¶ Overview
Geolocation IP policies are a crucial component of modern cybersecurity strategies, providing organizations with the means to enhance their network security, compliance, and user experience. By leveraging geolocation data associated with IP addresses, businesses can implement targeted policies to control access, mitigate security threats, and ensure regulatory compliance.
¶ Key Features
| Granular Access Control | Geolocation IP policies enable organizations to define access permissions based on the geographic location of users or devices. This granular control enhances security by restricting access to sensitive data or systems based on the user's physical location. |
| Threat Mitigation | Identify and block potentially malicious activities originating from specific regions or countries. Geolocation IP policies provide a proactive approach to cybersecurity, allowing organizations to preemptively block traffic from high-risk areas and reduce the likelihood of cyber attacks. |
| Compliance Management | Address regulatory requirements by tailoring access controls to adhere to specific regional or industry-based compliance standards. Geolocation IP policies assist in ensuring data sovereignty and meeting legal obligations associated with data protection and privacy regulations. |
| Dynamic Policy Adjustments | Adapt to changing threat landscapes and business requirements by dynamically adjusting geolocation IP policies. Automated systems can continuously monitor and analyze IP traffic, allowing organizations to respond quickly to emerging threats or regulatory changes. |
| Multi-Layered Security | Geolocation IP policies complement existing security measures, forming part of a multi-layered security approach. By combining geolocation filtering with other security tools, organizations can create a robust defense mechanism against a wide range of cyber threats. |
¶ Configure and Apply Geolocation IP Policies
Geolocation IP policies are a powerful tool for organizations seeking to strengthen their cybersecurity posture, achieve regulatory compliance, and optimize the user experience. By intelligently leveraging geolocation data, businesses can implement targeted and dynamic access controls, contributing to a comprehensive and adaptive security strategy.
Exium enables workspace admins with multiple options to configure Geolocation IP policies. Geolocation IP policies are defined in the central admin console and applied in the Exium Cloud CyberMesh platform as shown in the above architecture diagram. Admins can define Geolocation IP policies to ALLOW/BLOCK some of the countries. Admins can also define default BLOCK from all locations and add ALLOW policy from specific countries. Exium enables workspace admins with multiple options to configure Geolocation IP policies.
|
Geolocation IP Policies |
Workspace level |
Group level |
User level |
|---|---|---|---|
| Policy Definition | Applies to all users in the workspace or in the organization | Applies to all users in the group | Applies to a particular user |
| Geolocation IP Policies Granularity |
√ |
√ |
√ |
| Policies override precedence/ order |
Lowest |
Middle |
Highest |
- Admins can define Geolocation IP policies and at workspace level which will be applied to all users in the workspace.
- Admins can define Geolocation IP policies at group level which will be applied to all users in that group.
- Admins can define Geolocation IP policies and at a user level which will be applied to that particular user.
¶ Override policies
Admins can attach override policies at higher precedence. User level policies are at the highest precedence, followed by the group level policies and finally workspace level policies are at the lowest precedence.
¶ Create Geolocation IP Policies
Exium enables workspace admins with multiple options to configure Geolocation IP policies. Policies can be defined at Workspace, User group or User level.
¶ Workspace level Geolocation IP Policies
You can define Geolocation IP policies at workspace level which will be applied to all users in the workspace (organization). To create Geolocation IP policies, Follow below steps
- Navigate to the Service Portal admin console
- Click on Advanced Policies in the left menu bar and Click on Location Policy
- Select Workspace from drop down and click on Add Location as shown below
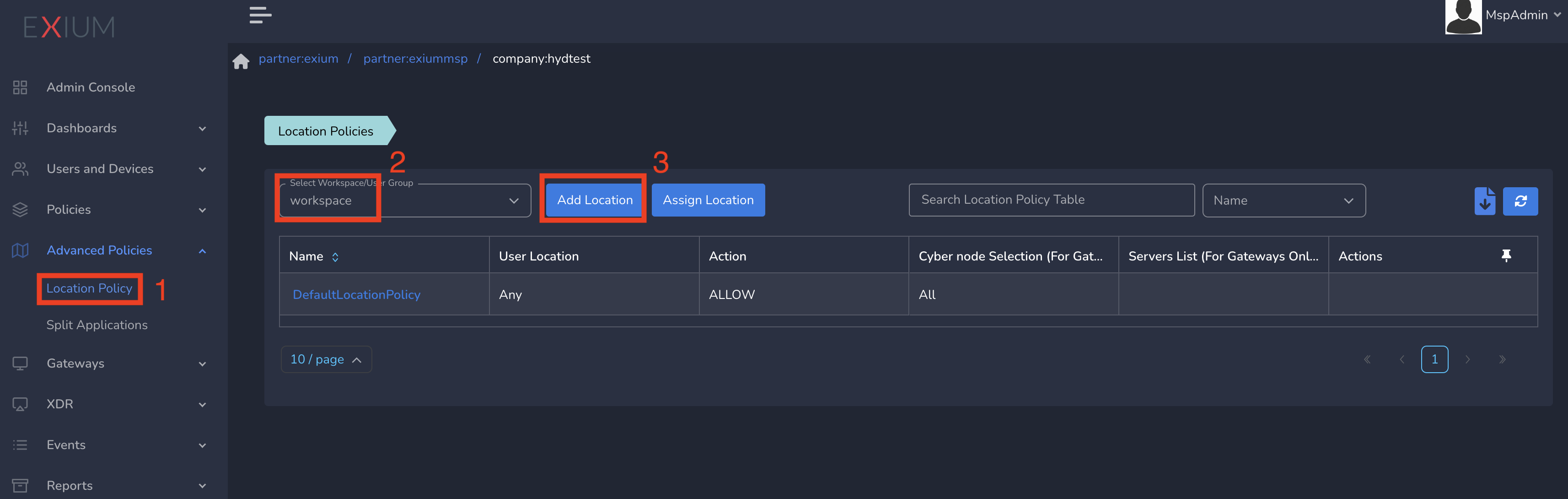
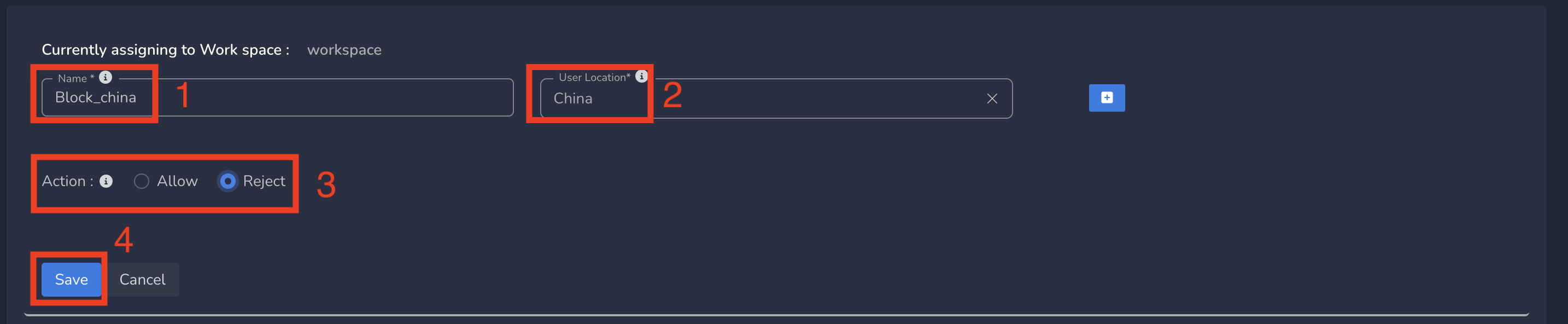
On Create Location Policy form, follow below steps
- Enter a Name for the policy
- Select User Location from drop down (based on requirement). Any applies to all locations and countries.
- Select Action as Allow/Reject (based on requirement). By default, Allow is selected.
- Finally click on Save as shown below.
Geo Location IP policies gets applied to all users in workspace immediately after submitting.
¶ Group level Geolocation IP Policies
You can define Geolocation IP policies at group level which will be applied to all users in that group. To create Geolocation IP policies, Follow below steps
- Navigate to the Service Portal admin console
- Click on Advanced Policies in the left menu bar and Click on Location Policy
- Select a group from drop down and click on Add Location as shown below
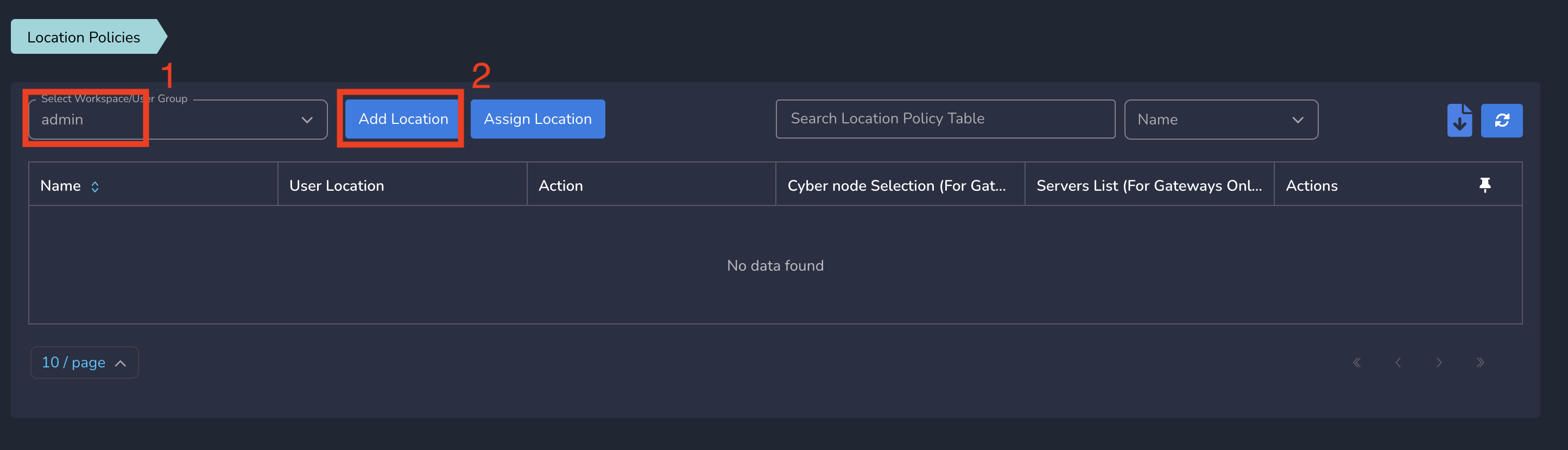
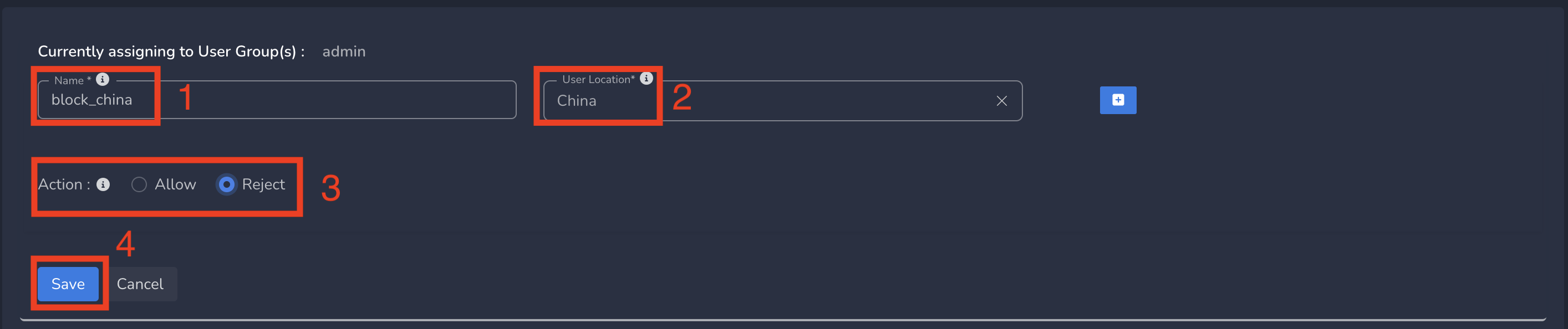
On Create Location Policy form, follow below steps
- Enter a Name for policy
- Select User Location from drop down (based on requirement). Any applies to all locations and countries.
- Select Action as Allow/Reject (based on requirement). By default, Allow is selected.
- Finally click on Save as shown below.
Geolocation IP policies gets applied to all users in the group immediately after submitting.
¶ User level Geolocation IP Policies
You can define Geolocation IP policies at user level which will be applied to that user. To assign Geolocation IP policies to user, Follow below steps
You can define the policy as shown in above step. You can select All Locations in policies table before creating the policy.
To Assign the policy to User, follow below steps
- Click on Users and Devices in the left menu bar and Click on Users
- Select the user and click on username as shown below
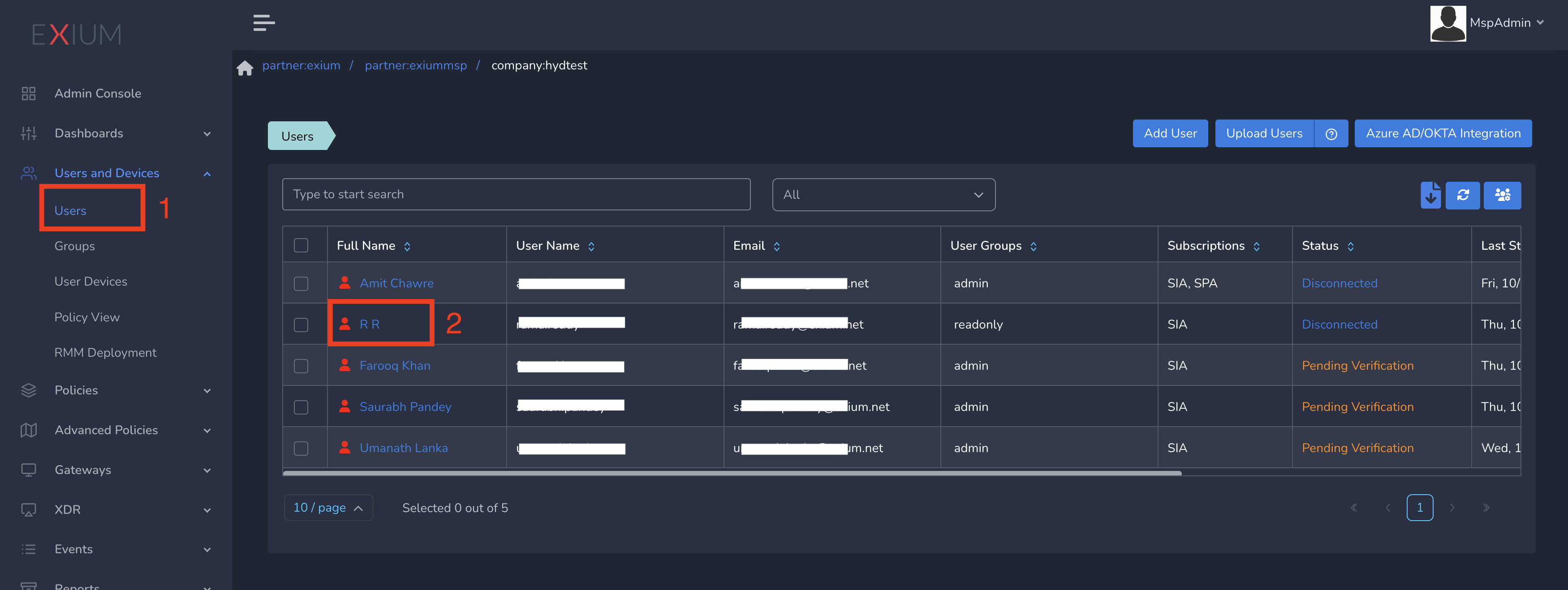
- Select Location Policy from drop down and click on Update as shown below
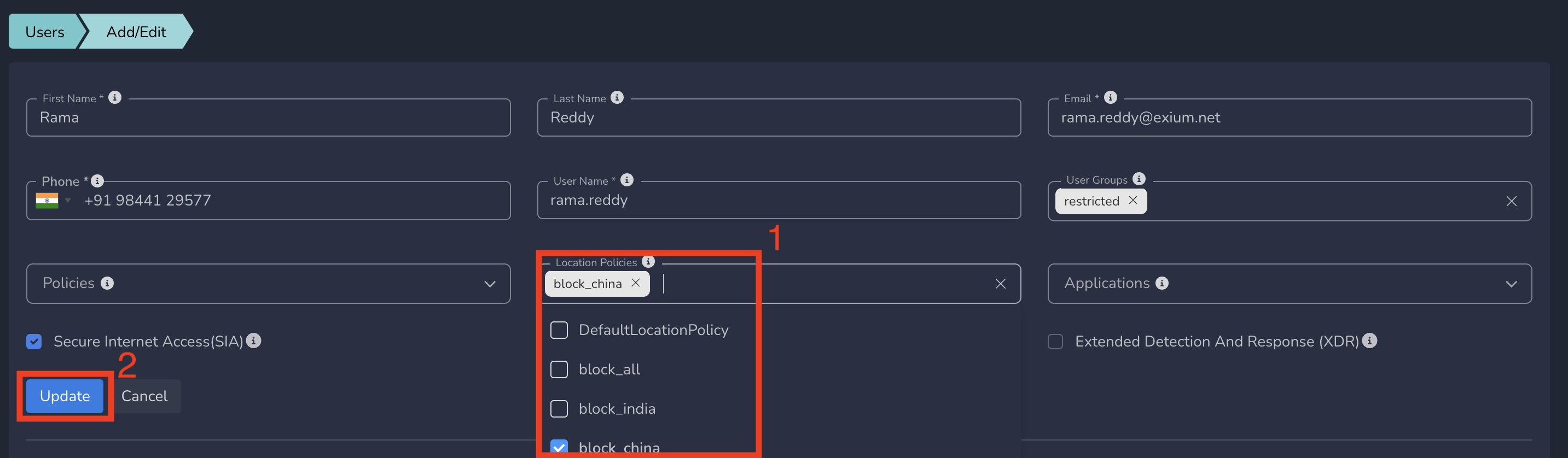
Geolocation IP policies gets applied to that user immediately after submitting.
¶ Override Policies and Policy Precedence View
When a user belongs to multiple groups and if the same country is defined in multiple policies attached to multiple groups or workspace, the country rule part of a group which has highest level of precedence will be applied.
We provide some examples below to clarify this. For all the examples, userA is assumed to be a part of a group groupA.
|
Example |
Workspace |
Group |
User |
Policy in Play |
|---|---|---|---|---|
| 1 | Blocked | Allowed | NA | If China is Blocked at workspace level and if China is Allowed at groupA level, for all users part of the groupA (including userA), can access when they connect to Exium from China. For the users not in groupA, connection to Exium from China will be blocked. |
| 2 | Blocked | NA | Allowed | If China is Blocked at workspace level and if China is Allowed at userA level, only userA can connect to Exium from China. For all other users, connection to Exium from China will be blocked. |
| 3 | Blocked | Allowed | Blocked | If China is Blocked at workspace level, and if China is Allowed at groupA level and China is blocked at userA level. For userA connection to Exium from China will be blocked, while for all other users part of groupA (excluding userA), connection to Exium from China will be allowed. For the users not in groupA, connection to Exium from China will be blocked. |
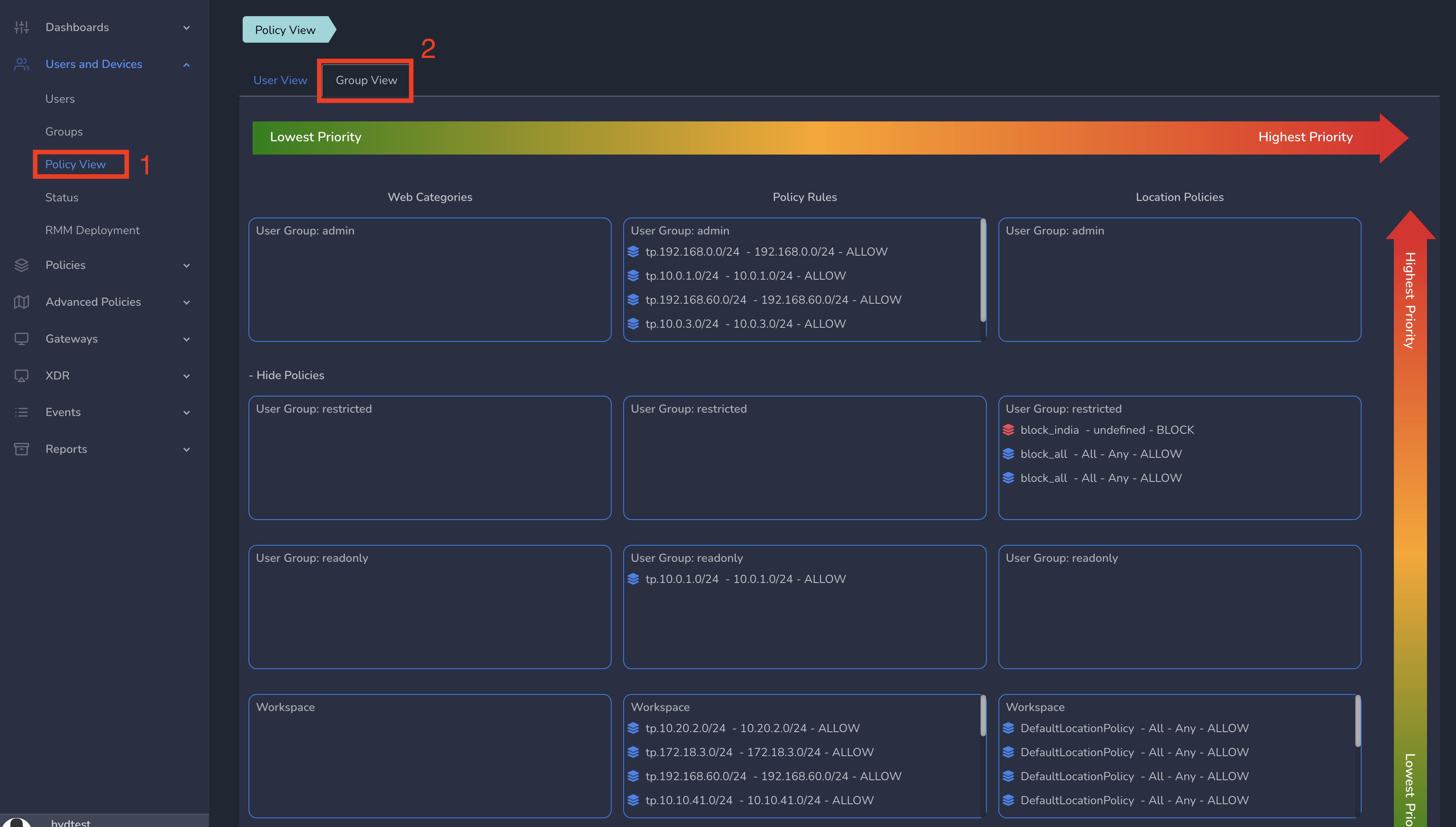
Exium provides Policy Precedence View (Generic Group level view and per user view) which will help admins to get an overview of all the policies placed in different groups and workspace level in the order of precedence.
¶ Policy View
To view Overall policy view, click on Policy View under Users and Devices in left menu bar and select Group View tab as shown below
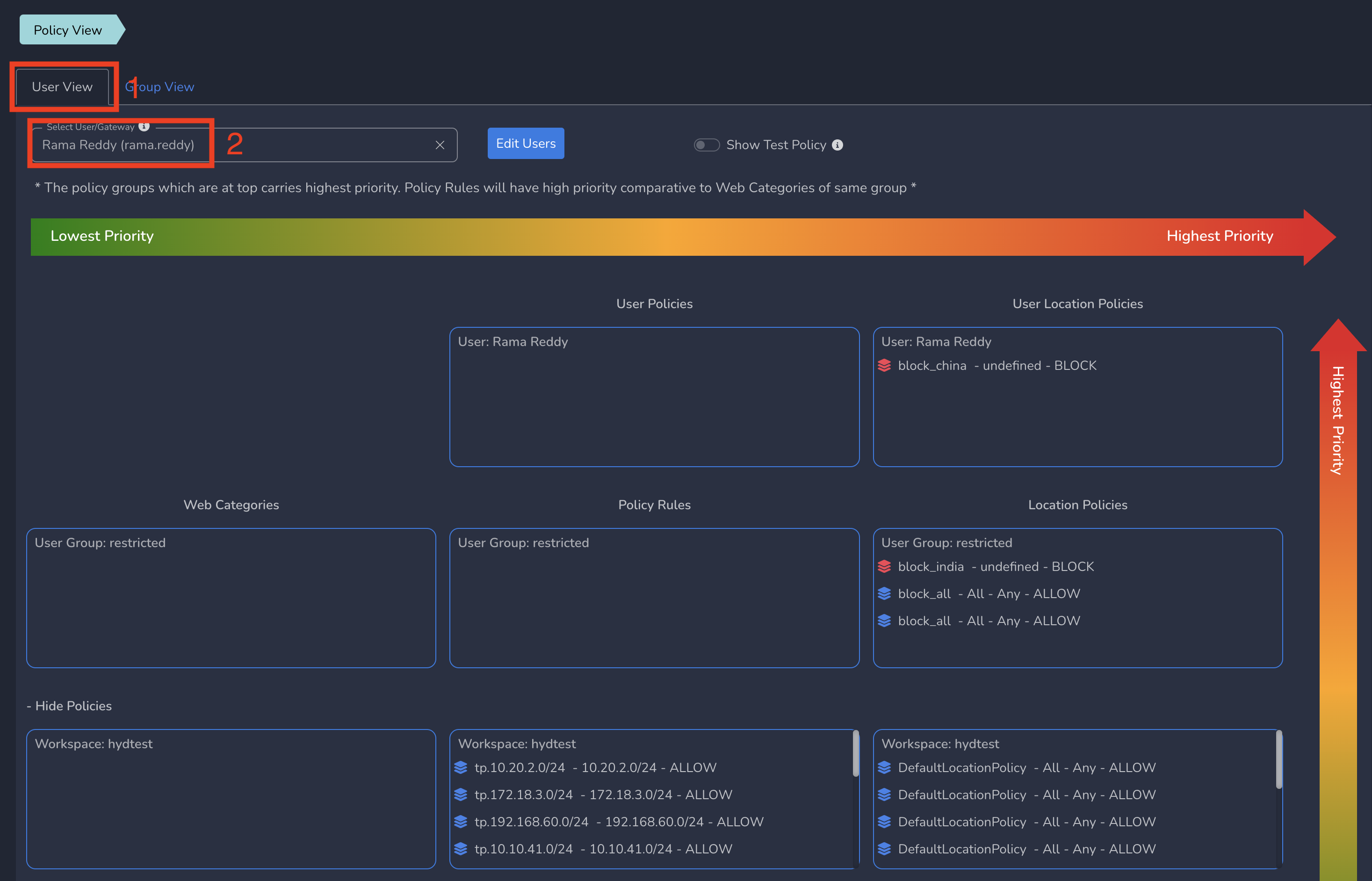
To view User level policy view, click on Policy View under Users and Devices in left menu bar and select User View tab. Select a user from drop down as shown below.
¶ Blocked users and Unblock a user
Users gets blocked when they try to connect to exium from a location which is marked as Blocked. Admins can view If any users are blocked because of Location, investigate further and take required actions. Admins can also unblock the user after all the necessary actions are taken.
¶ Blocked user event
You can view blocked user events under Blocked Threats/Policies as shown below. To view blocked threats, follow below steps.
- Click on Dashboards in the left menu bar and Click on Blocked Threats/Policies.
- Search for Location in Searchbox as shown below.
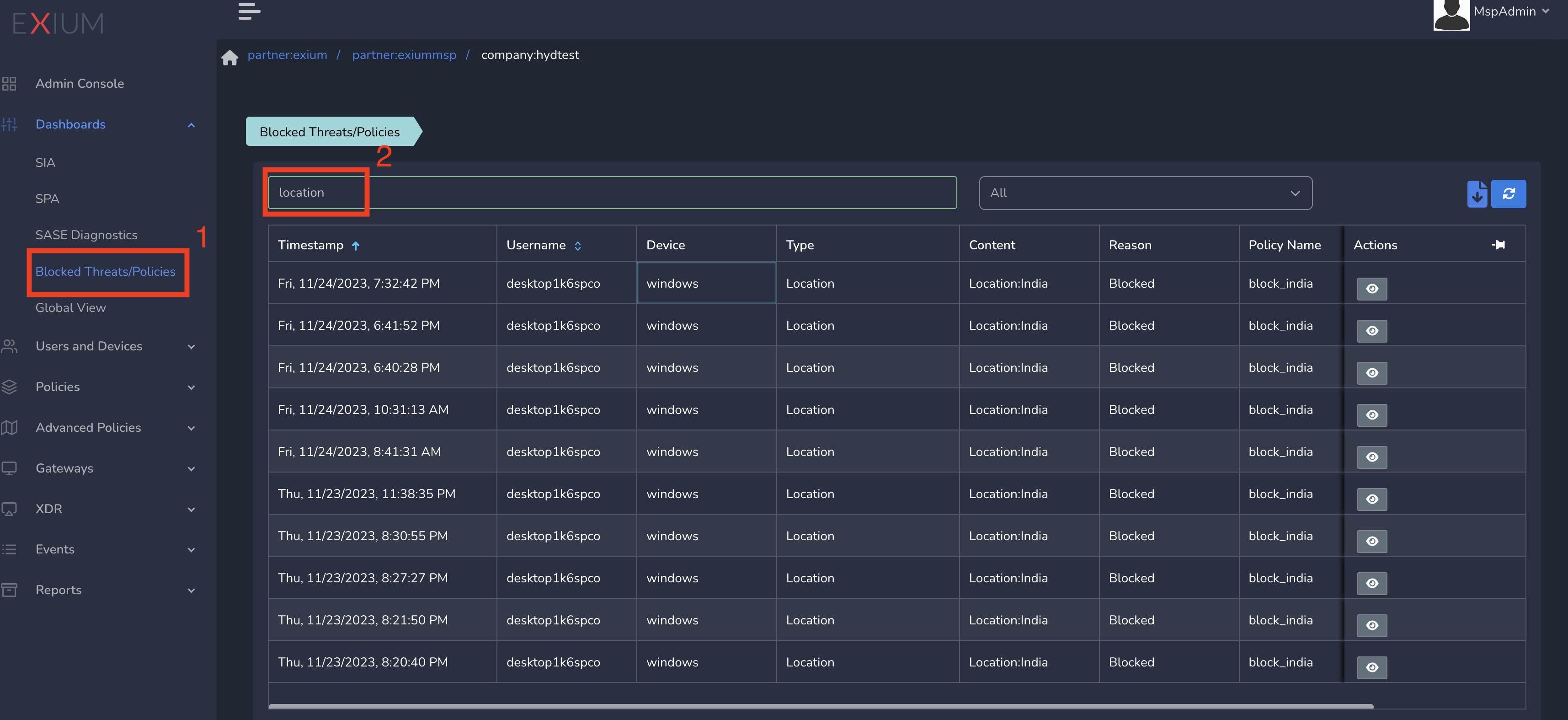
The table shows different users blocked because of Geolocation IP policy along with policy name.
¶ Unblock a user
After required investigation and required actions, You can unblock a user blocked earlier. To unblock a user, Follow below steps.
- Click on Users and Devices in the left menu bar and Click on Users
- Click on Unblock action next to the user who is blocked currently as shown below.
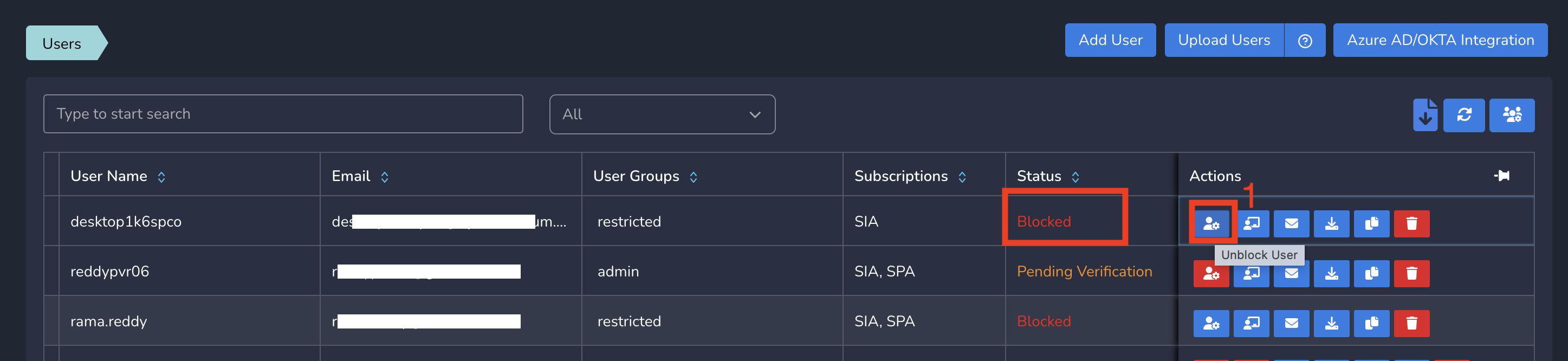
The user gets unblocked immediately, connect to Exium and access all services.
To learn more about implementing SASE for your organization and explore tailored solutions that meet your unique requirements, contact Exium at partners@exium.net for a consultation or demonstration.