Microsoft 365 is being adopted by organizations of all sizes. Microsoft 365 Detection and Response gives users productivity with the tools they need while maintaining visibility and controls to protect sensitive data, prevents loss, and ensure compliance.
¶ The Challenge
Collaboration and communication are key components of productivity in modern organizations. Microsoft 365 provides the necessary environment to facilitate this collaboration and communication, delivering the de facto productivity suite for many organizations of all sizes. Microsoft 365 has been built from the ground-up to accommodate a more mobile workforce, helping to get work done wherever and whenever it happens. However, this flexibility can also facilitate security challenges. Though Microsoft 365 provides native security controls, organizations often find they require a broader approach to security that takes into account enterprise application use and mobile worker mobility.
¶ 365 Microsoft 365 Detection and Response
Microsoft 365 Detection and Response provides a robust security solution, helping MSPs to understand and control risky activities across the Microsoft 365 suite of apps and enable protection of sensitive data and blocking cloud threats. Exium provides deep visibility into activity and data-level usage within every Microsoft 365 app and any other cloud app your organization uses, managed or unmanaged. Across each app, MSPs can observe corporate data violations and potential cyber threats that can endanger the security and compliance of your organization.
¶ COMPLETE VIEW OF MICROSOFT 365
Exium can reveal deep visibility across your Microsoft 365 and all apps in use within your organization. MSPs can parse through each individual Microsoft 365 app or obtain a consolidated view of usage. Microsoft 365 apps such as Exchange, SharePoint, and OneDrive can reveal previously unknown critical activity and data usage, insights that security teams were simply unaware before. With Exium, you can obtain granular visibility into Microsoft 365 activity and the spread of sensitive data within and outside your client organizations.
Exium collects event data from Microsoft 365. Using advanced machine learning, Exium can flag anomalous behavioral activities in user accounts that can signal data exfiltration attempts by cybercriminals that have bypassed your security defenses.
¶ OBTAIN A 360 DEGREE VIEW INTO ALL CLOUD-BASED THREATS
With Exium, you obtain deep visibility and insight into Microsoft 365 app use.
| Threats and Compliance | 360 DEGREE VIEW |
|---|---|
| Insider threats | Detect anomalous behavior by unusual amounts of data uploaded/data, changes in user behavior, and login frequency into account of cloud services |
| Compromised accounts | Evaluate access attempts by identifying suspicious geographic login-access, brute-force attacks, and unusual login patterns |
| Privileged user threats | Identify sudden user privilege escalations, dormant accounts, and unusual system access |
| Malware | Block known malware, discover unknown files, and identify command and control behavior signaling data exfiltration |
| Shadow IT | Discover all managed and unmanaged cloud apps |
| Audit trail | Capture an audit trail of activity for forensic investigations |
| Prevent loss of data | Prevent loss of corporate Microsoft 365 data from use of unmanaged cloud apps or personal Microsoft 365 instances. Detect unauthorized data from being shared externally. |
| Compliance | Stay compliant with PCI, HIPAA, GDPR, and other regulations |
¶ Instructions for Integrating Microsoft 365 with Exium
Follow these steps to integrate Microsoft 365 with Exium:
- Ensure that Audit logging is enabled for your Microsoft 365 organization.
- Navigate to the Microsoft Entra admin center and go to Identity > Applications > App registrations. For detailed guidance, refer to the article on registering an application in the Microsoft Azure portal for authentication with the Microsoft identity platform endpoint.
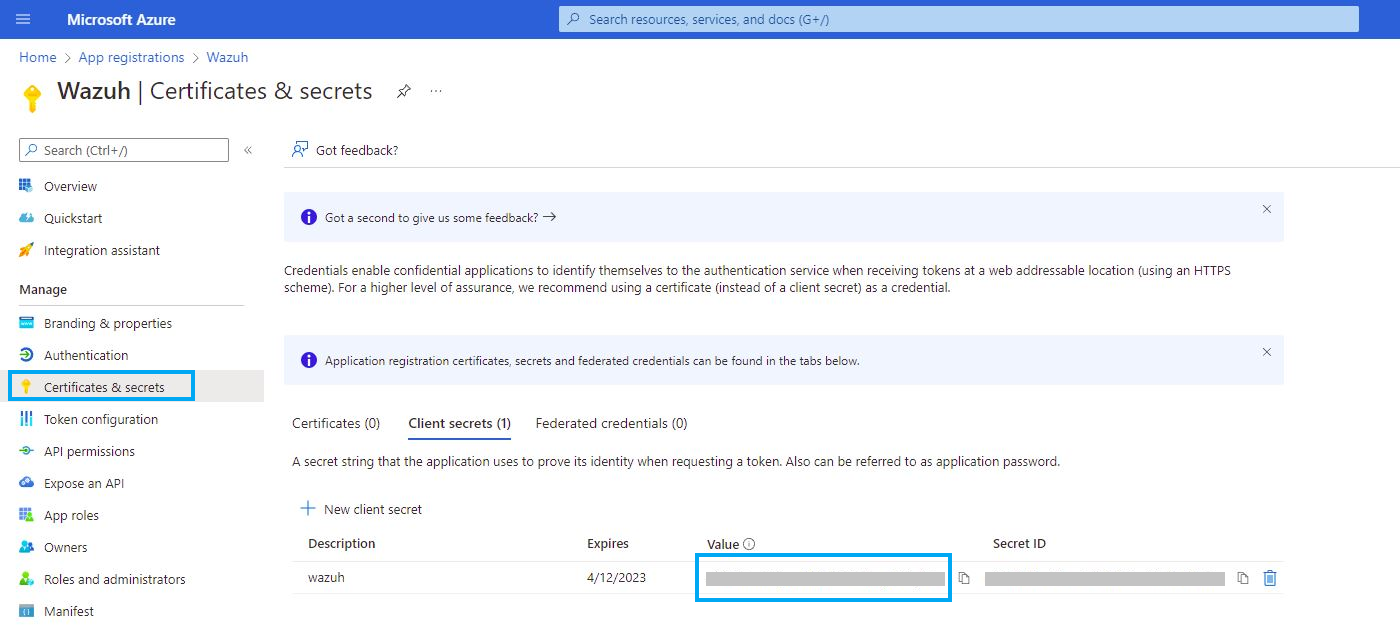
- After registering a new application, retrieve the client ID and tenant ID. Refer to the screenshot provided for assistance.
- Create a new password for the application, then Copy and save the value of the secret under the Client secrets section. This will serve as the client_secret for subsequent steps.
Note
Make sure you write it down because the web interface won’t let you copy it afterward.
Perform the following steps to configure the application permissions:
- Navigate to the API permissions menu and choose Add a permission.
- Select the Office 365 Management APIs and click on Application permissions.
- Add the following permissions under the ActivityFeed group:
ActivityFeed.Read: Read activity data for your organization.ActivityFeed.ReadDlp: Read DLP policy events including detected sensitive data.- Ensure the API permissions Type for these permissions is set to “Application” and not “Delegated,” as illustrated in the screenshot.
- Click on the Add permissions button.
Note
Admin consent is required for API permission changes.
¶ M365 SaaS Configuration in Exium
After registering your application on the Azure portal, proceed with the following steps:
- Go to the MSP admin console and click on the 'Companies' tab.
- Select the desired company name or directly navigate to the Customer/ Client Workspace Sign In.
- Click on XDR and then select “M365,” as illustrated in the screenshot.
- Enter the required information, including your client ID, tenant ID, and client_secret.
- Click “Update.”
¶ Accessing M365 Dashboards
To view M365 logs and dashboards, follow the steps below. For more details, refer to the section titled "Unlocking the XDR Platform."
- Click on XDR and then select “Login” as shown in the screenshot.
- Note your login name (workspace name) and copy the password.
- Click on the icon under Actions to open the dashboards.
- Log in using your username (login name is the same as the workspace name) and the copied password.
Once the dashboard is displayed, click on the Office 365 card.
This will open a range of graphs, as depicted in the screenshot.
Select “Events” to view detailed M365 security and audit events, along with logs activity, as illustrated in the screenshot.
To learn more about implementing SASE and XDR for your organization and explore tailored solutions that meet your unique requirements, contact Exium at partners@exium.net for a consultation or demonstration. If you are ready to get started, check out our testing and onboarding process.