¶ Time-Bound Zero Trust Security Policies
In an era of evolving cyber threats and regulatory requirements, organizations face the critical challenge of securing their networks while ensuring compliance with stringent regulations. Exium's Secure Access Service Edge (SASE) platform introduces a revolutionary approach to cybersecurity, combining the principles of Zero Trust with time-bound security policies. This innovative feature not only enhances organizational compliance but also provides robust protection against cyber threats.
¶ Challenges
|
Regulatory Compliance |
Dynamic Cyber Threat Landscape |
|---|---|
| Organizations must adhere to industry-specific regulations, requiring stringent control over data access and security measures. | Cyber threats are continuously evolving, demanding adaptive security measures to safeguard against sophisticated attacks. |
¶ Exium SASE Solution Highlights
|
No |
Key Components of Exium SASE Solution |
|---|---|
| 1 |
Zero Trust Principles:
|
| 2 |
Time-Bound Security Policies:
|
| 3 |
Compliance Assurance:
|
| 4 |
Adaptive Security Posture:
|
| 5 |
User-Centric Controls:
|
¶ Benefits for Organizations
- Regulatory Compliance: Align security practices with regulatory mandates, fostering a compliance-driven security culture.
- Dynamic Threat Mitigation: Respond proactively to evolving cyber threats by adjusting security policies based on real-time threat intelligence.
- Reduced Attack Surface: Time-bound access restrictions limit exposure to potential threats, enhancing overall cybersecurity resilience.
- Operational Efficiency: Tailor security policies to user roles, optimizing access controls without compromising productivity.
¶ Configuring Time-Bound Security Policies
Exium enables workspace admins with multiple options to configure Time-Bound Security Policies. Time-Bound Security Policies are defined in the central admin console and applied in the Exium Cloud CyberMesh platform as shown in the below architecture diagram.
You can define Time-Bound Security Policies at workspace level, group level or user level as shown in the Table below:
|
Time-Bound Security Policies |
Workspace level |
Group level |
User level |
|---|---|---|---|
| Policy Definition | Applies to all users in the workspace or in the organization | Applies to all users in the group | Applies to a particular user |
| Limited Access to specific services in a network (Non-Recurring Time-Bound) |
√ |
√ |
√ |
| Limited Access to specific services in a network (Recurring Time-Bound) |
√ |
√ |
√ |
| Policies override precedence/ order |
Lowest |
Middle |
Highest |
¶ Non-Recurring Time-Bound Security Policies
¶ Workspace level Time-Bound Security Policies (Non-Recurring)
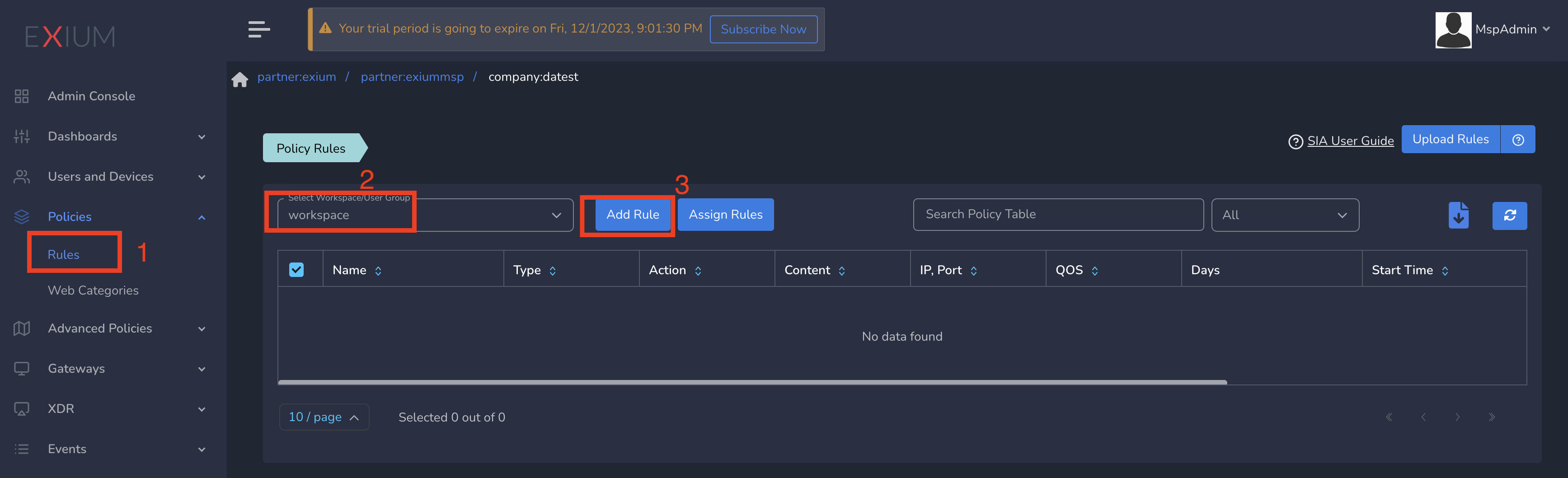
You can define limited ZTNA policies at workspace level which will be applied to all users in the workspace. To create ZTNA policies, follow the below steps
- Navigate to the Service Portal admin console
- Click on Zero-trust Policies in the left menu bar and Click on Rules
- Select workspace from drop down and click on Add Rule as shown below
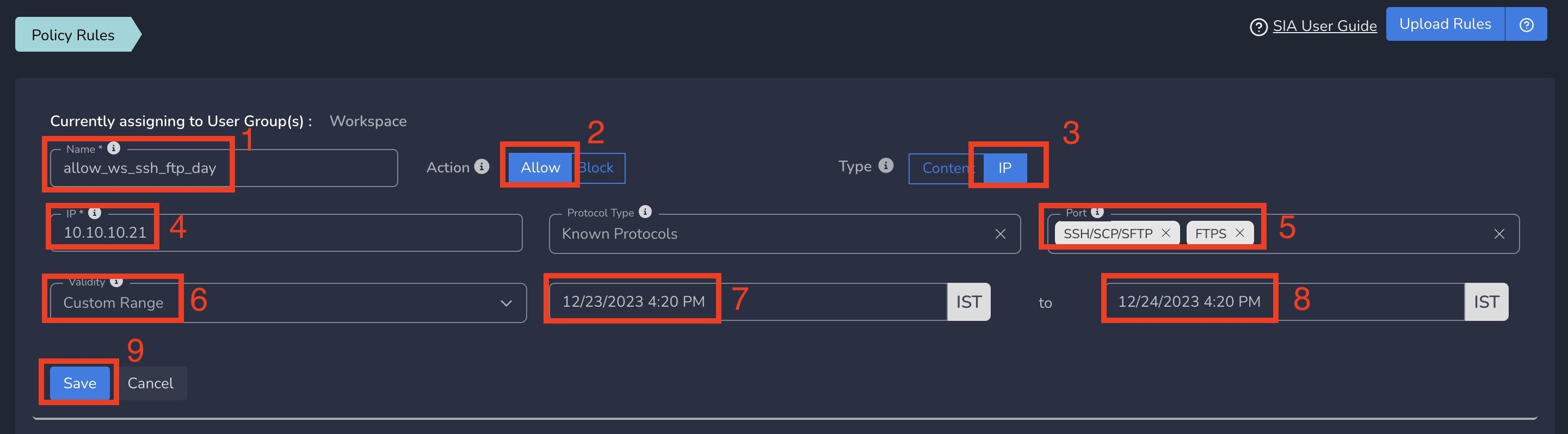
On Create Policy form, follow below steps
- Enter a name for policy
- Select Action as Allow. By default, Block is selected.
- Select Type as IP.
- Enter the Subnet or specific IP as IP. Optionally you can select Protocol and Port(s) to give access only to specific service within that IP and Port.
- Select Validity as Next 1 Hour or 1 Day or 1 Week or 1 Month or 1 Year. You can also define a Custom Start Date/Time to End Date/Time.
- Finally click on Save as shown below
Limited ZTNA policies gets applied to all users in workspace immediately after submit based on the start date/time. All users in workspace will be able to access the specific service defined in this policy. The policy will become inactive automatically after end date/time.
¶ Group level Time-Bound Security Policies (Non-Recurring)
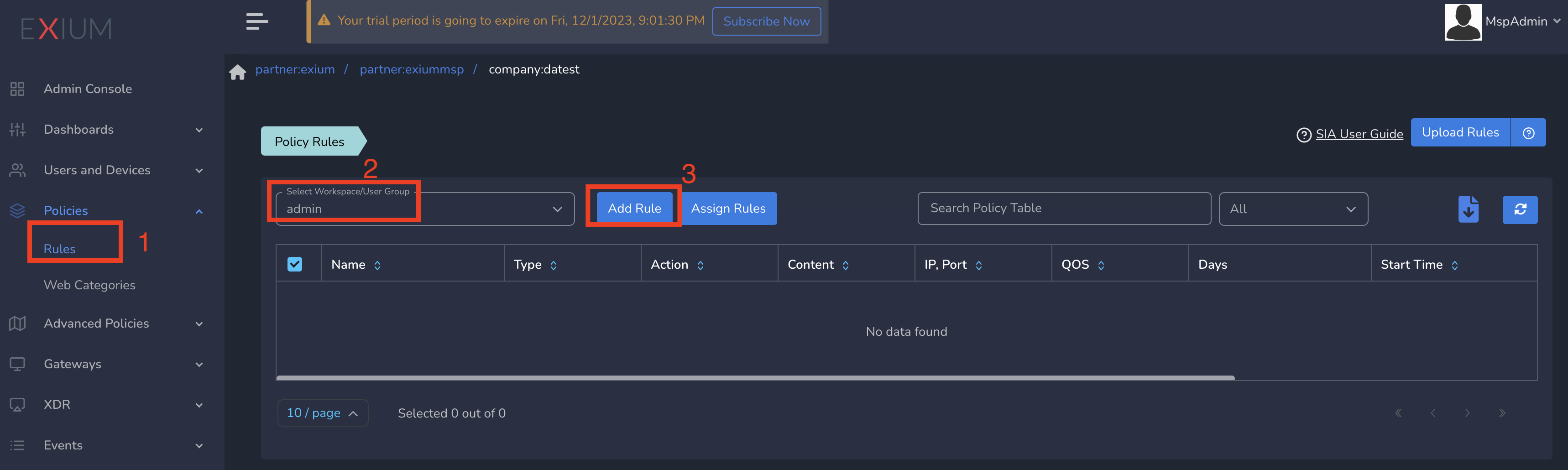
You can define limited ZTNA policies at group level which will be applied to all users in that group. To create ZTNA policies, Follow below steps
- Navigate to the Service Portal admin console
- Click on Policies in the left menu bar and Click on Rules
- Select group from drop down and click on Add Rule as shown below
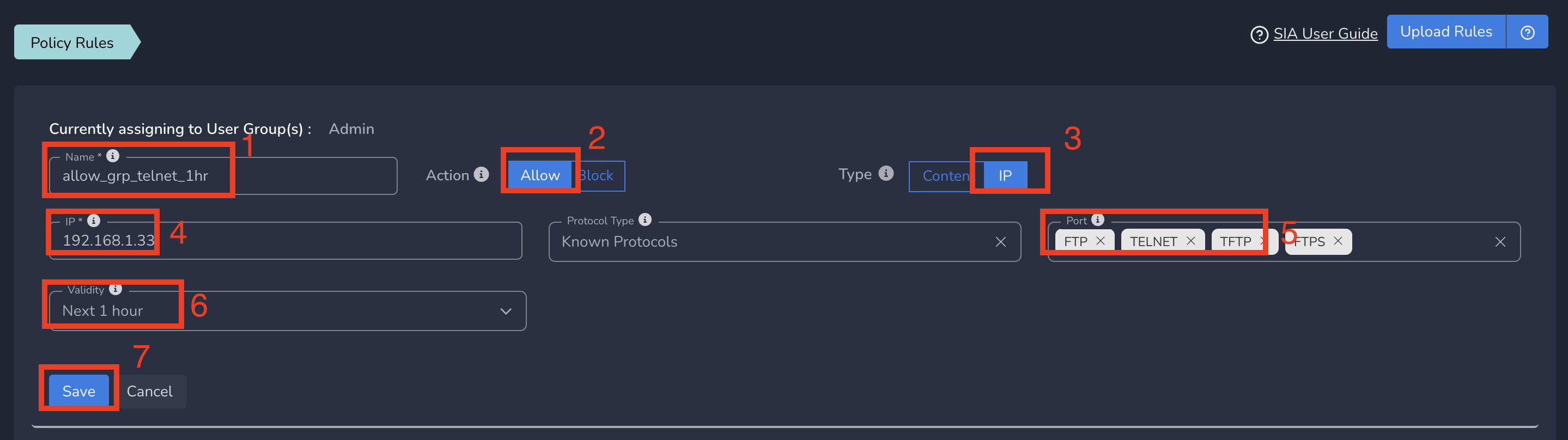
On Create Policy form, follow the below steps
- Enter a name for policy
- Select Action as Allow. By default, Block is selected.
- Select Type as IP.
- Enter the Subnet or specific IP as IP. Optionally you can select Protocol and Port(s) to give access only to specific service within that IP and Port.
- Select Validity as Next 1 Hour or 1 Day or 1 Week or 1 Month or 1 Year. You can also define a Custom Start Date/Time to End Date/Time.
- Finally click on Save as shown below
Limited ZTNA policies gets applied to all users in group immediately after submit based on the start date/time. All users in that group will be able to access the specific service defined in this policy. The policy will become inactive automatically after end date/time.
¶ User level Time-Bound Security Policies (Non-Recurring)
You can define ZTNA policies at user level which will be applied to all users in that group. To create ZTNA policies, Follow below steps
You can define the policy as shown in the previous steps. You need to select All Rules in policies table before creating the policy
To Assign the policy to User, follow below steps
- Click on Users and Devices in the left menu bar and Click on Users
- Select the user and click on username as shown below
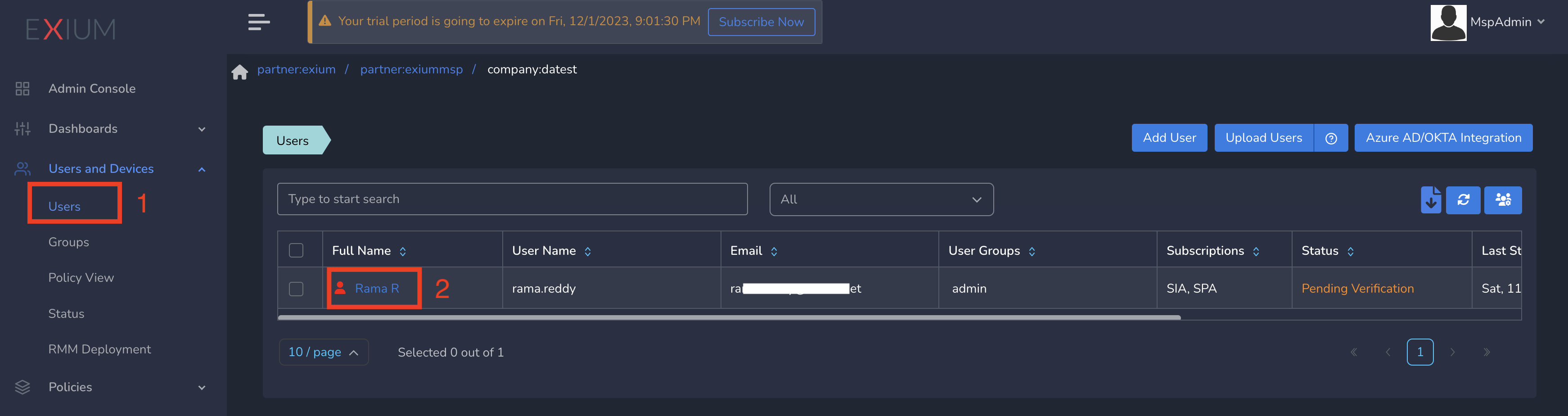
- Select Policy from drop down and Update as shown below
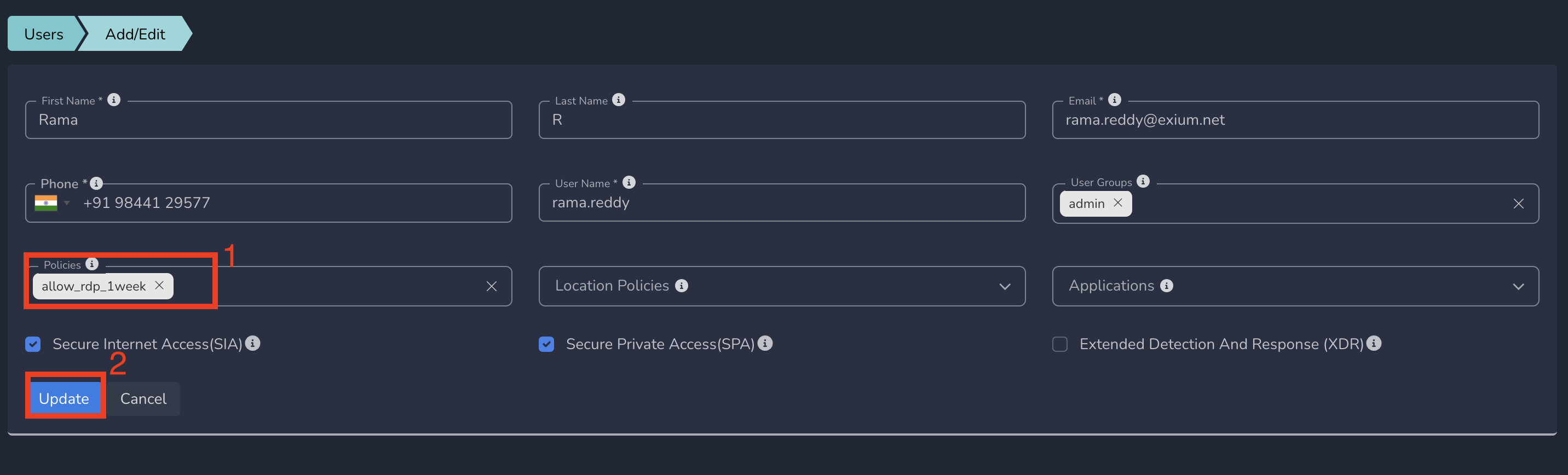
Limited ZTNA policies gets applied to the user immediately after submit based on the start date/time. User will be able to access the specific service defined in this policy. The policy will become inactive automatically after end date/time.
¶ Recurring Time-Bound Security Policies
¶ Workspace level Time-Bound Security Policies (Recurring)
You can define limited ZTNA policies at workspace level which will be applied to all users in the workspace. To create ZTNA policies, follow the below steps
- Navigate to the Service Portal admin console
- Click on Zero-trust Policies in the left menu bar and Click on Rules
- Select workspace from drop down and click on Add Rule as shown below

On Create Policy form, follow below steps
- Enter a name for policy
- Select Action as Allow. By default, Block is selected.
- Select Type as IP.
- Enter the Subnet or specific IP as IP. Optionally you can select Protocol and Port(s) to give access only to specific service within that IP and Port.
- Select Validity as Repetitive. Select Start Time to End Time. Select Days on which you want the policy to be repeated.
- Finally click on Save as shown below
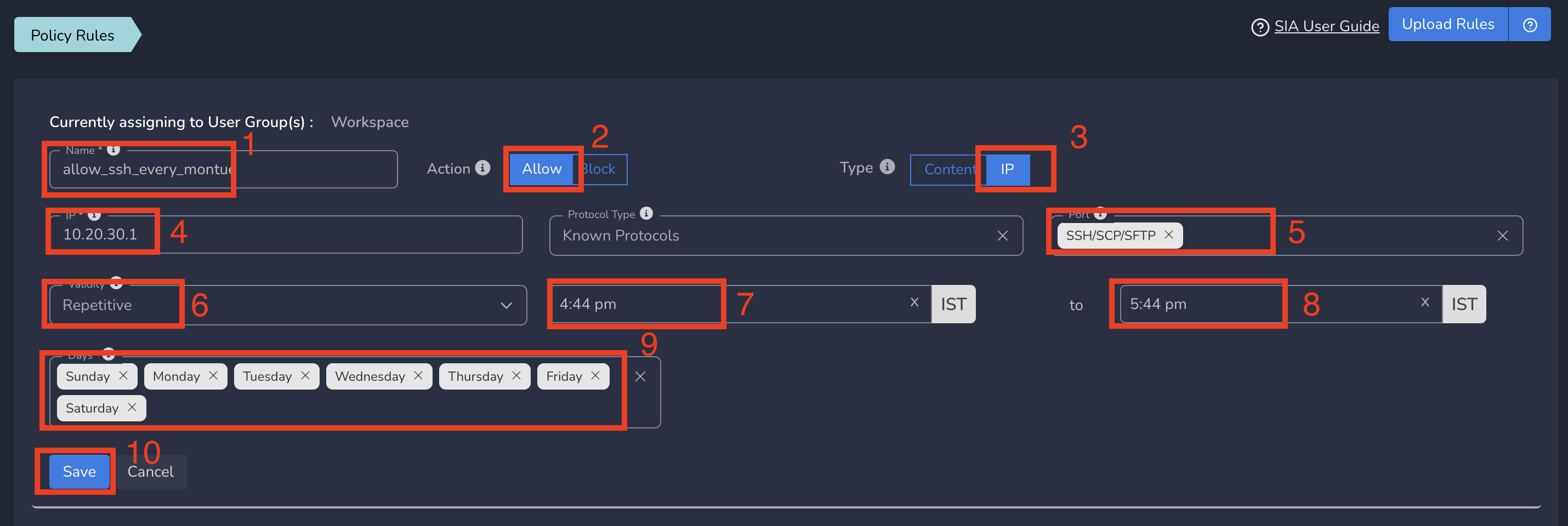
Limited ZTNA policies gets applied to all users in workspace immediately after submit based on the day and start time. All users in workspace will be able to access the specific service defined in this policy. The policy will become inactive automatically after end time of the day and gets repeated based on the next day and time.
¶ Group level Time-Bound Security Policies (Recurring)
You can define limited ZTNA policies at group level which will be applied to all users in that group. To create ZTNA policies, Follow below steps
- Navigate to the Service Portal admin console
- Click on Policies in the left menu bar and Click on Rules
- Select group from drop down and click on Add Rule as shown below

On Create Policy form, follow the below steps
- Enter a name for policy
- Select Action as Allow. By default, Block is selected.
- Select Type as IP.
- Enter the Subnet or specific IP as IP. Optionally you can select Protocol and Port(s) to give access only to specific service within that IP and Port.
- Select Validity as Repetitive. Select Start Time to End Time. Select Days on which you want the policy to be repeated.
- Finally click on Save as shown below
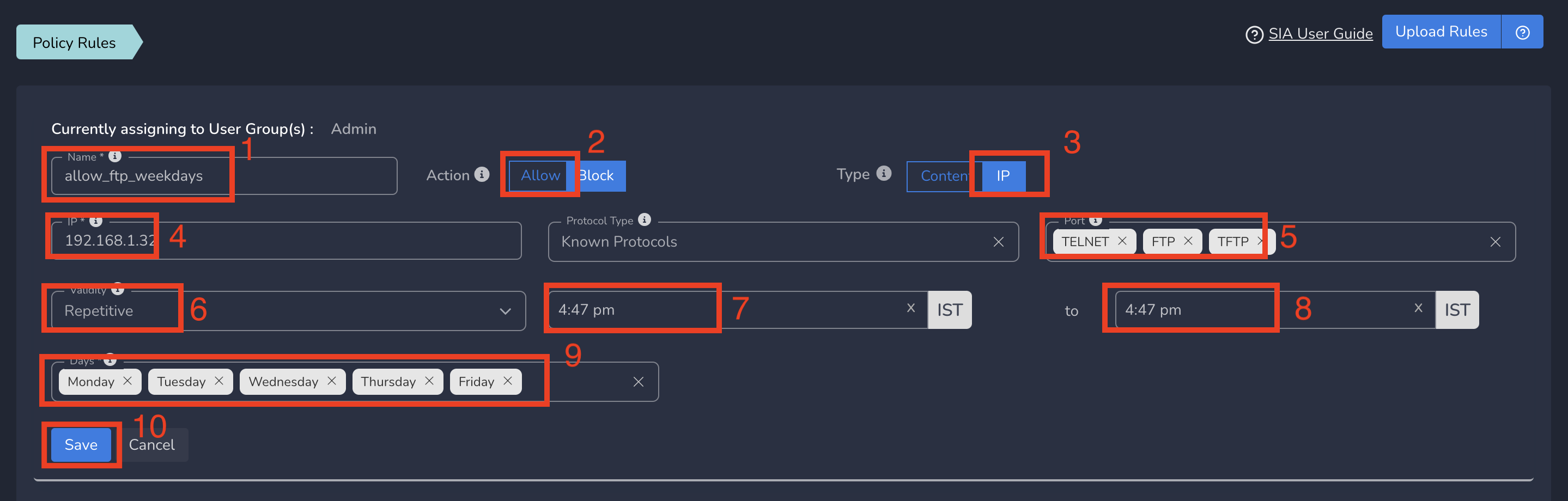
Limited ZTNA policies gets applied to all users in group immediately after submit based on the day and start time. All users in group will be able to access the specific service defined in this policy. The policy will become inactive automatically after end time of the day and gets repeated based on the next day and time.
¶ User level Time-Bound Security Policies (Recurring)
You can define ZTNA policies at user level which will be applied to all users in that group. To create ZTNA policies, Follow below steps
You can define the policy as shown in the previous steps. You need to select All Rules in policies table before creating the policy
To Assign the policy to User, follow below steps
- Click on Users and Devices in the left menu bar and Click on Users
- Select the user and click on username as shown below

- Select Policy from drop down and Update as shown below
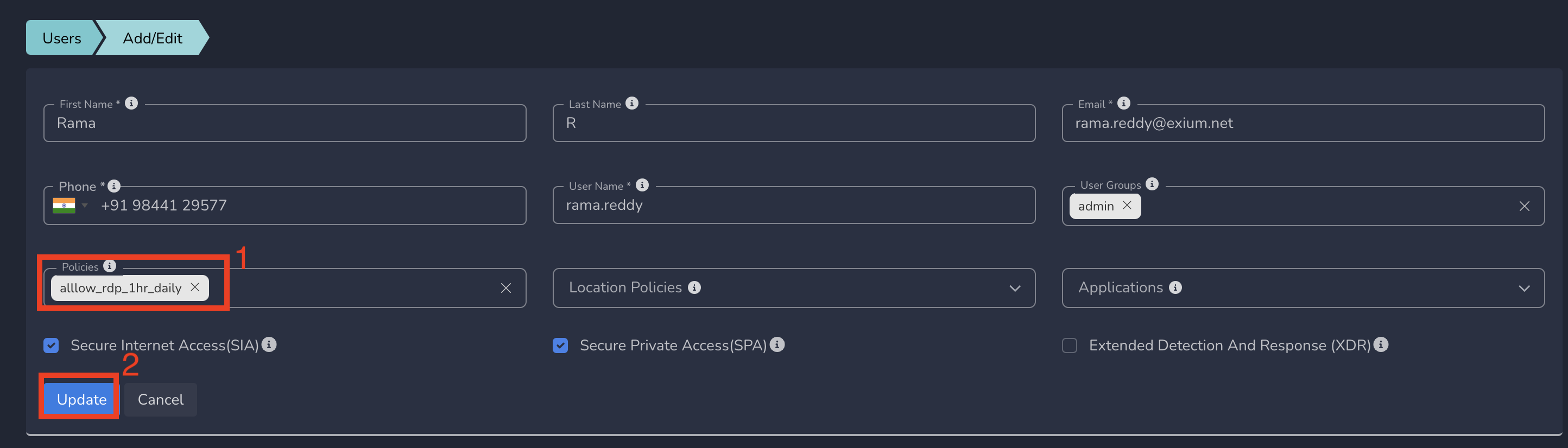
Limited ZTNA policies gets applied to the user immediately after submit based on the day and start time. User will be able to access the specific service defined in this policy. The policy will become inactive automatically after end time of the day and gets repeated based on the next day and time.
¶ Conclusion
Exium SASE's integration of time-bound Zero Trust security policies represents a significant leap forward in cybersecurity. By combining Zero Trust principles with time-sensitive access controls, organizations can achieve regulatory compliance, proactively mitigate cyber threats, and foster an adaptive and resilient security posture. Embrace the future of cybersecurity with Exium SASE.
To learn more about implementing SASE for your organization and explore tailored solutions that meet your unique requirements, contact Exium at partners@exium.net for a consultation or demonstration. If you are ready to get started, check out our testing and onboarding process.