Use custom traffic selectors: Enabled
- Custom traffic selectors:
- Configure Local address range (Azure workload subnet) and Remote address range (On-prem workspace subnets/trust paths)
- Local address range 10.0.2.0/24 and Remote address range 172.26.0.0/24
- Local address range 10.0.2.0/24 and Remote address range 172.18.1.0/24
- Local address range 10.0.2.0/24 and Remote address range 192.168.57.0/24
- Local address range 10.0.2.0/24 and Remote address range 192.168.100.0/24
- Configure Local address range (Azure workload subnet) and Remote address range (On-prem workspace subnets/trust paths)
- Custom traffic selectors:
- IKE Phase 1:
- IKE Protocol: IKEv2
- Ingress NAT Rules: 0
- Egress NAT Rules: 0
- Save
Below is a sample configuration for your reference.
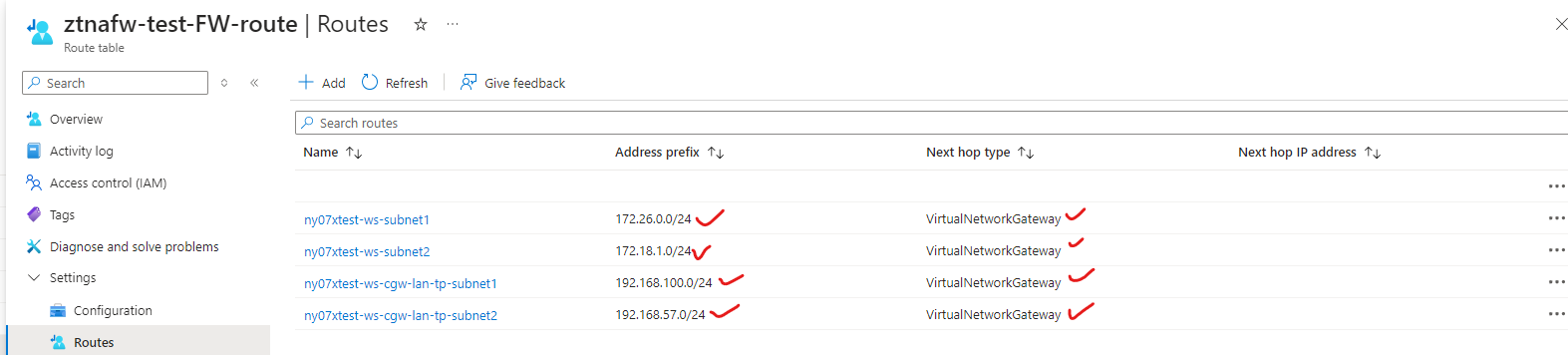
¶ Update Route Table on your Azure Cloud
Go to Azure portal > Route tables > Select your route table (ztnafw-test-FW-route)
Go to Settings > Routes
Add routes for all the On-prem subnets to go via Virtual Network Gateway:
For e.g:
- Route Name: ztnafw-test-FW-def-gw, Address prefix: 0.0.0.0/0, Next hop type: VirtualAppliance, Next hop IP address: 10.0.1.4 (Private IP of the Azure Firewall) - For only Inside out Access
- Route Name1: ws-subnet1, Address prefix: 172.26.0.0/0, Next hop type: VirtualNetworkgateway
- Route Name2: ws-subnet2, Address prefix: 172.18.1.0/0, Next hop type: VirtualNetworkgateway
- Route Name3: cgw-tp-subnet1, Address prefix: 192.168.57.0/0, Next hop type: VirtualNetworkgateway
- Route Name4: cgw-tp-subnet2, Address prefix: 192.168.100.0/0, Next hop type: VirtualNetworkgateway
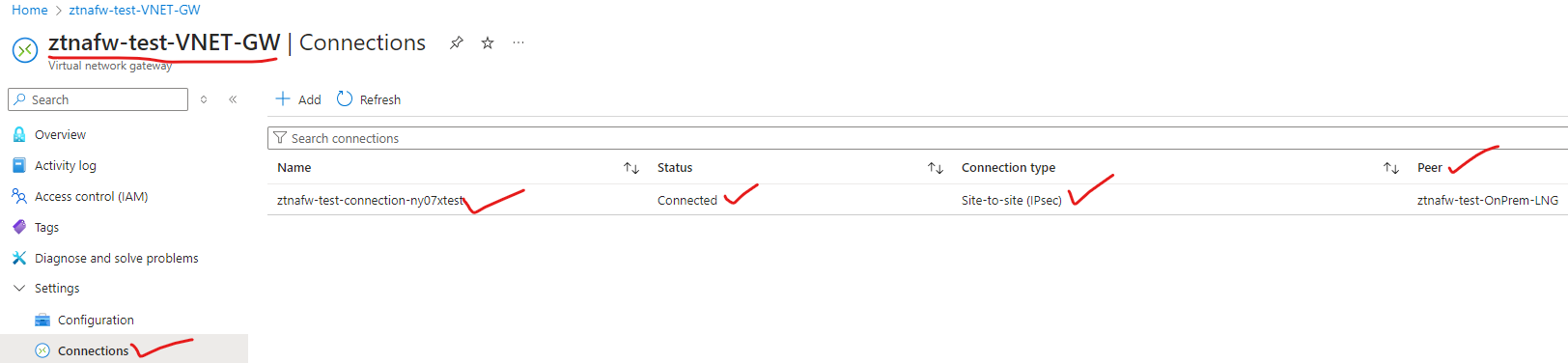
¶ Check Site-to-Site Connection Status
When connection is established between your Azure Cloud and Exium's SASE Cloud, status can be checked on Exium's admin console. Azure cloud UI will also show connection status (Go to your Virtual Network Gateway > Select your gateway > Connections)
¶ Bi-directional traffic verification
When Site-to-Site tunnel is up and shows connection on admin console. You can verify traffic flows both direction:
- If you already have Exium client installed on laptop, then connect the client and try accessing your Azure workloads / private resources
- In case you have allowed other trust paths in ZTNA firewall config, you can ping those resources from any of Azure workload.
Please refer Sample network diagram which shows multiple sites with CGW and Azure cloud connectivity with Exium's SASE cloud.
To learn more about implementing SASE, XDR, IAM, and GRC for your organization and explore tailored solutions that meet your unique requirements, contact Exium at partners@exium.net for a consultation or demonstration. If you are ready to get started, check out our testing and onboarding process.