¶ Introduction
Users are central to a SASE deployment, as security policies are directly applied to them or their devices. Administrators have multiple options for securing user access, allowing them to set default service access for all users as:
- Secure Internet Access (SIA) only
- Secure Private Access (SPA) only
- Both SIA and SPA
These default settings apply to all newly created users when integrated through identity providers (IDP), Remote Monitoring and Management (RMM) tools, or CSV file uploads. Admins also have the flexibility to change service settings for one or all existing users/devices.
¶ Important Notes:
- At any given time, both SIA and SPA services cannot be disabled for a user. At least one service must remain active.
- The SPA service cannot be disabled for a user if that user is part of a group that has Trustpath attached.
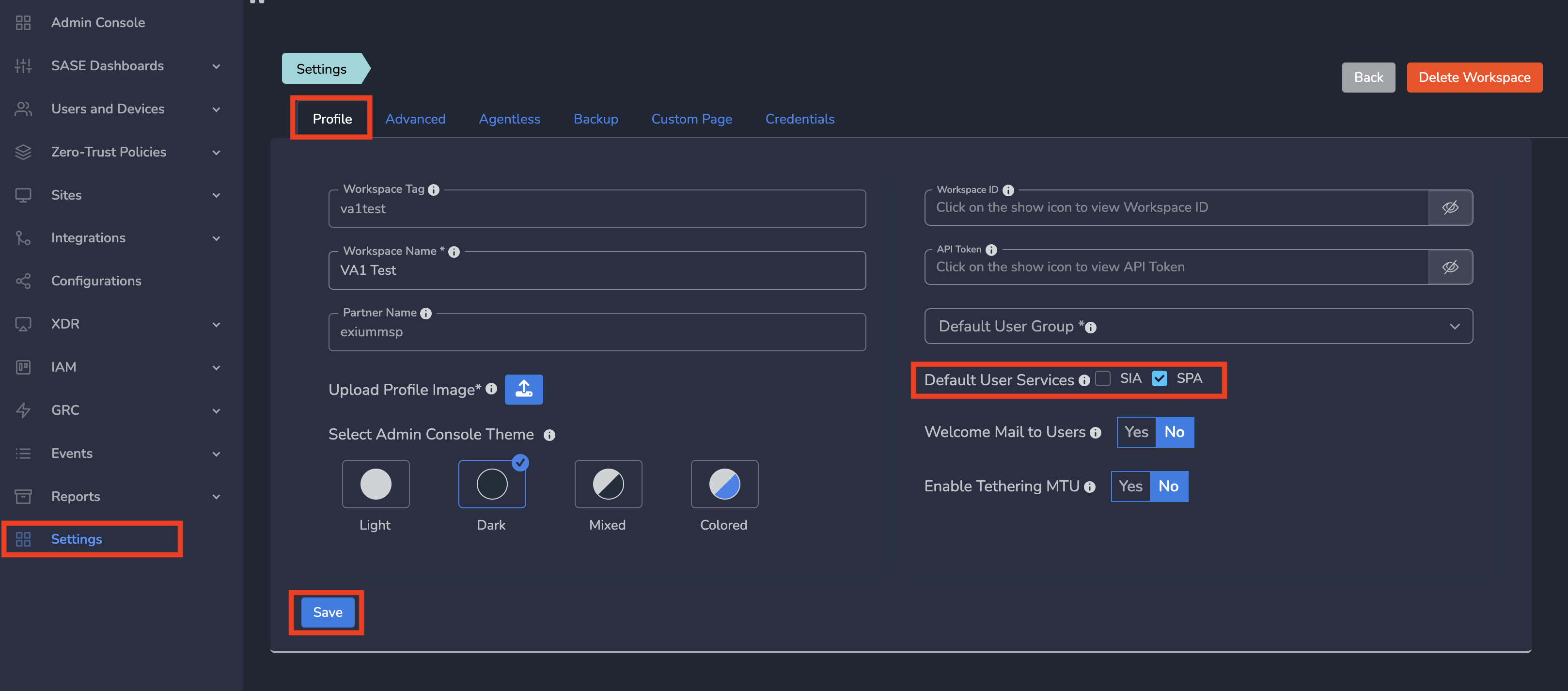
¶ Default Setting for New Users
You can set default configurations as SIA, SPA, or both, which will apply to all newly created users in the workspace:
- Log into the partner admin console and navigate to the company workspace.
- Click on Settings in the left menu bar, then select the Profile tab.
- Set the Default User Services to SIA, SPA, or both.
- Click on Save.
When users are created via IDP (such as Azure AD, Okta, or JumpCloud), RMM, or CSV uploads, they are automatically assigned these default services.
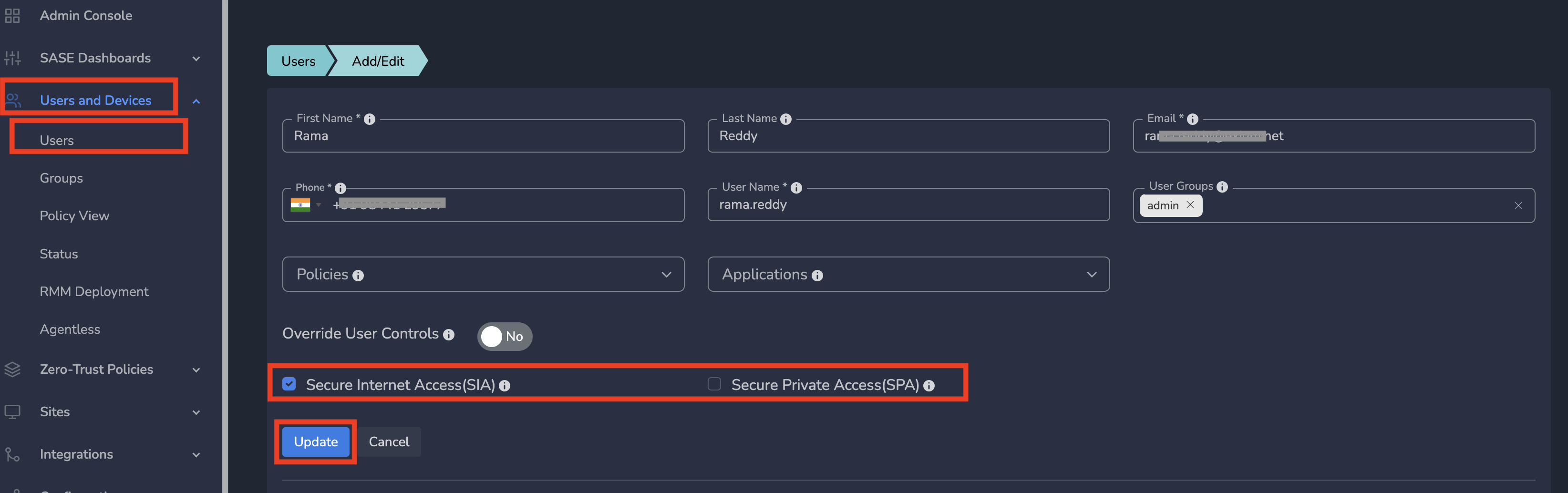
¶ Change Settings for one User
To change the services for existing user, you can modify the settings to either SIA, SPA, or both, which will override the workspace-level default settings for that user
- Log into the partner admin console and navigate to the company workspace.
- Click on Users and Devices in the left menu bar, then select Users.
- Select a username.
- On the Edit User form, adjust the settings to enable Secure Internet Access (SIA), Secure Private Access (SPA), or both.
- Click on Update.
By following these steps, you can ensure that SIA, SPA, or both services are properly configured for your users.
User automatically configured according to changed service setting.
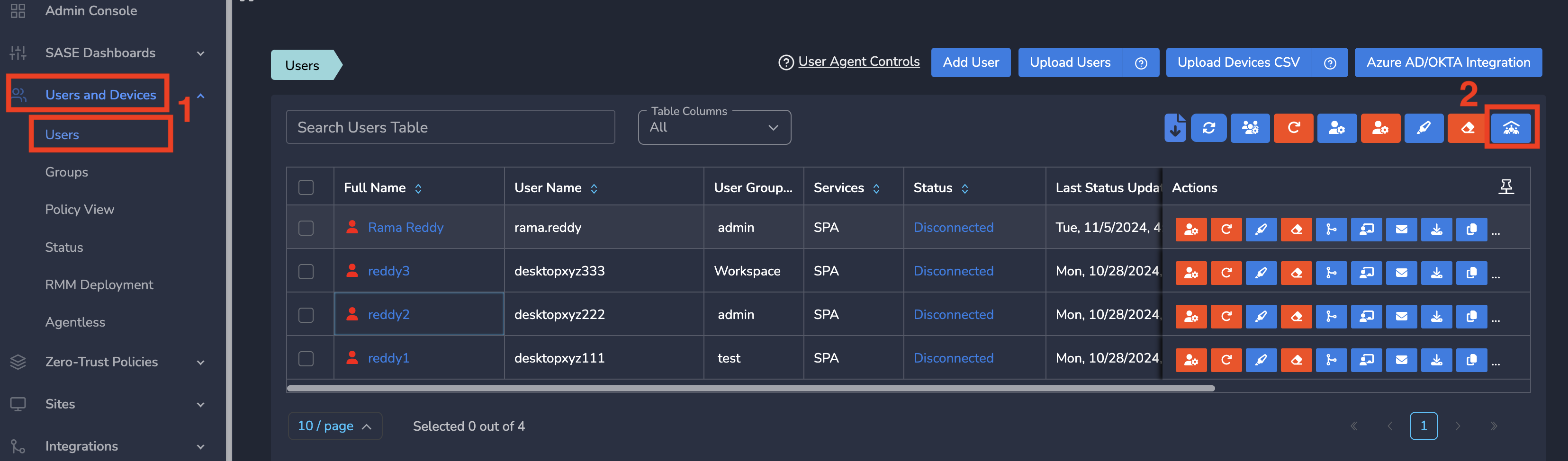
¶ Change Settings for all Users
To change the services for all existing users, you can either enable/disable SIA/SPA, which will override the workspace-level default settings for all users.
- Log into the partner admin console and navigate to the company workspace.
- Click on Users and Devices in the left menu bar, then select Users.
- Click on Enable/Disable SIA/SPA as shown below
- Select an option from drop down as shown below
- Click on Submit
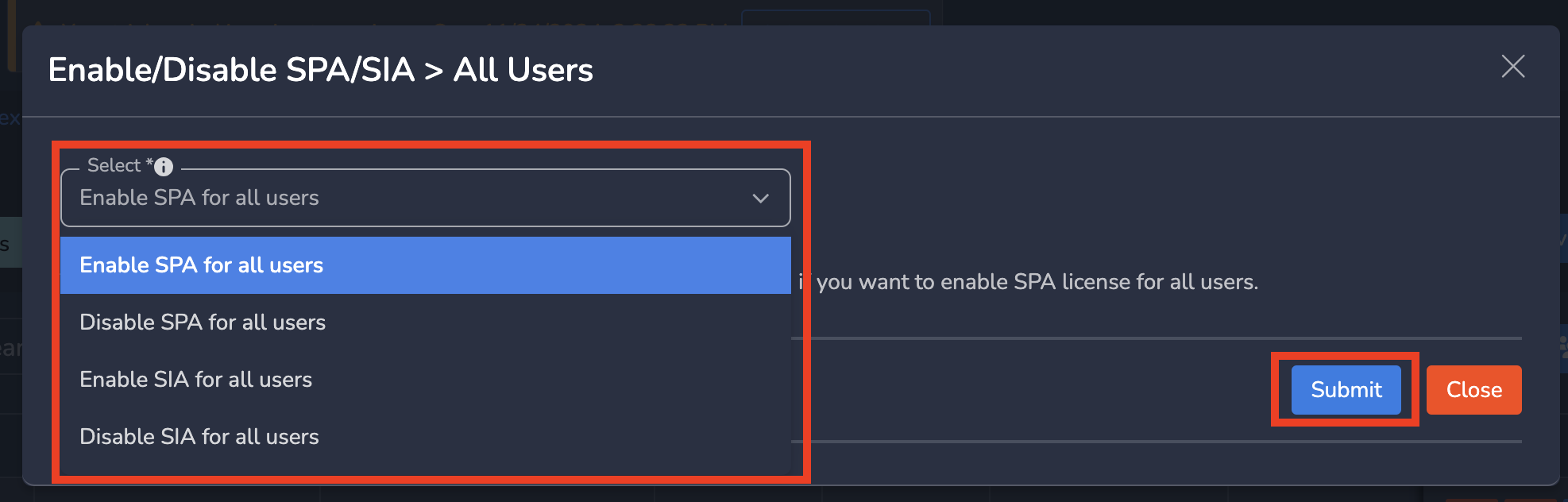
User automatically configured according to changed service setting.
By following these steps, you can ensure that SIA, SPA, or both services are properly configured for your users.
To learn more about implementing SASE, XDR, IAM/ MFA, and GRC for your organization and explore tailored solutions that meet your unique requirements, contact Exium at partners@exium.net for a consultation or demonstration. If you are ready to get started, check out our testing and onboarding process.