¶ Exium's SASE - Geographically-Aware Inbound Traffic Controls
In the dynamic landscape of cybersecurity, securing incoming traffic is as critical as fortifying inbound threats. Exium's Secure Access Service Edge (SASE) solution offers a pioneering approach by implementing ingress traffic controls based on destination geography. This ensures comprehensive protection by allowing IT administrators to configure security policies tailored to the organization's unique needs.
¶ Key Features
|
No |
Key Capabilities of Ingress/ Inbound Traffic Controls |
|---|---|
| 1 |
Geographical Precision
|
| 2 |
Dynamic Policy Adjustments
|
| 3 |
Tailored Security Policies
|
| 4 |
Real-Time Threat Intelligence
|
¶ Benefits
Enhanced Security Posture: Geographically-aware inbound traffic controls bolster your organization's security posture, offering a proactive defense against region-specific cyber threats. This level of granularity ensures a more resilient security infrastructure.
Compliance Adherence: Aligning with various compliance standards is simplified with Exium's SASE. Customizable policies enable organizations to meet regulatory requirements by controlling inbound traffic based on geography, domains, and global IP addresses.
Operational Efficiency: Exium's solution strikes a balance between security and operational efficiency. Tailored policies allow organizations to facilitate legitimate incoming traffic while preventing unauthorized access, ensuring smooth business operations.
User-Friendly Configuration: The user-friendly interface of Exium's SASE solution simplifies the configuration of geographically-aware inbound traffic controls. IT administrators can effortlessly define and manage policies to suit the organization's specific security needs.
¶ Ingress Geolocation IP Policies - Levels
Ingress Geolocation IP policies are a powerful tool for organizations seeking to strengthen their cybersecurity posture, achieve regulatory compliance, and optimize the user experience. By intelligently leveraging geolocation data, businesses can implement targeted and dynamic access controls, contributing to a comprehensive and adaptive security strategy.
Exium enables workspace admins with multiple options to configure Ingress Geolocation IP policies. Ingress Geolocation IP policies are defined in the central admin console and applied in the Exium Cloud CyberMesh platform as shown in the above architecture diagram. Admins can define Ingress Geolocation IP policies to ALLOW/BLOCK some of the countries. Admins can also define default BLOCK from all locations and add ALLOW policy from specific countries. Exium enables workspace admins with multiple options to configure Geolocation IP policies.
|
Geolocation IP Policies |
Workspace level |
Group level |
|---|---|---|
| Policy Definition | Applies to all users in the workspace or in the organization | Applies to all users in the group |
| Geolocation IP Policies Granularity |
√ |
√ |
| Policies override precedence/ order |
Lowest |
Highest |
- Admins can define Ingress Geolocation IP policies and at workspace level which will be applied to all users in the workspace.
- Admins can define Ingress Geolocation IP policies at group level which will be applied to all users in that group.
- Admins can define Ingress Geolocation IP policies and at a user level which will be applied to that particular user.
¶ Override policies
Admins can attach override policies at higher precedence. User group level policies are at the highest precedence, followed by the group level policies and finally workspace level policies are at the lowest precedence.
¶ Configure Ingress/ Inbound Traffic Policy Controls
Exium's SASE solution transforms inbound traffic security by introducing geographically-aware controls, providing a robust defense against cyber threats. With the ability to customize policies based on destination countries, domains, and global IP addresses, organizations can fortify their cybersecurity posture while maintaining operational efficiency.
¶ Workspace level Ingress/InboundGeolocation IP Policies
You can define Ingress/ Inbound Traffic policies at workspace level which will be applied to all users in the workspace. To create Ingress/ Inbound Traffic policies, Follow below steps
- Log into the partner admin console and navigate to the company workspace.
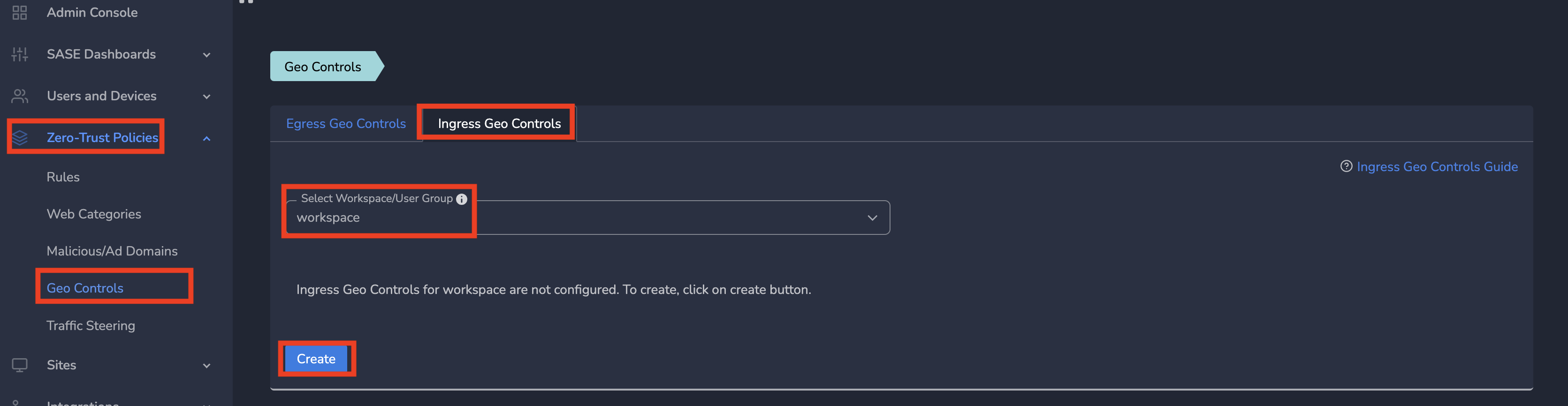
- Click on Zero-Trust Policies and then Click on Geo Controls in the left menu bar.
- On Geo Controls page, Click on Ingress Geo controls tab
- Select workspace from drop down and Click on Create as shown below
- Select all countries you want to BLOCK ingress traffic and Click on Update as shown below
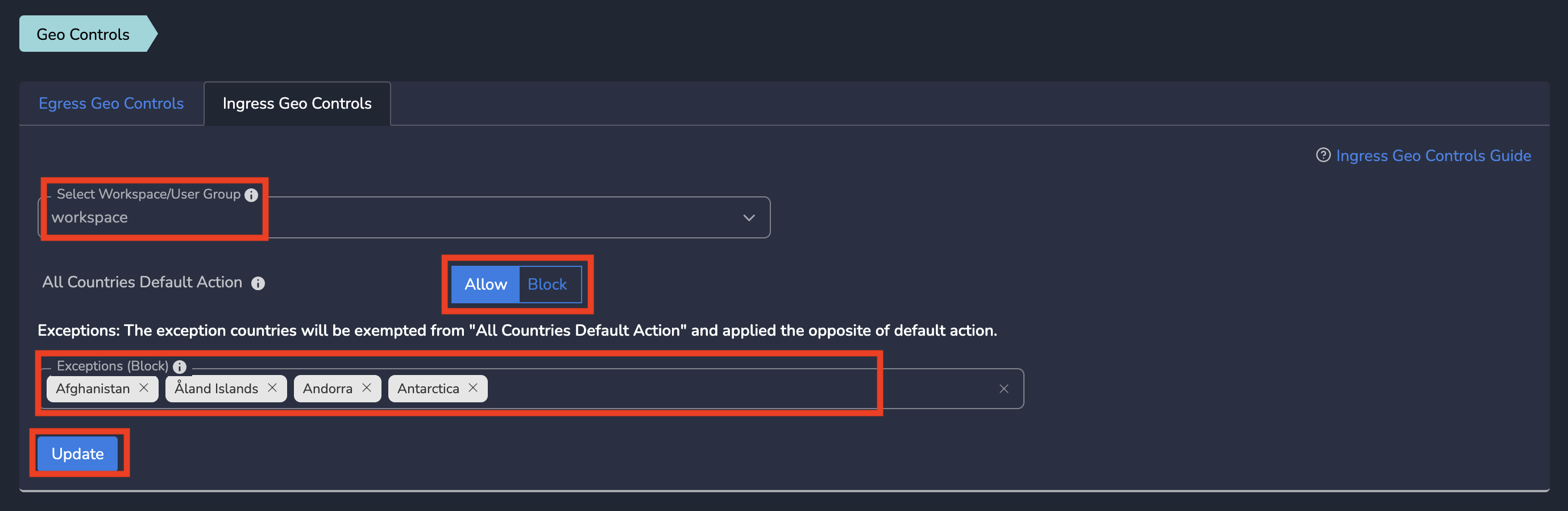
After Submit, Ingress Geo Controls will be applied on the traffic in near realtime and traffic will be bypassed (will not go through tunnel) accordingly.
¶ Group level Ingress/InboundGeolocation IP Policies
You can define Ingress/ Inbound Traffic policies at workspace level which will be applied to all users in the workspace. To create Ingress/ Inbound Traffic policies, Follow below steps
- Log into the partner admin console and navigate to the company workspace.
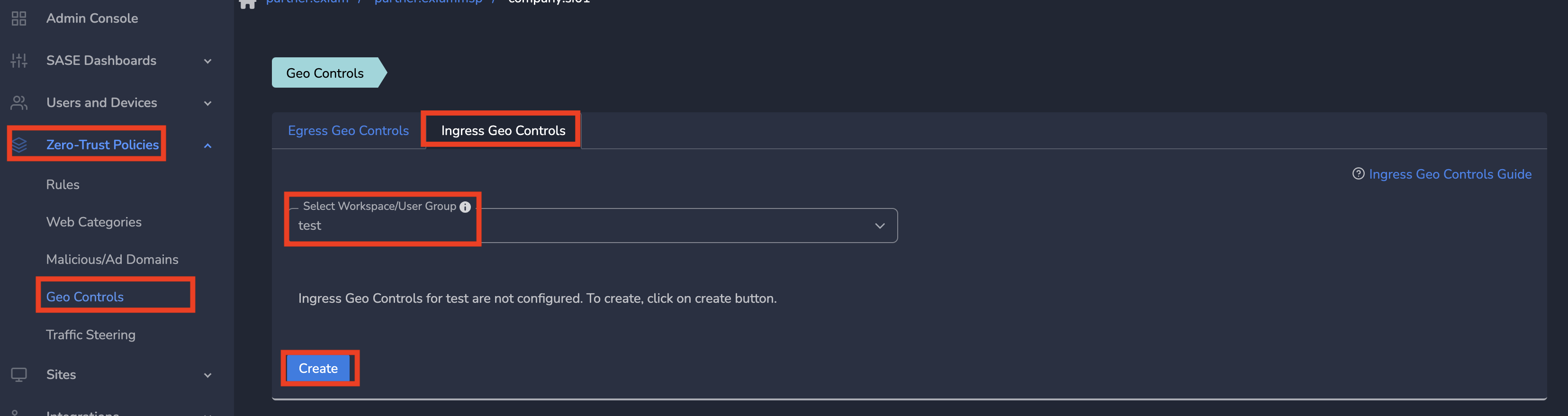
- Click on Zero-Trust Policies and then Click on Geo Controls in the left menu bar.
- On Geo Controls page, Click on Ingress Geo controls tab
- Select a group from drop down and Click on Create as shown below
- Select all countries you want to BLOCK ingress traffic and Click on Update as shown below
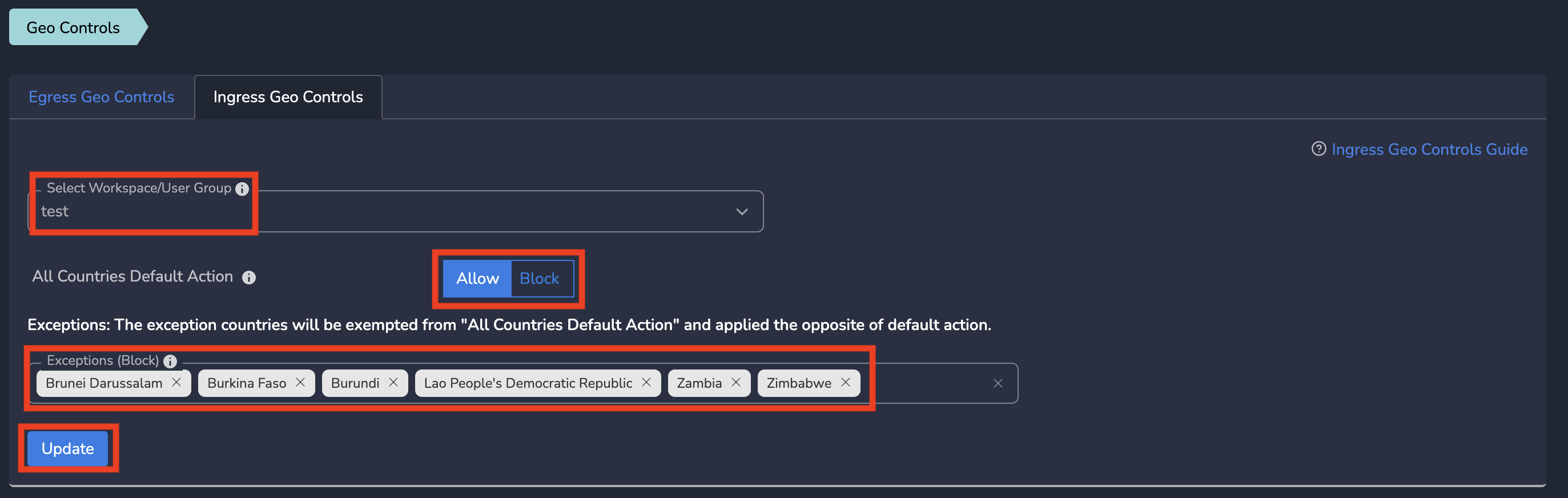
¶ Bypassing the SASE Tunnel at Specific Locations
If you want users in particular locations, like an office, to bypass the SASE tunnel, you can set up a custom ingress policy. This policy should include the public IP addresses of that site.
Here's how it works:
When users are in the office: SASE CyberMesh will detect the specified public IP, and the SASE tunnel will automatically disconnect.
When users are remote (e.g., at home, an airport, coffee shop, or hotel): Their public IP address will differ from the one in your custom policy, so the SASE tunnel will connect automatically.
- Log into the partner admin console and navigate to the company workspace.
- Click on Zero-Trust Policies and then Click on Geo Controls in the left menu bar.
- On Geo Controls page, Click on Ingress Geo controls tab
- Click on Add Custom Ingress as shown below
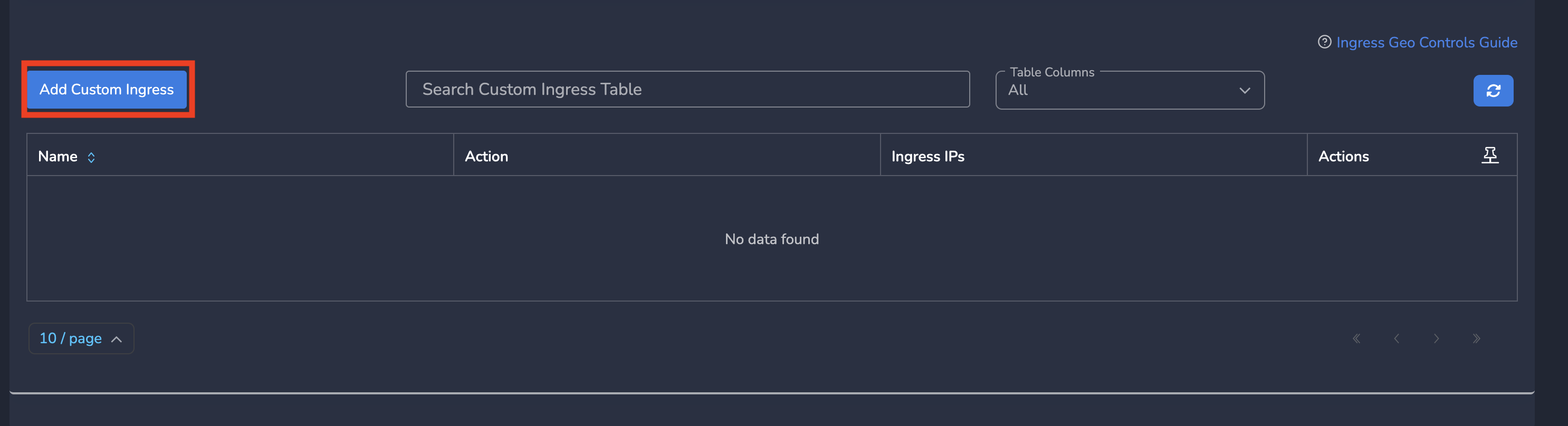
- Enter Name, change Action as Block and Enter public IP(s) as Ingress IPs
- Click on Update as shown below
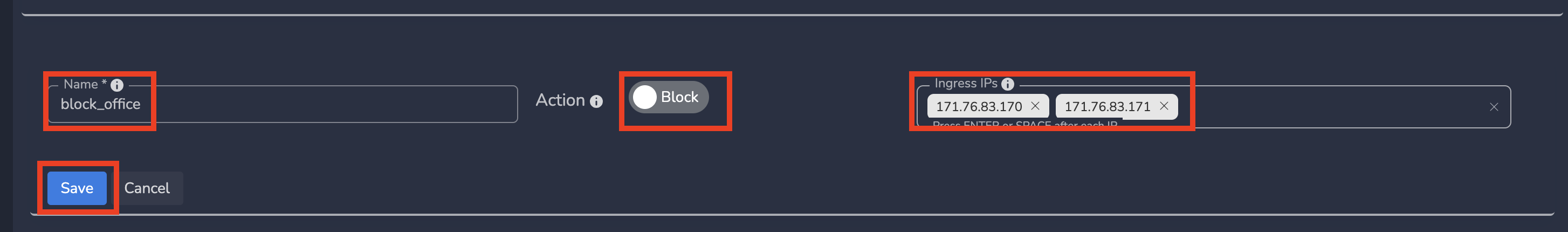
If next time a device tries to connect from this Public IP, traffic from those devices gets bypassed (will not go through tunnel) automatically.
¶ Ingress/ Inbound Traffic Policy Controls - Override Policies
When a user belongs to multiple groups and if the same country is defined in multiple policies attached to multiple groups or workspace, the country rule part of a group which has highest level of precedence will be applied.
We provide some examples below to clarify this. For all the examples, userA is assumed to be a part of a group groupA.
|
Example |
Workspace |
Group |
Policy in Play |
|---|---|---|---|
| 1 | Blocked | Allowed | If China is Blocked at workspace level and if China is Allowed at groupA level, for all users part of the groupA (including userA), can access when they connect to Exium from China. For the users not in groupA, connection to Exium from China will be blocked. |
| 2 | Allowed | Blocked | If China is Allowed at workspace level and if China is Blocked at groupA level, for all users part of the groupA (including userA), connection to Exium from China will be blocked. For the users not in groupA, can access when they connect to Exium from China |
¶ Ingress/ Inbound Traffic Policy Controls - Blocked users and Unblock a user
User sessions get blocked when they try to access any destination IPs belong to the countries which are part of BLOCK list. All the events gets captured part of Blocked Threats/Policies page. Admins can view If any users are blocked because of Location, investigate further and take required actions. Admins can also unblock the user after all the necessary actions are taken.
¶ Blocked user event
You can view blocked user events under Blocked Threats/Policies as shown below. To view blocked threats, follow below steps.
- Click on Dashboards in the left menu bar and Click on Blocked Threats/Policies.
- Search for Location in Searchbox as shown below.
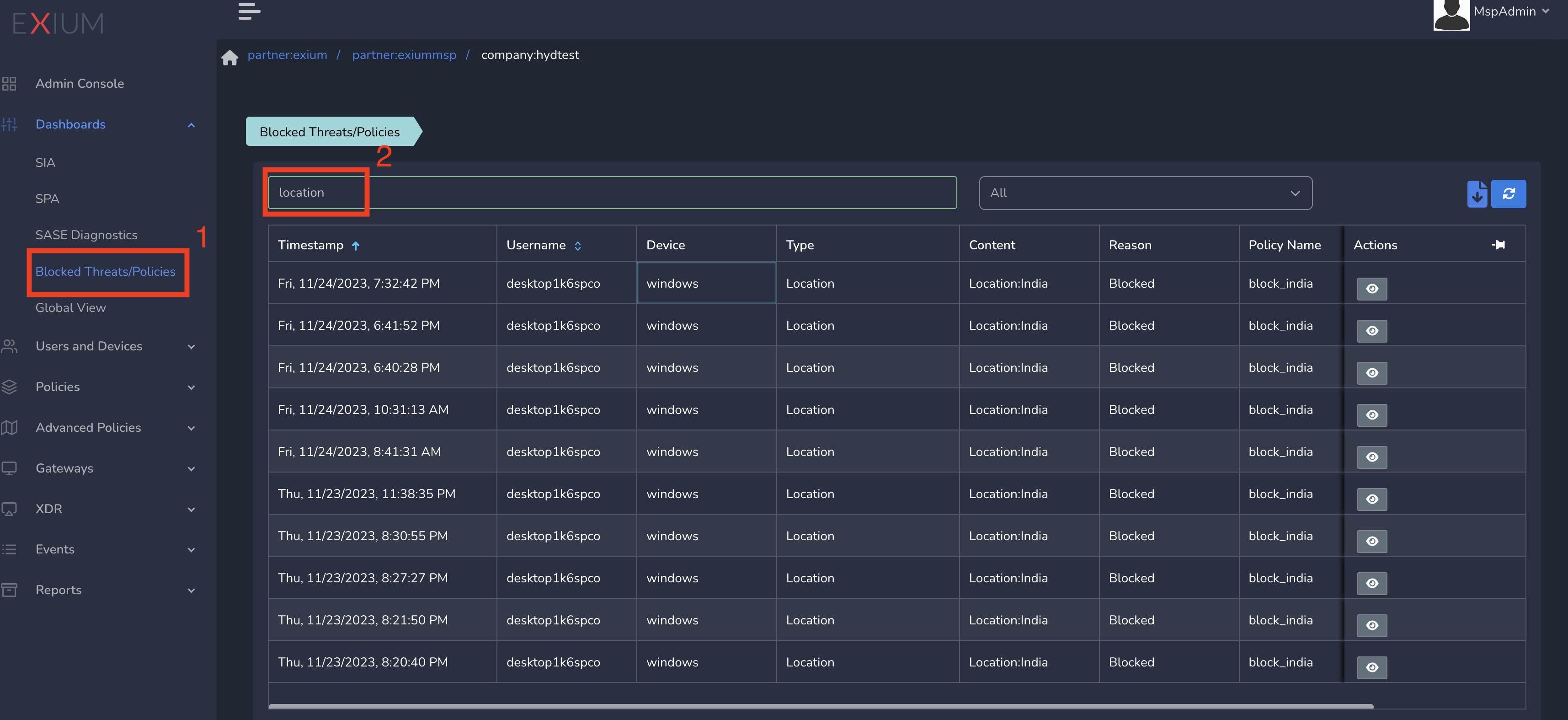
The table shows different users blocked because of Ingress Geolocation IP policy.
¶ Unblock a user
After required investigation and required actions, You can unblock a user blocked earlier. To unblock a user, Follow below steps.
- Click on Users and Devices in the left menu bar and Click on Users
- Click on Unblock action next to the user who is blocked currently as shown below.
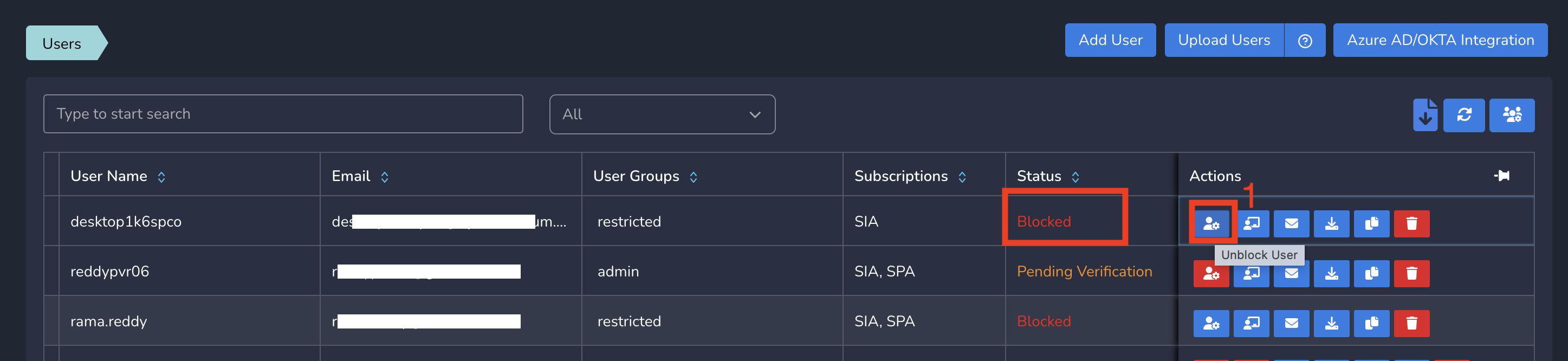
The user gets unblocked immediately, connect to Exium and access all services.
Experience the Exium advantage and take your cybersecurity strategy to new heights. With Exium, you're not just protected – you're empowered. To learn more about implementing SASE for your organization and explore tailored solutions that meet your unique requirements, contact Exium at hello@exium.net for a consultation or demonstration.