¶ Challenge
Balancing robust security with optimal network performance can be a constant struggle. Traditional VPNs encrypt all traffic, potentially impacting performance for applications that don't require strict security measures. Additionally, full VPN tunnels can create obstacles when accessing local network resources like printers.
¶ Solution
Exium SASE introduces the powerful Traffic Steering Applications feature, also known as split tunneling. This functionality allows you to define which applications and traffic utilize the secure, encrypted VPN tunnel, while routing non-critical traffic directly over the internet.
¶ How it Works
Exium SASE leverages a multi-layered approach to facilitate split tunneling. You can define application rules based on:
- IP Addresses or Subnets: Designate specific IP addresses or subnets that require VPN protection.
- Application Identification: Exium SASE can identify specific applications and ensure they utilize the encrypted tunnel.
¶ Key Features and Benefits
|
No |
Key Features and Benefits of Traffic Steering Applications |
|---|---|
| 1 |
Selective Traffic Routing (e.g., Conditional Access)
|
| 2 |
Network Efficiency
|
| 3 |
Flexibility and Customization
|
| 4 |
Access to Local Network Devices
|
Exium SASE's Traffic Steering Applications feature represents a powerful solution for organizations seeking to balance network security with performance and flexibility. By selectively routing traffic through encrypted VPN tunnels, organizations can prioritize critical business applications while maintaining efficient access to non-business related resources. With enhanced security measures and granular control over traffic routing, Exium SASE enables organizations to optimize network efficiency and productivity without compromising on security.
¶ Configuring Traffic Steering Applications
Exium enables workspace admins with multiple options to configure Traffic Steering Applications. Traffic Steering Applications are defined in the central admin console and applied in the Exium Cloud CyberMesh platform as shown in the below architecture diagram.
You can define Traffic Steering Applications as Include or Exclude Lists as shown in the Table below. Also, you can define these applications either at workspace level or group level or user level.
|
Traffic Steering Applications |
Policy Definition |
Workspace level |
Group level |
User level |
|---|---|---|---|---|
|
Applies to all users in the workspace or in the organization |
Applies to all users in the group |
Applies to a particular user |
||
| Include List Support | Apps, IP addresses and subnets specified in the Include Lists go inside the tunnel |
√ |
√ |
√ |
| Exclude List Support | Apps, IP addresses and subnets specified in the Exclude Lists go outside the tunnel |
√ |
√ |
√ |
| Policies override precedence/ order | As per the order shown on the right |
Lowest |
Middle |
Highest |
¶ Override policies
Administrators can assign override policies with higher precedence. User-level policies take priority, followed by group-level policies, and workspace-level policies have the lowest precedence. For a deeper understanding of policy precedence, please refer to our article, “Customized Security Controls with Exium’s SASE Solution.”
¶ Traffic Steering Applications - Include List
You can define Traffic Steering Applications as include list, which will be included in tunnels of all users in the workspace. To create Traffic Steering Applications, follow the below steps
- Log into the partner admin console and navigate to the company workspace.
- Click on Zero-trust Policies in the left menu bar and Click on Traffic Steering
- Click on Add App as shown below

On Create Policy form, follow below steps
- Enter a Name for policy
- Select Include as Action
- Select Subnets as Type
- Enter Subnet as a subnet or IP address. Multiple entries can be added by pressing ENTER or SPACE after each entry.
- Finally click on Save as shown below
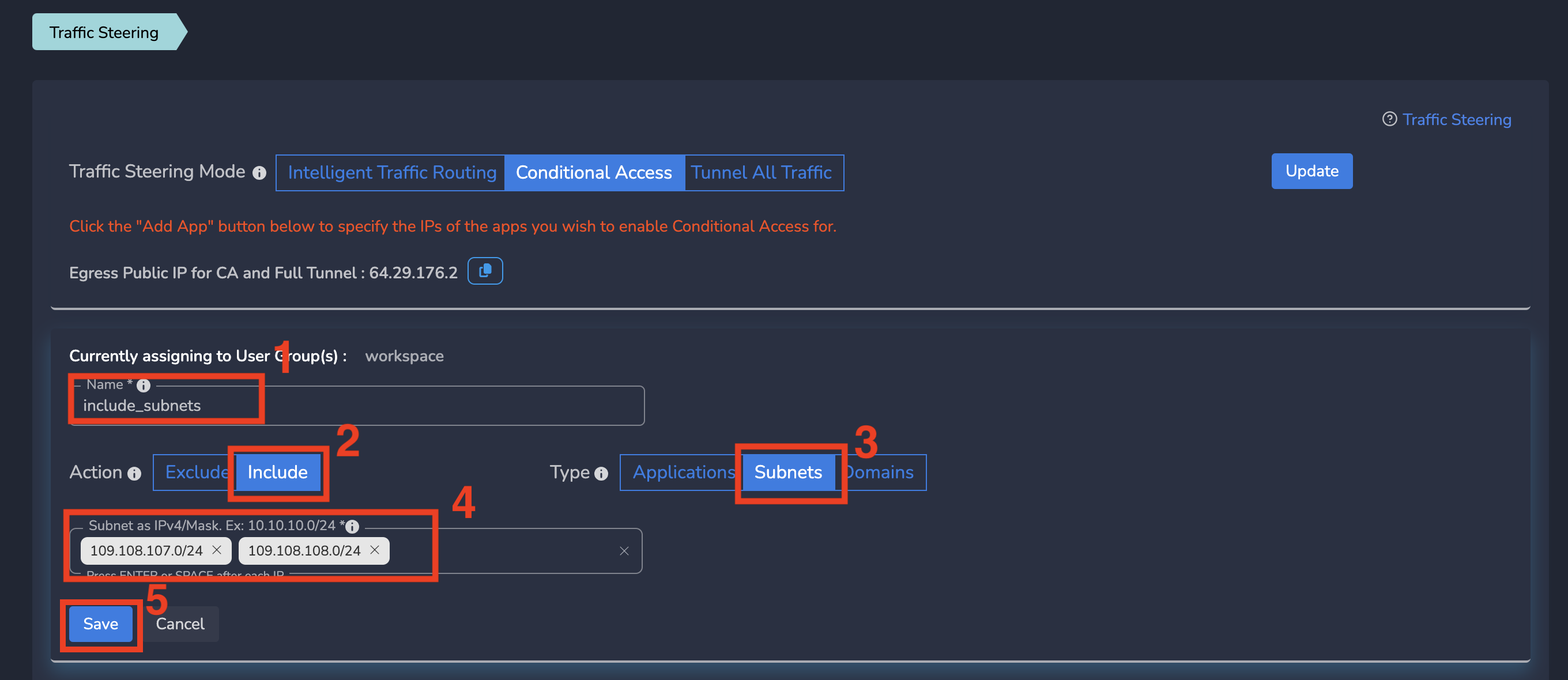
Traffic Steering Applications gets applied to all users in workspace. All users in workspace will be able to access the specific service on plain internet as defined in this policy.
¶ Traffic Steering Applications - Exclude List
You can define Traffic Steering Applications as exclude list, which will be excluded in tunnels of all users in the workspace. To create Traffic Steering Applications, follow the below steps
- Log into the partner admin console and navigate to the company workspace.
- Click on Zero-trust Policies in the left menu bar and Click on Traffic Steering
- Click on Add App as shown below

On Create Policy form, follow below steps
- Enter a Name for policy
- Select Exclude as Action
- Enter Subnets as Type
- Enter Subnet as a subnet or IP address. Multiple entries can be added by pressing ENTER or SPACE after each entry.
- Finally click on Save as shown below

Traffic Steering Applications gets applied to that user. User will be able to access the specific service on plain internet as defined in this policy.
¶ Configuring Traffic Steering Applications by User, Group, or Workspace
You have the flexibility to define traffic steering applications at various levels, whether it be at the workspace, group, or individual user level. The following sections detail the steps to configure traffic steering applications for each of these levels, ensuring precise control and optimized performance.
¶ Implementing Workspace-Level Traffic Steering Applications
To ensure consistent application of traffic steering rules across all users, you can set these policies at the workspace level. Follow the steps below to create and apply workspace-wide traffic steering applications:
- Log into the partner admin console and navigate to the company workspace.
- In the left menu bar, click on "Zero-trust Policies" and then select "Traffic Steering."
- From the drop-down menu, choose "workspace" and click on "Add App."

On the Create Policy form, proceed with the following steps:
- Enter a name for the policy.
- Select "Include" as the action.
- Choose "Subnets" as the type.
- Enter the subnet or IP address. Multiple entries can be added by pressing ENTER or SPACE after each entry.
- Click on "Save."
Traffic steering applications will be applied to all users within the workspace, ensuring they can access the specified services as defined by this policy.

¶ Group-Level Traffic Steering Applications
To apply traffic steering applications to all users within a specific group, follow these steps to create group-level policies:
- Log into the partner admin console and navigate to the company workspace.
- In the left menu bar, click on "Zero-trust Policies" and then select "Traffic Steering."
- From the drop-down menu, choose "group" and click on "Add App."

On the Create Policy form, follow these steps:
- Enter a name for the policy.
- Select "Include" as the action.
- Choose "Subnets" as the type.
- Enter the subnet or IP address. Multiple entries can be added by pressing ENTER or SPACE after each entry.
- Click on "Save."
Once submitted, traffic steering applications are immediately applied to all users within the group, enabling them to access the specified services as defined by this policy.

¶ User-Level Traffic Steering Applications
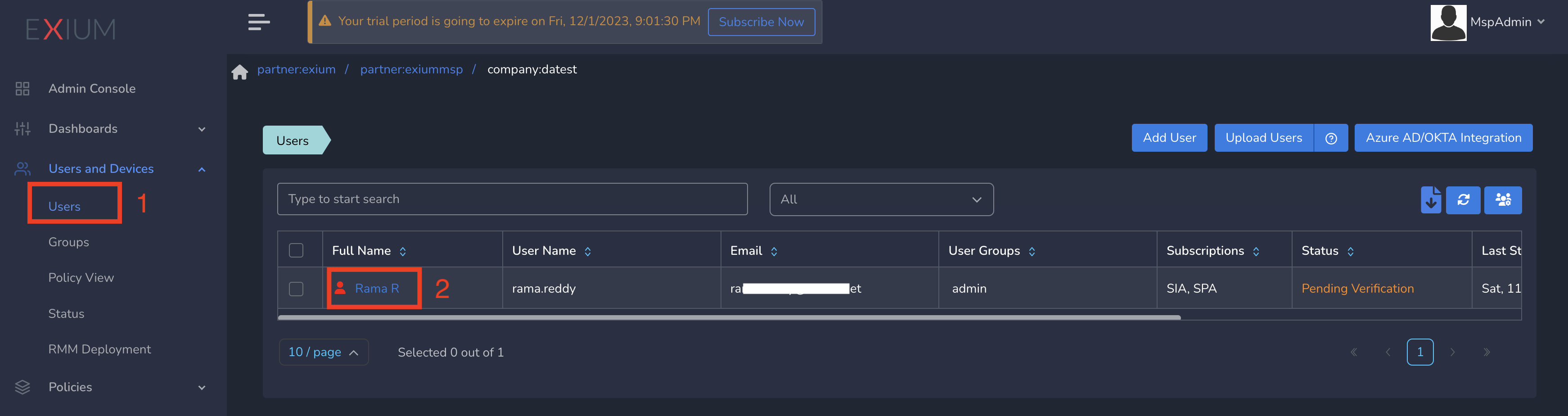
You can set up traffic steering applications specifically at the user level, ensuring tailored access for individual users. To assign a traffic steering policy to a user, follow these steps:
- Click on "Users and Devices" in the left menu bar, then select "Users."
- Choose the user by clicking on their username.
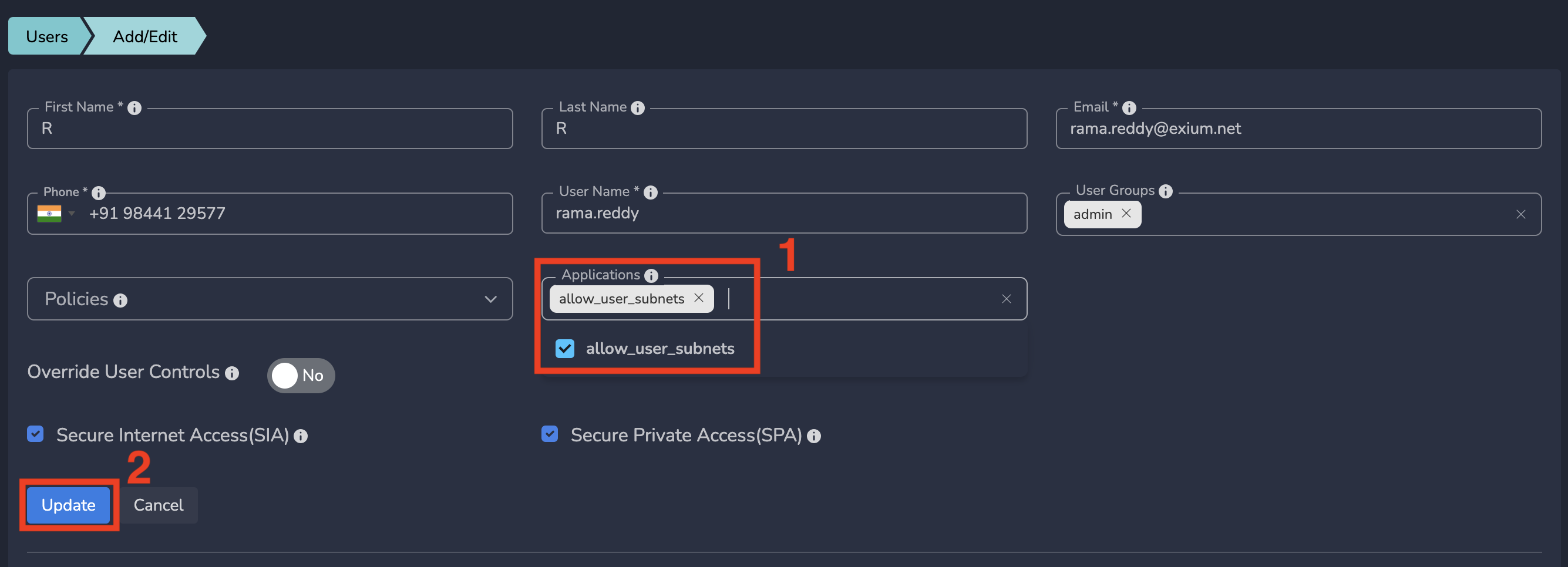
- From the "Applications" dropdown menu, select the traffic steering application, and then click "Update."
Once submitted, the traffic steering application is immediately applied to the user, allowing them to access the specific services defined in this policy.
¶ Understanding Traffic Steering Applications: Types of Application Definitions
When creating traffic steering applications within Exium, you have the option to define them as "Exclude" or "Include," with several methods for application creation. The following table summarizes each type:
|
No |
Types of Traffic Steering Applications |
|---|---|
| 1 |
Applications:
|
| 2 |
Subnets:
|
| 3 |
Domains:
|
¶ Traffic Steering Applications - Applications based
On Create Policy form, follow below steps
- Enter a Name for policy
- Select Include as Action
- Enter Applications as Type
- Select pre defined applications from dropdown. Multiple entries can be added by pressing ENTER or SPACE after each entry.
- Finally click on Save as shown below

¶ Traffic Steering Applications - Subnets based
On Create Policy form, follow below steps
- Enter a Name for policy
- Select Include as Action
- Select Subnets as Type
- Enter Subnet as a subnet or IP address. Multiple entries can be added by pressing ENTER or SPACE after each entry.
- Finally click on Save as shown below

¶ Traffic Steering Applications - Domains based
On Create Policy form, follow below steps
- Enter a Name for policy
- Select Include as Action
- Select Domains as Type
- Enter domain in Domains field. Multiple entries can be added by pressing ENTER or SPACE after each entry.
- Finally click on Save as shown below

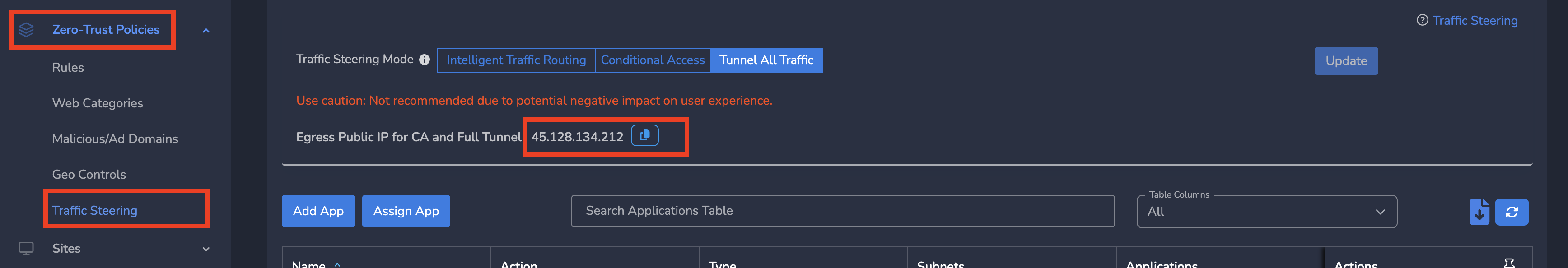
¶ Traffic Steering Applications - Public IP for CA
When traffic steering mode is set to conditional access or tunnel all traffic, the page displays internet facing public IP. For some applications like M365, this public IP needs to be whitelisted.
- Log into the partner admin console and navigate to the company workspace.
- Click on Zero-trust Policies in the left menu bar and Click on Traffic Steering
- Click on Copy button next to public ip as shown below
To learn more about implementing SASE for your organization and explore tailored solutions that meet your unique requirements, contact Exium at partners@exium.net for a consultation or demonstration. If you are ready to get started, check out our testing and onboarding process.